High Volume Email (HVE) is a new service from Microsoft to allow the sending of up to 100,000 internal emails per day (with a small number external) which is in excess of the current limits of 10,000 per day (depending upon your licence).
Here are my initial observations on setting this service up. During preview this service is free, and I might come back here and update this blog post for the pricing when it is available. Also during preview this is a USA based service only, other locations will be available later.
So what do you need to do. You need to create a HVE dedicated account, then configure any requirements to allow legacy or basic auth to work (that is, Conditional Access rules or Exchange Online Authentication Policies) and then test it out.
So, creating the dedicated HVE account. Note that you cannot convert an existing account and mailbox to a HVE account but need to make a new account with a new email address. If you want to use an existing email address then you need to delete that old account first (or at least change the email address so its not in use for email or login) and then assign the email address to your new HVE account.
To make a HVE dedicated account, visit the Exchange Online Admin Center > Mail Flow > High Volume Email. Click Add an HVE account and fill out the form
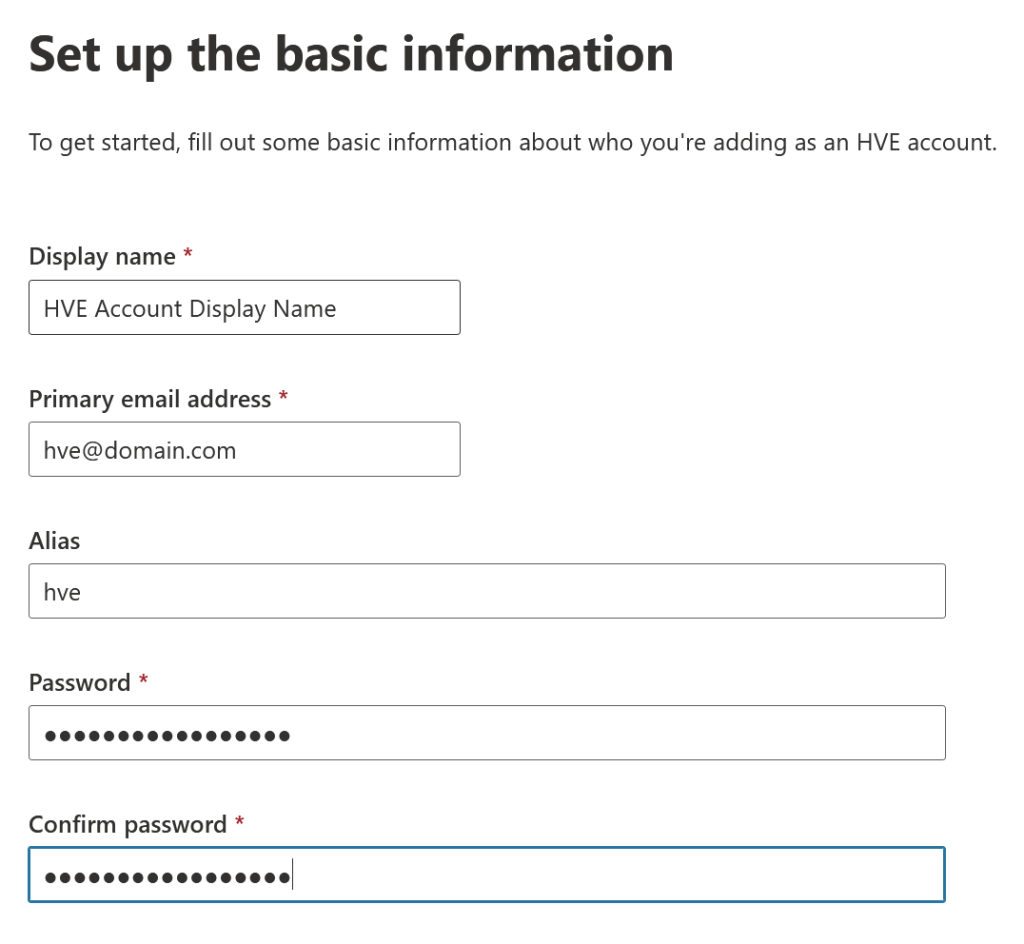
Click Next and the account is reviewed and then created. Its really easy!
The list of HVE accounts will update to show your new account, and shortly this account will appear in Entra ID as well.
If you have Conditional Access rules that block Legacy Authentication and you are using basic SMTP auth then you need to exempt this account from those rules. So either add the new user account to a group that exempts these rules via Entra ID > Groups or exempt the account directly in the Conditional Access rule.
If you have a custom Authentication Policy in Exchange Online that blocks legacy auth you need to create a new Authentication policy that has AllowBasicAuthSmtp enabled and then apply that policy to the HVE account using PowerShell – in the example below we list your current authentication policies and create a policy called “Block Legacy Authentication For All Except AuthSMTP”:
Get-AuthenticationPolicy | FL Name
New-AuthenticationPolicy "Block Legacy Authentication For All Except AuthSMTP" -AllowBasicAuthSmtp
Once the policy is made in the above example, we assign it to the HVE user account. The below cmdlet sets the users sign in token expiry time to one day in the past we well as setting the Authentication Policy. This token refresh change also means the policy takes effect immediately:
Set-User hve@domain.com -AuthenticationPolicy "Block Legacy Authentication For All Except AuthSMTP" -StsRefreshTokensValidFrom ([DateTime]::Now.AddHours(-24))
Finally you can send the email for testing. This uses a new endpoint, so it needs to be open on any firewalls etc. Here is an example of using the depreciated Send-MailMessage PowerShell cmdlet to send an email:
$hve = Get-Credential
Send-MailMessage -From hve@domain.com -To breid@domain.com -Subject "Hello - HVE Testing" -Body "This is a test email to prove HVE delivery." -SmtpServer smtp-hve.office365.com -UseSsl -Port 587 -Credential $hve
If it does not work you will get an error back. Here are three errors I have seen:
“Send-MailMessage: The SMTP server requires a secure connection or the client was not authenticated. The server response was: 5.7.57 Client not authenticated to send mail. Error: 535 5.7.139 Authentication unsuccessful, basic auth is blocked. Contact your administrator.“.
