One relatively easy way to block some categories of phishing email is to block the attachment type that is sent with some of these messages. For example, I have had a few of these recently:
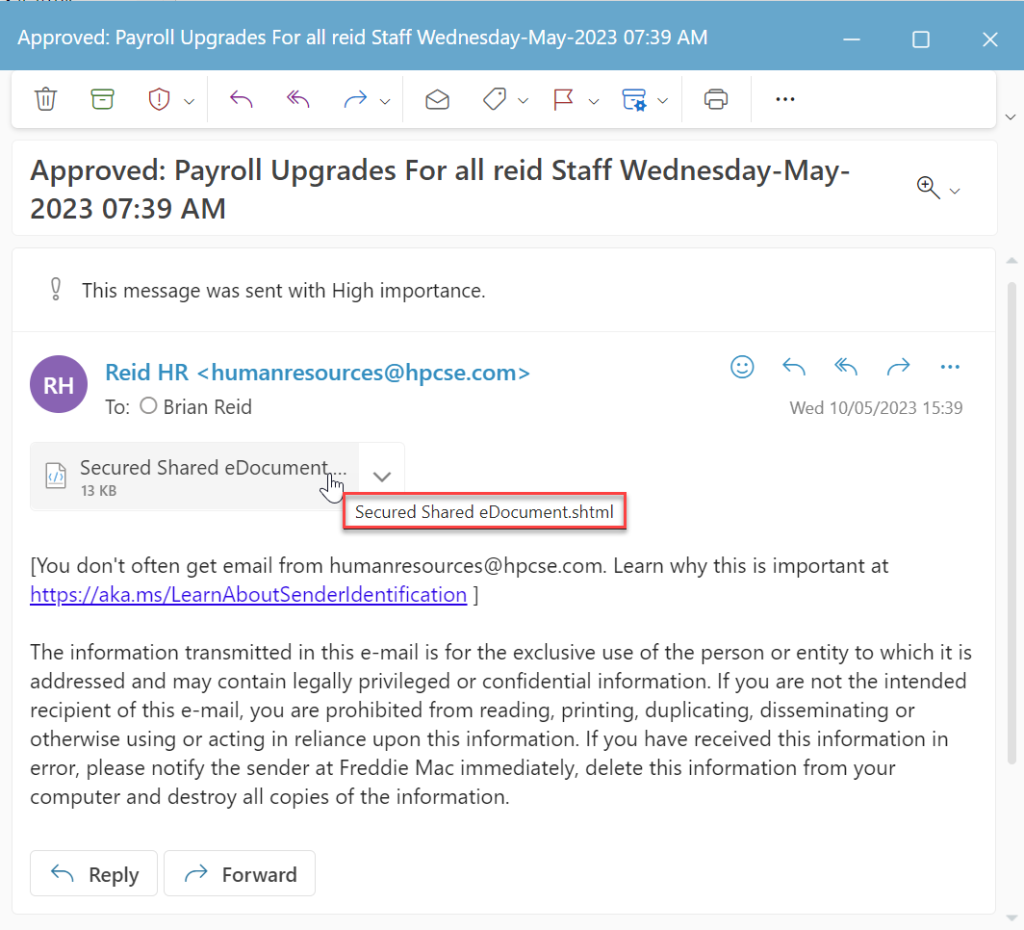
Hovering over the attachment I see the filename, and it ends .shtml. This attachment is for server-side HTML (SSI includes if you are interested) and so has no place in an email. But it is opened and rendered by most client browsers without restriction.
This phish typically contains some hashed or encrypted code that the browser runs as javascript or the like and redirects to a malicious webpage aimed at taking something from the user (credentials or if running a reverse proxy, their MFA as well).
So given there is no reason for this attachment type in email, how can we just stop it in Exchange Online/Microsoft 365? To do this we make use of the “Attachment Filter” part of the anti-malware policy.
