A long request within Azure AD/Office 365 has been the request to be able to register your security info from a known location or only on certain other conditions. Well it looks like this has appeared in Azure AD in the last few days!!
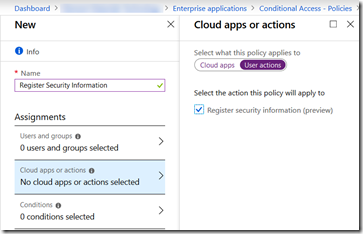
Its visible under Azure AD > Conditional Access > New/Existing Policy > Cloud Apps or Actions:
So, what does this look like in practice? Lets put this preview to the test.
Create the Conditional Access Policy for User Actions
Open the Azure AD portal at https://aad.portal.azure.com and click Enterprise Applications
From here click Conditional Access (this is also accessible under Azure AD > Security as well)
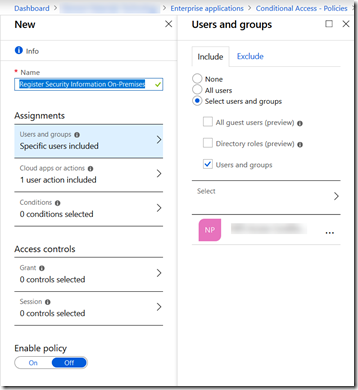
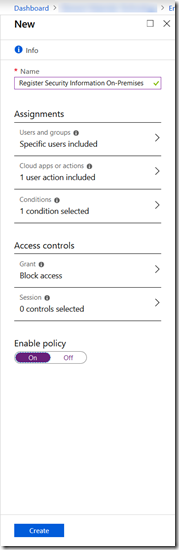
Click Add Policy and give the policy a name. I have chosen “Register Security Information On-Premises” for here
Click Users and Groups. I have selected “Users and Groups” rather than “All Users” as I plan to test this out first! I have picked the group that I use for testing Conditional Access changes. Eventually I will change this to All Users so that no-one can register security info apart from when on a trusted location. Note that this would also I think include guest users – I need to test that! Guest users are by their very nature not on my network but I might have MFA required for them – so they need to register, but I don’t want to apply the below to them
Select Cloud Apps or Actions (this was recently renamed to support this functionality we are describing here)
Select User Actions in the slider and check the option for Register Security Information (Preview)
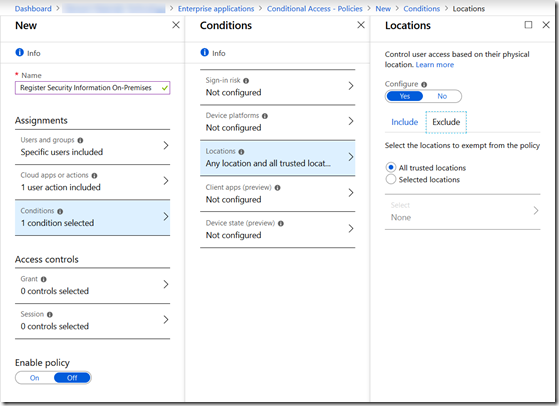
Select Conditions and select the conditions you want to apply when users are registering security information. Its probably location based, so I will set that up here.
Select Locations, click Yes under Configure and select Any Location under Include and then under Exclude select Trusted Locations. Note that you need to have set up trusted locations in Conditional Access as well – I’m going to assume the public IP of all your offices is added and marked as trusted.
This setting will ensure that all locations other than trusted locations cannot register security information – note that this is the reverse of what you might expect. We need to block the locations we don’t want to access the MFA/SSPR registration process rather than the reverse. This is because we are required to add a control to the rules
With Azure AD P2 licences you could user a sign-in risk condition, ensuring that registration does not happen on medium or high risk sign-ins!
Click Done to bring you back to the first blade of settings and set Enable Policy to On to turn on this feature
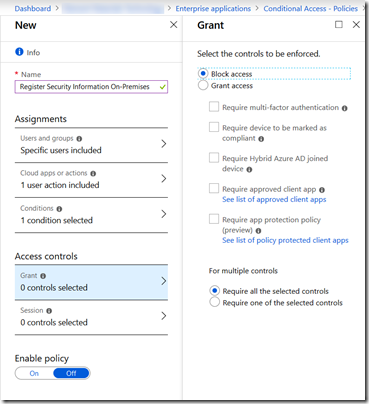
Under Access Controls, click Grant and choose Block Access – be very careful here – don’t block all your access to everything!
Click Done
This takes us back to the first blade in the Conditional Access settings.
Click On in the Enable Policy slider
Now the Create button is available – this is not available if you do not create the reverse of what you might expect to do – block unknown locations rather than allow trusted locations!
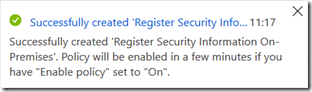
Click Create
You will get your notification – you can test this in a few minutes:
Enable The New Combined MFA/SSPR Registration Page
Though I noticed that this conditional access restriction works against the older MFA registration page, Microsoft have said in their release blog article for this feature that it will only work against the new MFA/SSPR combined registration page. Therefore you should turn this on for your users impacted by the above policy – initially for your pilot users and then for all users.
See https://techcommunity.microsoft.com/t5/Azure-Active-Directory-Identity/Cool-enhancements-to-the-Azure-AD-combined-MFA-and-password/ba-p/354271 for more on setting up the combined MFA/SSPR registration page.
Testing Register Security Information (Preview)
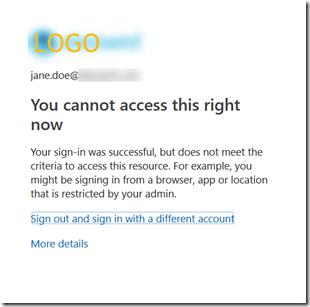
In an in-private browser session on the Wi-Fi of your favourite coffee company, browse to https://aka.ms/mfasetup (as this is not a trusted location!)
After logging in you would expect to be take to the registration page for MFA and SSPR – but you are not!
Repeat your test from on-premises, and you will get the MFA and SSPR registration pages (or both if you have the new combined MFA+SSPR wizard enabled):
Note that for a brand new user where you have SSPR enabled, they are required to register by default every 180 days. This will mean they have to register at first login – therefore first login needs to be from a trusted network (in this example) – you could use Trusted Device as the only place to register from, but adding a user to a trusted device requires MFA by default, so watch out for an issue here and if you want to do this, test it very well.
I have not had the opportunity to test this with the 180 day refresh of your settings – presumably that should work from any location and only changing them would be blocked, but this is something that needs to be tried out.
Leave a Reply