Category: Exchange Online Protection
-

Direct Send – What It Is, and What It Isn’t
There are a number of posts online panicking about “Direct Send” and how its the worst thing ever. These appear to have started following Microsoft’s publication of an article on how to turn it off – but lots of the articles get the basic principles wrong and therefore provide poor and inaccurate advice. The blog…
-
Why Is My Microsoft 365 Data In Multiple Regions?
When your Microsoft 365 service is first used data is provisioned in the location best suited to your organization postal address and provided in the M365 Admin Center. If you start other services at later times, those services might be in different locations. Here is an example: The above is found in the Microsoft 365…
-

Implementing High Volume Email with Exchange Online
High Volume Email (HVE) is a new service from Microsoft to allow the sending of up to 100,000 internal emails per day (with a small number external) which is in excess of the current limits of 10,000 per day (depending upon your licence). Here are my initial observations on setting this service up. During preview…
-

Blocking onmicrosoft.com Emails in Exchange Online Protection
There is a considerable uptick in emails from the default domain in Microsoft 365 tenants. These emails come from senders @ tenant.onmicrosoft.com and are not your tenant. Microsoft recently announced recipient external sender limits to reduce this, as the default is 10,000 recipients per day, but will get an additional restriction of no more than…
-

Integrating Microsoft 365 SafeLinks and Mimecast Targeted Threat Protection
If your email protection filter is provided by Mimecast, then you might also have enabled Mimecast Targeted Threat Protection (TTP). TTP, like Microsoft Defender for Office SafeLinks will rewrite the URLs in email messages, but unlike SafeLinks will not rewrite or redirect them in Office documents or Teams chat, channel and meetings. Therefore as both…
-

What Is “mx.microsoft”?
mx.microsoft is the new MX delivery domain for Exchange Online. For years now it has been mail.protection.outlook.com, but this domain will not work with the new DNSSEC extensions that Exchange Online will start to support. When you added a new domain (called a vanity domain) to Microsoft 365, it would show you the MX record…
-

Blocking More Obvious Phish – Attachment Filtering
One relatively easy way to block some categories of phishing email is to block the attachment type that is sent with some of these messages. For example, I have had a few of these recently: Hovering over the attachment I see the filename, and it ends .shtml. This attachment is for server-side HTML (SSI includes…
-

More Frequent Quarantine Notifications in Exchange Online Protection
Available from the end of April 2023 there is now an option to increase the notification interval to end users about items in the quarantine. The Microsoft 365 Quarantine is at https://security.microsoft.com/quarantine and though this is a good link to add corporate intranets, its also a useful one for users to remember and bookmark. Up…
-

Troubleshooting AutoDetect
AutoDetect is like an “AutoDiscover of AutoDiscovers”. Exchange Online and Exchange Server administrators know the delights of AutoDiscover, which is a web service to tell the client where the mailbox is located (to return the endpoints and protocols that email is read from by the client). But AutoDiscover only works for Exchange based services (unless…
-

Improving Exchange Online Email Deliverability Through Third Party Filtering Services – Trusted ARC Sealer
When you receive emails into Exchange Online and you filter the external messages before arrival with a third party filter such as Mimecast, Proofpoint or others, then you can have DMARC failures that result in messages being junked or quarantined in Exchange Online. Trusted ARC Sealer is a feature of Exchange Online to allow you…
-

Finding Existing Plus Addresses
Exchange Online will automatically enable “Plus Addressing” for all tenants from Jan 2022. This change may cause issues if you have existing mailboxes where the SMTP address contains a + sign. That is, directors+managers@contoso.com would be considered a broken email address from Jan 2022 in Exchange Online. So you need to check you have no…
-