By default this is disabled and if you use the preset-security policies it is enabled but has no file types added to it, therefore it is effectively disabled in all tenants unless you take action. I wrote back in 2017 how to turn this on using the same values in the Exchange Server Edge Server role, and so I an going to use similar here. It will take a few seconds to turn on, and you just need to decide what attachment extensions to impact, and if you want to reject them (NDR to the sender) or quarantine them.
Attachment filtering true-types the attachment, so a renamed attachment is treated based on the file type and not the name of the file. For example a compressed file will be blocked if the non-compressed format is also blocked – so block a .exe but not a .zip and then send in a compressed exe file – it will be blocked!
If you have already enabled the attachment filter then slightly different instructions are needed to add the .shtml file type to the list. So pick the correct instructions you need.
Both of the following use Exchange Online PowerShell to do the changes in bulk and quickly, but this can all be done (apart from updates to the preset security policies) via the Anti-Malware Policies at https://security.microsoft.com/antimalware.
Enabling Attachment Filtering for the first time
In Exchange Online PowerShell check the names of the anti-malware policies you have in place and if the file attachment policies are active:
Get-MalwareFilterPolicy | fl name,*file*
You will get back the “Default” policy which is disabled for the attachment filter out of the box:
Name : Default
EnableFileFilter : False
FileTypeAction : Reject
FileTypes : {ace, apk, app, appx…}
You can see that there are some existing file attachment types in this rule, and so you could just enable it, but we want to add .shtml (and .shtm whilst we are at it). So you would run this cmdlet to get the current list of FileTypes, add additional values to the list and the write the new list back to the configuration. We will also turn on the feature, and we note that it is set to reject emails that fail the policy (and not to quarantine them).
Microsoft document the current default list of file types they would block (if the feature was enabled) at Anti-malware protection – Office 365 | Microsoft Learn.
This cmdlet gets the FileTypes from the existing Default policy, but it updates the Preset Security Policies and any other policies that exist as well to what your Default list is currently plus the shtml/shtm extensions we are blocking (sorted and duplicates removed).
$filetypes = (Get-MalwareFilterPolicy Default).FileTypes
$filetypes = $filetypes + "shtml" + "shtm"
$filetypes = $filetypes | Sort -Unique
Get-MalwareFilterPolicy | Set-MalwareFilterPolicy -FileTypes $filetypes -FileTypeAction Reject -EnableFileFilter $true
If you are updating the preset security policies you will see a message saying “WARNING: All recommended properties will be controlled by Microsoft.” and as these file attachment settings are not centrally controlled by Microsoft, your settings take effect.
To add additional attachments (but don’t add .html and .htm as that will break stuff), just append them to the second line – for example years ago Microsoft Edge Server used to block ade, adp, asx, bas, bat, chm, cpl, crt, csh, fxp, hlp, inf, ins, isp, js, jse, ksh, mda, mdb, mde, mdt, mdw, mdz, ops, pcd, prf, prg, ps1, ps11, ps11xml, ps1xml, psc1, psc2, scf, shs, and url as well as all the Exchange Online defaults. Some of these are now blocked by Outlook directly, but some should be considered for adding as well!
For a reference list see https://github.com/0xAnalyst/awesome-email-security/blob/main/FileExtensionstoblock.md, though take the ChatGPT created one with care as it contains attachment extension types that would break standard MIME type emails, such as HTML emails.
Removing Attachment Filtering Extensions
To remove attachment extensions you have previously added, get the current list as an array and then remove items from that list:
$filetypes = (Get-MalwareFilterPolicy Default).FileTypes
$filetypes.Remove("html") # to remove 'html' from the list
Set-MalwareFilterPolicy "Name Of Policy" -FileTypes $filetypes
Updating Attachment Filtering with new attachment types
To add to an existing list, you just need to know the name of the policy that contains the list you want. This example is the Default policy list:
$filetypes = (Get-MalwareFilterPolicy Default).FileTypes
$filetypes = $filetypes + "shtml" + "shtm"
To add even more attachment types to filter out, you just extend the list of $filetypes you want to exclude. This contains 60+ more attachment types to block on top of the default, including some macro files extensions at the end you might want to consider.
