Category: Office 365
-
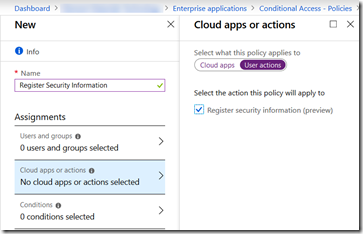
Register For Azure AD MFA From On-Premises Or Known Networks Only
A long request within Azure AD/Office 365 has been the request to be able to register your security info from a known location or only on certain other conditions. Well it looks like this has appeared in Azure AD in the last few days!! Its visible under Azure AD > Conditional Access > New/Existing Policy…
-
Read Only And Document Download Restrictions in SharePoint Online
Both SharePoint Online (including OneDrive for Business) and Exchange Online allow a read only mode to be implemented based on certain user or device or network conditions. For these settings in Exchange Online see my other post at https://c7solutions.com/2018/12/read-only-and-attachment-download-restrictions-in-exchange-online. When this is enabled documents can be viewed in the browser only and not downloaded. So…
-
![Save Time! Have All Your Meetings End Early [or start late]](https://c7solutions.com/wp-content/uploads/2019/04/image_thumb-1.png)
Save Time! Have All Your Meetings End Early [or start late]
Updated April 22nd 2021 with new global default settings I am sure you have been in a meeting, where the meeting end time rolls around and there is a knock at the door from the people who want the meeting room now, as their meeting time has started and yours has finished. What if you…
-
Convert Office 365 Group to Microsoft Team Totally Failing
This one has been annoying me for a while – I had an Office 365 Group that I created many years ago in Office 365 that I cannot convert to a Microsoft Team. This is what I see in Teams to do this process. First, click “Create a team” Followed by “Create a team from…
-
Public Folder Sync–Duplicate Name Error
I came across this error with a client today and did not find it documented anywhere – so here it is! When running the Public Folder sync script Sync-ModernMailPublicFolders.ps1 which is part of the process of preparing your Exchange Online environment for a public folder migration, you see the following error message: UpdateMailEnabledPublicFolder : Active…
-

Configuring Multi Factor Authentication For Office 365
Given that Office 365 is a user service, the enabling of multi-factor authentication is very much as admin driven action – that is the administrators decide that the users should have it, or that it is is configured via Conditional Access when limiting the login for the user to certain applications and locations. For a…
-
SSL Inspection and Office 365
Lots of cloud endpoint URL’s break service flow if you enable SSL Inspection on the network devices between your client and the service. My most recent example of this Enterprise State Routing in Windows 10. Microsoft have a list of URLs for the endpoints to their service, where they are categorised as Default, Allow or…
-
Improving Password Security In the Cloud and On-Premises
Passwords are well known to be generally insecure the way users create them. They don’t like “complex” passwords such as p9Y8Li!uk%al and so if they are forced to create a “complex” password due to a policy in say Active Directory, or because their password has expired and they need to generate a new one, they…
-
Azure Information Protection and SSL Inspection
I came across this issue the other day, so thought I would add it to my blog. We were trying to get Azure Information Protection operating in a client, and all we could see when checking the download of the templates in File > Info inside an Office application was the following: The sequence of…
-
Customizing ADFS To Match Azure AD Centered User Experience
Back in December 2017 the User Experience (UX) for Azure AD login changed to a centered (or centred, depending upon where in the world you speak English) login page with pagination. Pagination is where you enter the username on one screen and the password on the next. This was covered in new Azure Active Directory…
-
Exchange Online Migration Batches–How Long Do They Exist For
When you create a migration batch in Exchange Online, the default setting for a migration is to start the batch immediately and complete manually. So how long can you leave this batch before you need to complete it? As you can see from the below screenshot, the migration batch here was created on Feb 19th,…
-
Office 365 Retention Policies and Hybrid Public Folders
If you create an Office 365 Retention Policy (in the Security and Compliance Center) that applies to all Exchange Online content then you might find that after the retention policy has been deployed (a day or so later usually) that the policy is in error and there is a message at the top of the…
-
Journal Rule Testing In Exchange Online
I came across two interesting oddities in journaling in Exchange Online in the last few weeks that I noticed where not really mentioned anyway (or anywhere I could find that is). The first involces routing of journal reports and the second the selection of the journal target. The journal report, that is the message that…
-
Duplicate Exchange Online and Exchange Server Mailboxes
With a hybrid Exchange Online deployment, where you have Exchange Server on-premises and Exchange Online configured in the cloud, and utilising AADConnect to synchronize the directories, you should never find that a synced user object is configured as both a mailbox in Exchange Online and a mailbox on-premises. When Active Directory is synced to Azure…
-
Enable Report Message Add-In For Office 365
There is a new add-in available for Outlook and OWA in Office 365 that can simplify spam and phishing reporting to Microsoft for content in your mailbox. I recommend rolling this add-in out to everyone in your Office 365 tenant and for Office 365 consultants to add this as part of the default steps in…
-
Office 365 Advance Threat Protection Attachment Preview
It is now possible to preview attachments that Advanced Threat Protection (ATP) is currently in the process of checking. This was enabled on my tenant recently and so will come to all tenants soon. It was mentioned at Microsoft Ignite 2017. It looks like this. You get the email with the standard ATP attachment saying…
-
Office 365 and ACDC
The best connectivity to Office 365 is achieved with local internet breakout and local DNS egress. This means things like each branch office should connect directly to the internet and not via the Head Office and then to the internet and that DNS lookups are done local as well. The reason for DNS lookups is…
-
Azure AD SSO and Disabled Computer Accounts
When you set up Azure AD SSO, the Azure AD Connect application creates a computer account called AZUREADSSOACC. Do not disable this account, or SSO stops working. I’ve had a few clients in the past week disable this when generally disabling all the computer accounts that have not logged in for X days. Therefore if…
-
On-Premises Public Folders, Exchange Online, And Multiple Forests
Update: October 2018. Microsoft have added support to hide public folders in Exchange Online. Now rather than the below post from me, you can set a users mailbox to see public folders or not as required and then enable the global setting to turn on controlled access to public folders. For more see https://techcommunity.microsoft.com/t5/exchange-team-blog/announcing-support-for-controlled-connections-to-public-folders/ba-p/608591 …