Category: Outlook
-

Outlook Reactions – Unsubscribe and Resubscribe
You can “answer” and email in Outlook with a emoji, called a reaction. If you get a reaction in response to a message you will see the reaction in the message, via a notification on the “bell” icon on the top of the Outlook desktop window and in other places, and importantly for this blog…
-

Troubleshooting AutoDetect
AutoDetect is like an “AutoDiscover of AutoDiscovers”. Exchange Online and Exchange Server administrators know the delights of AutoDiscover, which is a web service to tell the client where the mailbox is located (to return the endpoints and protocols that email is read from by the client). But AutoDiscover only works for Exchange based services (unless…
-

Fixing the Display of Voicemail In Outlook
Once upon a time voicemail in Office 365 was done in Exchange Online Unified Messaging, but that was retired early 2020. Voicemail is now provided by a service known as Cloud Voicemail but Outlook did not keep up to date if you have a newly created tenant and now when voicemail arrives in Outlook it…
-

Microsoft 365 – How To Enable A Progressive Web Application
A Progressive Web Application (PWA) is an application that runs in a website which you can separately have an icon for on your desktop (Windows, Chromebook, Raspberry PI, Linux, Android and other operating systems). This icon can be pinned to the Start Menu (or equivalent) and starting it opens the web application in a separate…
-
[New] External Email Notification in Exchange Online
This is a new feature released in March 2021 that adds support in Outlook (Mac, OWA, Mobile) for the display of the external status of the sender – note at the time of writing it does not add this feature to Outlook for the PC. This should be used to replace the way this has…
-
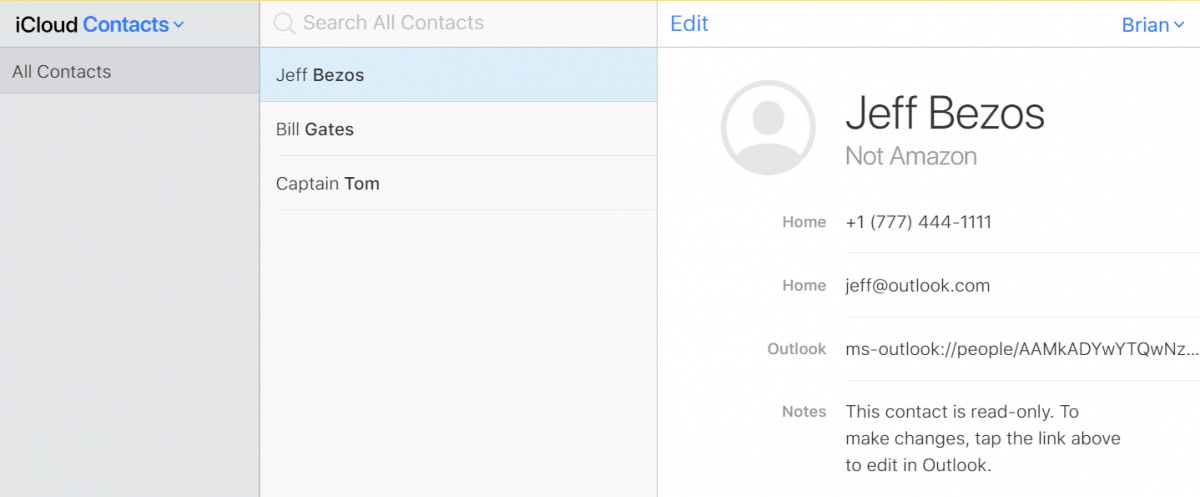
iOS and Outlook Mobile and Duplicate Contacts
Of the back of a few conversations recently on having duplicate contacts in the iOS platform because of syncing via multiple different routes or devices I decided to try to reproduce the issues and see what I could work out. I looked on my test iPhone to see if I could see any duplicates and…
-
Deploying Zoom Add-In To All Outlook Users
With the sudden change in working practices, a (large) number of companies has start to use Zoom as their video conferencing software. Though this software is not from Microsoft, that does not stop an Office 365 or Exchange Server administrator helping their users out in terms of scheduling Zoom meetings via an add-in in Outlook.…
-
How to Use Set-Place to Configure Your Meeting Rooms
Or Making Your Office 365 Meeting Rooms Accessible or How Wheelchair Users Can Find The Best Meeting Rooms In Your Organization etc. – there are many different titles I can think of for this blog post. They are all to do with setting useful properties against your meeting rooms so that your users can find…
-
![Save Time! Have All Your Meetings End Early [or start late]](https://c7solutions.com/wp-content/uploads/2019/04/image_thumb-1.png)
Save Time! Have All Your Meetings End Early [or start late]
Updated April 22nd 2021 with new global default settings I am sure you have been in a meeting, where the meeting end time rolls around and there is a knock at the door from the people who want the meeting room now, as their meeting time has started and yours has finished. What if you…
-