$filetypes = $filetypes + "ade" + "adp" + "cpl" + "app" + "bas" + "asx" + "bat" + "chm" + "cmd" + "com" + "crt" + "csh" + "exe" + "fxp" + "hlp" + "hta" + "inf" + "ins" + "isp" + "js" + "jse" + "ksh" + "lnk" + "mda" + "mdb" + "mde" + "mdt" + "mdw" + "mdz" + "msc" + "msi" + "msp" + "mst" + "ops" + "pcd" + "pif" + "prf" + "prg" + "ps1" + "ps11" + "ps11xml" + "ps1xml" + "ps2" + "ps2xml" + "psc1" + "psc2" + "reg" + "scf" + "scr" + "sct" + "shb" + "shs" + "url" + "vb" + "vbe" + "vbs" + "wsc" + "wsf" + "wsh" + "xnk" + "ace" + "ani" + "docm" + "jar" + "asp" + "cer" + "der" + "dll" + "dos" + "gadget" + "hta" + "inf" + "ins" + "isp" + "its" + "jse" + "ksh" + "lnk" + "mad" + "maf" + "mag" + "mam" + "maq" + "mar" + "mas" + "mat" + "mau" + "mav" + "maw" + "msh" + "msh1" + "msh1xml" + "msh2" + "msh2xml" + "mshxml" + "obj" + "os2" + "plg" + "pst" + "rar" + "tmp" + "vsmacros" + "vsw" + "vxd" + "w16" + "ws" + "apk" + "appx" + "cab" + "iso" + "library" + "lib" + "msix" + "mhtml" + "mht" + "msixbundle" + "terminal" + "plugin" + "font" + "command" + "bundle"
# new items added to this list in 2024
$filetypes = $filetypes + "lnk" + "hta" + "inf" + "isp" + "ins" + "action" + "appxbundle" + "asf" + "avi" + "bin" + "mht" + "vhd" + "dylib"
# To include Office macro files in the block list:
$filetypes = $filetypes + "dotm" + "pptm" + "potm" + ppsm" + sldm" + "xlm" + "xlsb" + "xlsm" + "xltm" + "vsdm" + "vstm"
# Sort the list alphabetically as this is the order it will appear in the admin portal, so this makes it easier to check the list in future. This cmdlet also removes any duplicates in case my list above includes filetypes you have already added
$filetypes = $filetypes | Sort -Unique
# Update the Default policy
Set-MalwareFilterPolicy Default -FileTypes $filetypes
# And if you have the preset policies in use, update these as well.
Set-MalwareFilterPolicy Standard* -FileTypes $filetypes
Set-MalwareFilterPolicy Strict* -FileTypes $filetypes
This set of cmdlets do not change the enabled status or the rejection type. Otherwise they are the same as the above cmdlets.
To copy your list to all your policies, use this at the end instead of the last line above
Get-MalwareFilterPolicy | Set-MalwareFilterPolicy -FileTypes $filetypes
If you have the M365 E5 licence you can use Advanced Hunting to see if you have received any particular attachment type in the previous x days. For example the following will show you who is sending and receiving Excel macro files. You can use this KQL query to determine any impact from any filename extension you want to block.
EmailAttachmentInfo
| where FileName endswith ".xlsm"
Or, this KQL which will show all the attachment extensions received from a given sender:
EmailAttachmentInfo
| where SenderFromAddress contains "billing@domain.com"
| where FileName contains "."
| extend Extension = reverse(split(reverse(FileName),".")[0])
| distinct Extension
Photo by Sora Shimazaki: https://www.pexels.com/photo/crop-ethnic-hacker-with-smartphone-typing-on-laptop-in-dark-room-5935792/

Leave a Reply