Category: email
-

Implementing High Volume Email with Exchange Online
High Volume Email (HVE) is a new service from Microsoft to allow the sending of up to 100,000 internal emails per day (with a small number external) which is in excess of the current limits of 10,000 per day (depending upon your licence). Here are my initial observations on setting this service up. During preview…
-

What Is “mx.microsoft”?
mx.microsoft is the new MX delivery domain for Exchange Online. For years now it has been mail.protection.outlook.com, but this domain will not work with the new DNSSEC extensions that Exchange Online will start to support. When you added a new domain (called a vanity domain) to Microsoft 365, it would show you the MX record…
-

Post Tenant To Tenant Migration Calendaring Issues
When you perform a Microsoft 365 tenant to tenant (T2T) migration and run a migration that is either staged over some time or sometime after the migration has completed you cutover the domains from the old tenant to the new tenant (that is, you were doing a rebrand and the new tenant had a new…
-

Improving Exchange Online Email Deliverability Through Third Party Filtering Services – Trusted ARC Sealer
When you receive emails into Exchange Online and you filter the external messages before arrival with a third party filter such as Mimecast, Proofpoint or others, then you can have DMARC failures that result in messages being junked or quarantined in Exchange Online. Trusted ARC Sealer is a feature of Exchange Online to allow you…
-

Safe Links, Microsoft Teams Rooms or Zoom Rooms, and Preset Security Policies
Or “How to customize Microsoft 365 Preset Security Policies“! The Preset Security Policies in Microsoft 365 allow you to assign to users, groups or domains the recommend anti-spam, anti-spoofing and anti-malware settings (amongst others). In the Microsoft 365 Security Portal (https://security.microsoft.com) where you set this there appears to be no way to customize these policies…
-

Finding Existing Plus Addresses
Exchange Online will automatically enable “Plus Addressing” for all tenants from Jan 2022. This change may cause issues if you have existing mailboxes where the SMTP address contains a + sign. That is, directors+managers@contoso.com would be considered a broken email address from Jan 2022 in Exchange Online. So you need to check you have no…
-
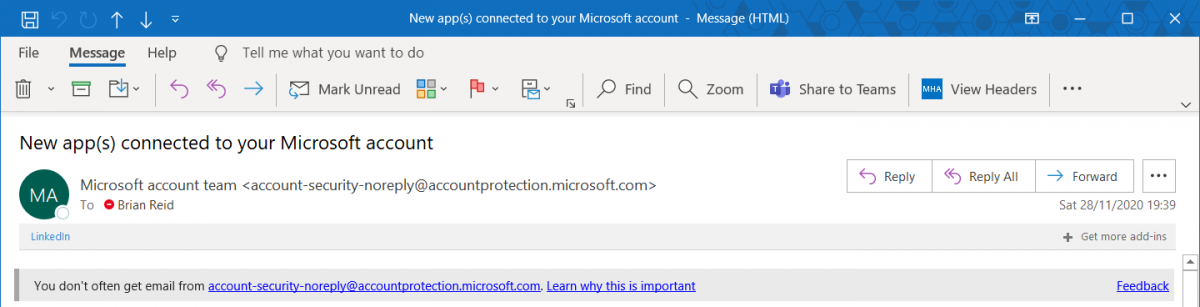
Exchange Online Warning On Receipt Of New Email Sender
Released recently to no fanfare at all, Microsoft now has a SafetyTip that appears if you receive email from a first time recipient. Most often phish emails will come from an address you have never received email from before, and sometimes this email will try to impersonate people you communicate with or are internal to…
-
MFA and End User Impacts
This article will look at the various different MFA settings found in Azure AD (which controls MFA for Office 365 and other SaaS services) and how those decisions impact users. There is lots on the internet on enabling MFA, and lots on what that looks like for the user – but nothing I could see…
-
Too Many Folders To Successfully Migrate To Exchange Online
Exchange Online has a limit of 10,000 folders within a mailbox. If you try and migrate a mailbox with more than this number of folders then it will fail – and that would be expected. But what happens if you have a mailbox with less than this number of folders and it still fails for…