Category: conditional access
-

Simple Security for Microsoft 365
There are many many security settings in Microsoft 365, including Entra ID, SharePoint, Exchange Online etc. But knowing where to look and what to change has been complex, even for people skilled in this range of products. Well this is about to change with Microsoft 365 Baseline Security Mode. This is reachable via the M365…
-

Switching SharePoint To Use Entra Guest Sharing With EnableAzureADB2BIntegration $true
In 2021 Microsoft released an update to SharePoint guest sharing that stopped it using its own SharePoint created guest accounts and would start to use Entra ID Guest Accounts. The accounts in Entra are subject to Conditional Access Policies (and Secure Defaults), MFA Trust, Authentication Methods and Authentication Strengths, and Access Policies and a host…
-

Reducing the Number of Sign-In Prompts in GitHub Managed Identity Logins
When you set up Managed Identities in GitHub, using the OIDC app in Entra ID you will see that you are prompted to re-authenticate every hour. This prompt gets in the way and is annoying, as well as training your developers that any sign-in prompt should be completed (and thus making your developers easier to…
-
Export Conditional Access Named Locations Using PowerShell
The named locations can be used in Conditional Access rules as a way to block or allow countries by IP address to geo-lookup database. Whilst not always accurate, and can be bypassed by VPN or a virtual machine in an allowed location, they do have their uses as a basic block to where services can…
-

Inviting Google (Gmail) Users To Collaborate In Your Teams Channels
This post is not about inviting Google users to your meetings, where you just send them the meeting invite and all is good. This is about adding the Gmail user as a member of a Team, so they can see the Teams channels, chat and collaborate with files and apps along with everyone else in…
-

Conditional Access Authentication Strengths
Newly released to Conditional Access in Azure AD is the “Authentication Strengths” settings. These allow you to control the strength of the authentication you need to be used for that conditional access rule. Before this feature was available you had the option of allowing access with no second factor, MFA as a second factor (any…
-

What Is “Multifactor Authentication Trusted IPs”
In Azure AD for location based conditional access rules you can select “Multifactor Authentication Trusted IPs” as a location. This short blog post outlines what this is. As an example of the use of this location, it could be used as follows in Conditional Access: The location selected in the above is “Multifactor Authentication Trusted…
-
MFA, Admin Roles and AADConnect Sync Failures
Come Feb 29th 2020 and Microsoft are turning off the baseline security policies. If you used these policies to do MFA for all admins (as that was an easy way to achieve this), then a replacement Conditional Access rule might cause errors with AADConnect. The reason being is that you could create a new Conditional…
-
Baseline Policy Replacements: Conditional Access MFA for Administrators
From Feb 29th 2020 Microsoft will remove the “baseline policies” from Azure AD. These were very useful in the past to enable blanket settings like MFA for all admin accounts (well, selected admin roles) and to disable legacy auth for the same admin roles. With the removal of the baseline policies you need to ensure…
-
MFA and End User Impacts
This article will look at the various different MFA settings found in Azure AD (which controls MFA for Office 365 and other SaaS services) and how those decisions impact users. There is lots on the internet on enabling MFA, and lots on what that looks like for the user – but nothing I could see…
-
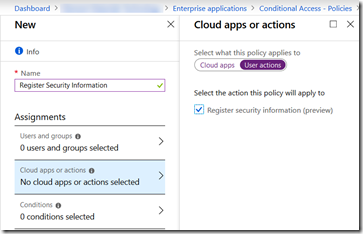
Register For Azure AD MFA From On-Premises Or Known Networks Only
A long request within Azure AD/Office 365 has been the request to be able to register your security info from a known location or only on certain other conditions. Well it looks like this has appeared in Azure AD in the last few days!! Its visible under Azure AD > Conditional Access > New/Existing Policy…
-
Read Only And Document Download Restrictions in SharePoint Online
Both SharePoint Online (including OneDrive for Business) and Exchange Online allow a read only mode to be implemented based on certain user or device or network conditions. For these settings in Exchange Online see my other post at https://c7solutions.com/2018/12/read-only-and-attachment-download-restrictions-in-exchange-online. When this is enabled documents can be viewed in the browser only and not downloaded. So…
-
Azure AD Single Sign-On Basic Auth Popup
When configuring Azure AD SSO as part of Pass-Through Authentication (PTA) or with Password Hash Authentication (PHA) you need now (since March 2018) to only configure a single URL in the Intranet Zone in Windows. That URL is https://autologon.microsoftazuread-sso.com and this can be rolled out as a registry preference via Group Policy. Before March 2018…
-
OWA and Conditional Access: Inconsistent Error Reports
Here is a good error message. Its good, because I could not find any references to it on Google and the fault was nothing to do with the error message: The error says “something went wrong” and “Ref A: a long string of Hex Ref B: AMSEDGE0319 Ref C: Date Time”. The server name in…