Allowing “Phish” Training Emails in Exchange Online
With the introduction of “Secure by Default” in Exchange Online, where you used to add IPs and other settings such as allow-lists to allow your phish training emails to get through to your users this will no longer work, and shortly it will no longer work to bypass the Exchange Online filters using mail flow…
-
550 5.1.8 Access denied, bad outbound sender AS(42003)
“Your message couldn’t be delivered because you weren’t recognized as a valid sender. The most common reason for this is that your email address is suspected of sending spam and it’s no longer allowed to send email. Contact your email admin for assistance.” This is an error you get when your anti-spam “outbound” policy restricts…
-
[New] External Email Notification in Exchange Online
This is a new feature released in March 2021 that adds support in Outlook (Mac, OWA, Mobile) for the display of the external status of the sender – note at the time of writing it does not add this feature to Outlook for the PC. This should be used to replace the way this has…
-
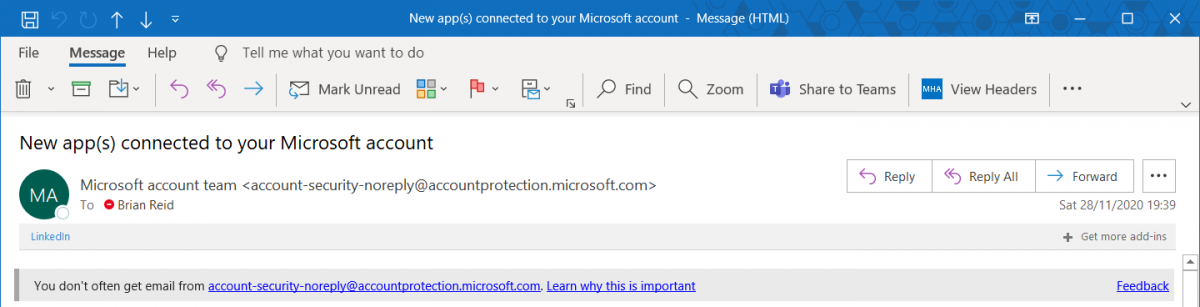
Exchange Online Warning On Receipt Of New Email Sender
Released recently to no fanfare at all, Microsoft now has a SafetyTip that appears if you receive email from a first time recipient. Most often phish emails will come from an address you have never received email from before, and sometimes this email will try to impersonate people you communicate with or are internal to…
-
Enabling Better Mail Flow Security for Exchange Online
At Microsoft Ignite 2020, Microsoft announced support for MTA-STS, or Mail Transfer Agent Strict Transport Security. This is covered in RFC 8461 and it includes making TLS for mail flow to your domains mandatory whereas it is currently down to the decision of the sender. You can publish your SMTP endpoint and offer the STARTTLS…
-
Reporting on MTA-STS Failures
This article is a follow up to the Enabling Better Mail Flow Security for Exchange Online which discusses setting up MTA-STS and in this article we cover the reporting for MTA-STS. To get daily reports from each sending infrastructure to receive reports on MTA-STS you just create a DNS record in the following format: It…
-

Enable EOP Enhanced Filtering for Mimecast Users
Enhanced Filtering is a feature of Exchange Online Protection (EOP) that allows EOP to skip back through the hops the messages has been sent through to work out the original sender. Take for example a message from SenderA.com to RecipientB.com where RecipientB.com uses Mimecast (or another cloud security provider). The MX record for RecipientB.com is…
-
Mail Flow To The Correct Exchange Online Connector
In a multi-forest Exchange Server/Exchange Online (single tenant) configuration, you are likely to have multiple inbound connectors to receive email from the different on-premises environments. There are scenarios where it is important to ensure that the correct connector is used for the inbound message rather than any of your connectors. Here is one such example.…
-
Anonymous Emails Between On-Premises and Exchange Online
When you set up Exchange Hybrid, it should configure your Exchange organizations (both on-premises and cloud) to support the fact that an email from a person in one of the organizations should appear as internal to a recipient in the other organization. In Outlook that means you will see “Display Name” at the top of…
-
Journal Rule Testing In Exchange Online
I came across two interesting oddities in journaling in Exchange Online in the last few weeks that I noticed where not really mentioned anyway (or anywhere I could find that is). The first involces routing of journal reports and the second the selection of the journal target. The journal report, that is the message that…