If you get this first error, the place to check is that you might have blocked legacy auth in Exchange Online and not created or updated the Authentication Policy on the user account. If you have changed the Authentication Policy assignment to the user wait 24 hours and try again, or reset the StsRefreshTokensValidFrom property and try again.
Or, for Error #2 “The SMTP server requires a secure connection or the client was not authenticated. The server response was: 5.7.57 Client not authenticated to send mail. Error: 535 5.7.139 Authentication unsuccessful, SmtpClientAuthentication is disabled for the Tenant. Visit https://aka.ms/smtp_auth_disabled for more information.“
This means that you have connected to the wrong endpoint for High Volume Email. The endpoint (SMTP Server) value needs to be smtp-hve.office365.com.
Or, for the last error I have seen “535 5.7.139 Authentication unsuccessful, the organization configuration does not allow this authentication request. Visit https://learn.microsoft.com/en-us/azure/active-directory/develop/reference-error-codes for more information. Error code: AADSTS53003“
This error means BlockedByConditionalAccess – Access has been blocked by Conditional Access policies. The access policy does not allow token issuance and so you need to check the sign-in logs for the HVE user to see what the logs show has happened and which Conditional Access rule is blocking your login. If you have Security Defaults enabled then you will be blocked, and as you cannot bypass Security Defaults without turning them off, either get Entra ID Plan 1 licences for everyone and implement Conditional Access or use another service such as Azure Communication Services (ACS) for your email sending.
You can also use Conditional Access > What If to check your Conditional Access rules before attempting to send an email. With What If you see to select your HVE user, the “Office 365 Exchange Online” app and “Mobile apps and desktop clients – Other clients” to perform your “What If” test. Do not select a Device Platform:
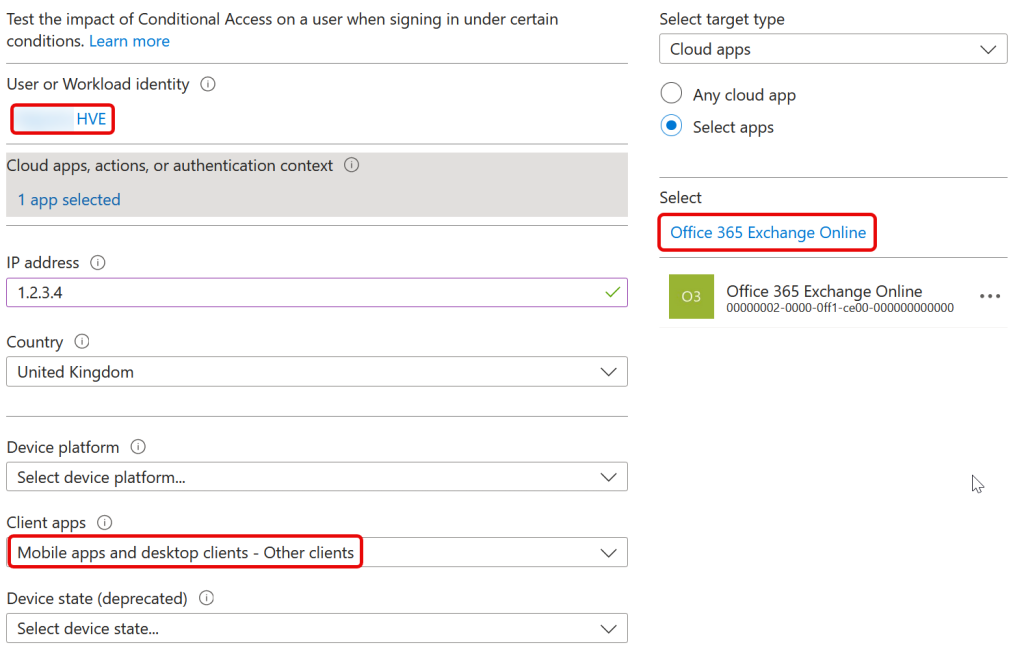
For example, if you have a Conditional Access rule that blocks unknown device platforms then HVE accounts will fail as the SMTP Legacy Auth session does not report a device platform.
Once you have it working, it is time for the real work – that is updating all your basic auth internal email sender applications to use the new endpoint and credentials!
Finally, just out of interest – HVE does not use SMTP internal to Exchange Online, but uses HTTP Submission to inject the messages into the mailbox.
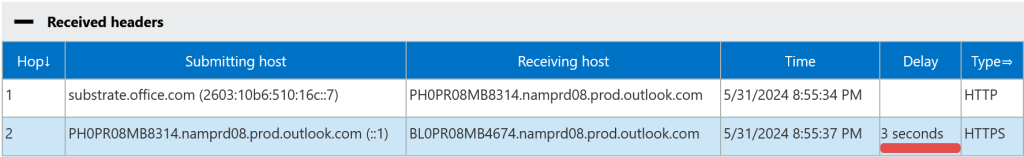
Other services such as Azure Communication Services will use SMTP and so will need to route via your MX record, SPF and DKIM configurations will also be needed.
Photo by Ylanite Koppens: https://www.pexels.com/photo/letters-and-an-eyeglass-on-table-1809342/

Leave a Reply