There is a considerable uptick in emails from the default domain in Microsoft 365 tenants. These emails come from senders @ tenant.onmicrosoft.com and are not your tenant. Microsoft recently announced recipient external sender limits to reduce this, as the default is 10,000 recipients per day, but will get an additional restriction of no more than 2000 external recipients per day per mailbox, which will be part of the 10,000 total recipients max.
Meanwhile, you might still be getting spam from other onmicrosoft.com domains. So, can you block it and what will the impact be?
Yes, you can block it with a transport rule and the impact is measurable before you turn on the block with Advanced Hunting, part of Microsoft Defender 365.
Advanced Hunting
In Advanced Hunting, enter the following Kusto query (KQL):
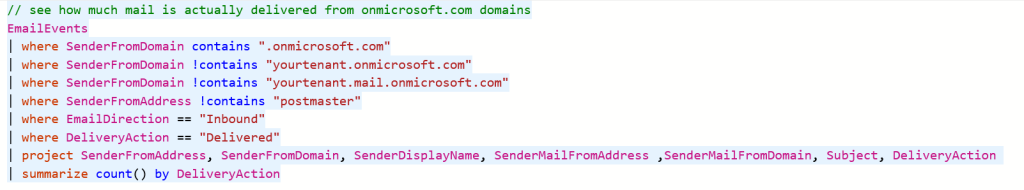
// see how much mail is actually delivered from onmicrosoft.com domains
EmailEvents
| where SenderFromDomain contains ".onmicrosoft.com"
| where SenderFromDomain !contains "yourtenant.onmicrosoft.com"
| where SenderFromDomain !contains "yourtenant.mail.onmicrosoft.com"
| where SenderFromAddress !contains "postmaster"
| where EmailDirection == "Inbound"
| where DeliveryAction == "Delivered"
| project SenderFromAddress, SenderFromDomain, SenderDisplayName, SenderMailFromAddress ,SenderMailFromDomain, Subject, DeliveryAction
This will show you all the emails that were “delivered” (so not counting quarantined or rejected) where the sender’s domain is *.onmicrosoft.com.
To avoid detecting and therefore later quarantining your own emails, we do not look for yourtenant.onmicrosoft.com or yourtenant.mail.onmicrosoft.com (added to Exchange Online when you set up Hybrid Exchange).
To see your domains, go to the Exchange Online Admin Center at https://admin.exchange.microsoft.com > Mail Flow > Accepted Domains. Take all the domains you have added that end “onmicrosoft.com” and include them in the Advanced Hunting query.
Note, for the query it is “dot onmicrosoft.com” and not just “onmicrosoft.com” otherwise useful services such as Directions On Microsoft (directionsonmicrosoft.com) would also be blocked.
The KQL Advanced Hunting is entered into the Microsoft Defender 365 Portal at https://security.microsoft.com > Hunting > Advanced Hunting. If your licence does not include Defender 365 for email queries you will get an error “‘where’ operator: Failed to resolve table or column expression named ‘EmailEvents’“.
Change the query duration to 7 days and see what you discover. The query exempts bounces from other postmaster@ and your own tenant. You can get a count of hits by adding “| summarize count() by DeliveryAction” as the last line of the query. Without this last line you will see the email data.
Expand the query to 30 days and look for any emails that would be problematic to block, for example bounces or redirects from mailing lists (i.e. anything that has done SRS, the Sender Rewriting Scheme). Compile a list of domains or senders that you need to exempt and then you can create your mail flow rule.
Mail Flow Rule
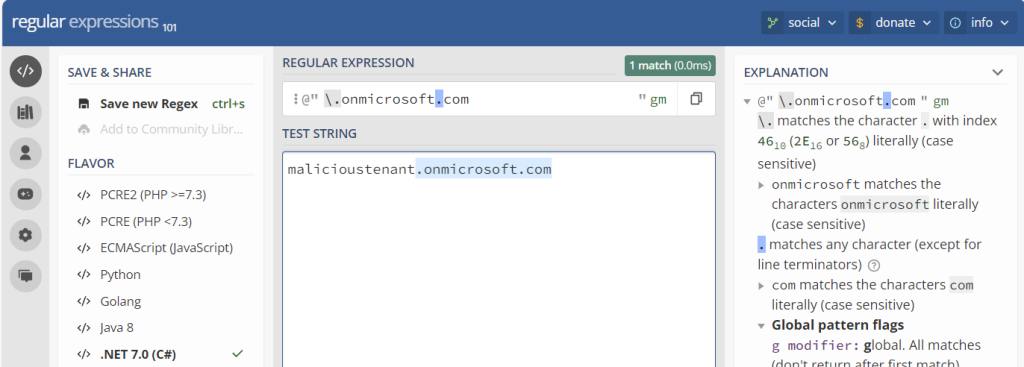
In the Exchange Admin Center (https://admin.exchange.microsoft.com) > Mail Flow > Rules add a new rule called “Quarantine email from onmicrosoft.com senders”. This is based on the rule created by Chris Lehr. Apply the rule if the sender address matches any of these text patterns and enter \.onmicrosoft.com (as above, include the backslash and dot/period at the start). The backslash is an escape character as the dot/period means any character, so “.onmicrosoft.com” would match my directionsonmicrosoft.com example above.