Conversation Red Number in Skype For Business That Won’t Go Away
I have had this issue for ages, but could not find any answer for it on the internet that did not involve resetting Skype for Business or other complex stuff when in fact the answer is so easy it hurts! Finding it was one of those Duh! moments. You have this: Skype for Business shows…
-
OWA and Conditional Access: Inconsistent Error Reports
Here is a good error message. Its good, because I could not find any references to it on Google and the fault was nothing to do with the error message: The error says “something went wrong” and “Ref A: a long string of Hex Ref B: AMSEDGE0319 Ref C: Date Time”. The server name in…
-
Bypassing Focused Inbox and Clutter Folders
For the last few years Exchange Online mailboxes have been processed by a service call Clutter, which moved the less important emails, or indeed the clutter, to a dedicated folder. This is now in the processes of being replaced by the Focused Inbox, which is client version dependant and is all based on views on…
-
The Case of the Disappearing Folders
Here is a issue I have come across at one of my current clients – you create a folder in Outlook 2013 when in the “Mail” view (showing only mail folders – your typical default view) and the folder does not get created. For example, in the below picture the user is in the middle…
-
Continuing Adventures in AD FS Claims Rules
Updated 20th April 2017 There is an excellent article at http://blogs.technet.com/b/askds/archive/2012/06/26/an-adfs-claims-rules-adventure.aspx which discusses the use of Claims Rules in AD FS to limit some of the functionality of Office 365 to specific network locations, such as being only allowed to use Outlook when on the company LAN or VPN or to selected groups of users.…
-
Errors in Moving Exchange Archive Mailboxes to Office 365
I was trying to move an Archive mailbox to the Office 365 service from my demo environment the other day when I came across an error I thought I would note down here for completion. I could not find the error elsewhere on the internet An archive mailbox must be enabled before it can be…
-
The New Rights Management Service
This blog is the start of a series of articles I will write over the next few months on how to ensure that your data is encrypted and secured to only the people you want to access it, and only for the level of rights you want to give them. The technology that we will…
-
Message Classifications, Exchange Server, Exchange Online and Outlook
Message Classifications are a way to tag email with a property that describes the purpose of the email, for example “Internal Use Only” might be a classification to tell the recipient of the email that the message should not be forwarded. Classifications are configured by administrators and appear shortly after creation in Outlook Web App,…
-
Unknown Error, Outlook 2003 and Exchange 2010
It’s a well documented issue with Outlook 2003 connecting to Exchange 2010 that means Outlook 2003 is not as responsive in Online mode as it was with legacy versions of Exchange Server (http://support.microsoft.com/kb/2009942). What is less well documented is an odd error message that can appear because of this interaction. Imagine the following scenario. User…
-
Blogger Blogs in Outlook – Incorrect Dates
This has been obvious to me for a while – whenever I viewed this blog in Outlook 2007 via the common RSS feed store, the dates were all incorrect and so new posts appeared at random within the list. I finally found a fix yesterday – the post was based upon ATOM technology and not…