If you customise your regex, always test it out. I recommend https://regex101.com/:
Do the following redirect the message to hosted quarantine and except if the sender address matches any of these text patterns and enter yourtenant.onmicrosoft.com or yourtenant.mail.onmicrosoft.com or mailinglistbounce.com or postmaster (where mailinglistbounce.com is any entry such as a mailing list that was detected in the last 30 days of your query). Most of the hits on this rule that are not spam/phish I have seen to be out of office replies, so I also exclude the message properties where the message type is OOF so that these get delivered and not quarantined.
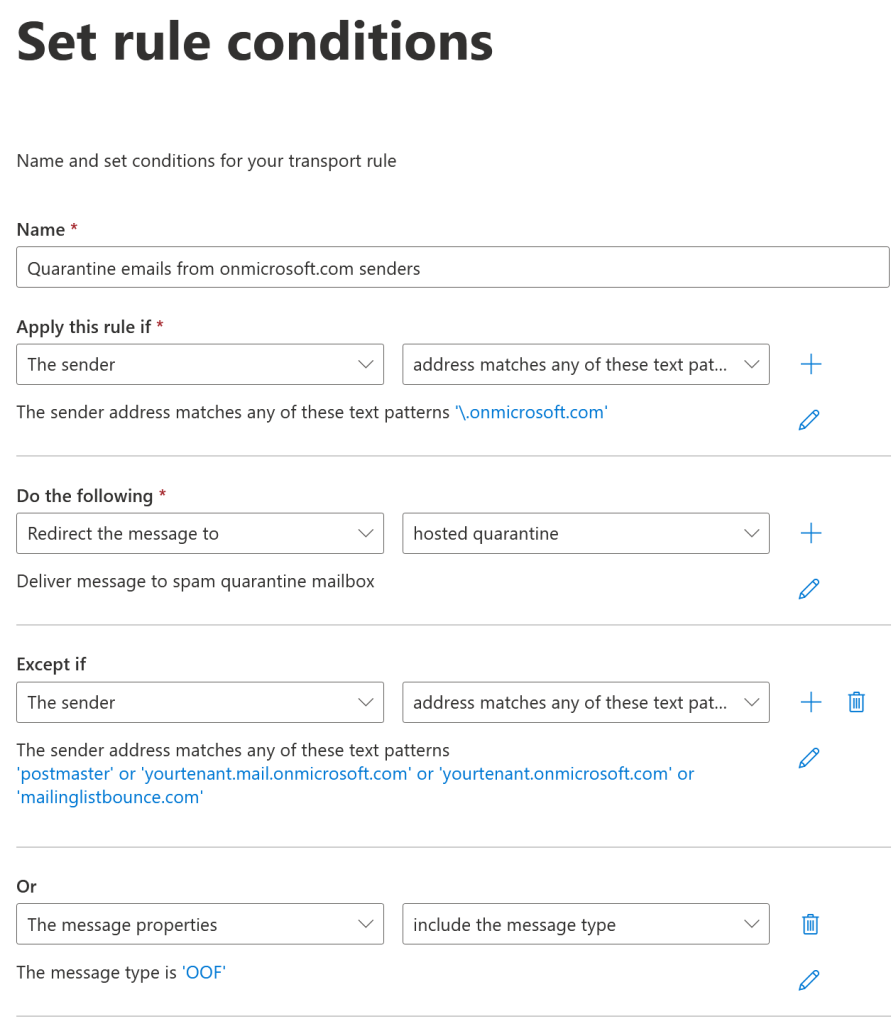
The rule will be created in disabled mode so you need to enable it for it to start working.
If you don’t have Advanced Hunting, then you can add the obvious exceptions of yourtenant and yourtenant.mail and postmaster but would add other exceptions as they appear in the quarantine and you release them. Advanced Hunting lets you get ahead of the game!
Photo by Lum3n: https://www.pexels.com/photo/red-yellow-and-black-bouy-on-body-of-water-during-daytime-190294/

Leave a Reply