Category: enterprise mobility + security
-
Adding Apple Well-Known RemoteManagement JSON to IIS Web Servers
To do Account driven BYOD device enrolment in Intune for iOS devices you need to publish to the website on your domain a JSON file that contains your tenant ID. The URL for this file is https://c7solutions.com/.well-known/com.apple.remotemanagement where the domain (c7solutions.com in this case) is the same as the domain of the username on the…
-

Authentication Methods – What Happens If I Click That Button
There are various buttons in the Entra ID portal that can be used in the event of an incident with a user account, but each have different effects and can be used in different circumstances. This blog post outlines the impact of each button on the user. To do these tests I performed a standard…
-

B2B Collaboration and Easy Multifactor Authentication in Microsoft 365/Entra ID
A couple of conversations this week, including this prompt by Daniel Glenn – https://x.com/DanielGlenn/status/1812952597759992149 have led me to write up this quick guide to making your cross-tenant, resource account, guest, B2B Collaboration users (note, these are all the same thing) multi-factor authentication easy. If you don’t do this, then the user needs to set up…
-

SSL Inspection and Microsoft 365
There are a number of features in Microsoft 365 that do not work if SSL Inspection (also known as TLS Interception) is enabled on your device or network provider. You need to disable the listed URLs that Microsoft provides in its documentation. The problem is there is a lot of disconnected documentation! This blog post…
-
Domain Tenant Move and Device Join Issues
I discovered recently an issue following a tenant to tenant Microsoft 365/Azure AD migration. The issue was that devices would not enroll with Intune in the old tenant because the settings the device was getting was mixed up between the old and new tenants. In the case I had, the new tenant was not yet…
-

Adobe Creative Cloud and Conditional Access Restrictions
In Azure Active Directory it is possible to create Conditional Access rules that restrict applications to only running on company owned or managed devices. Conditional Access approves or rejects the login based on that knowledge – so what happens if the app in question is running on a company (managed or compliant) machine, but the…
-

Conditional Access in Defender for Cloud (MCAS)
I was asked this question last week at Microsoft Ignite following a talk that I did, and as it was a question it was clearly not as clear cut as maybe I thought it was. The question was, “why is Conditional Access found in Azure AD and Defender for Cloud?” (Defender for Cloud was previously…
-

What Is “Multifactor Authentication Trusted IPs”
In Azure AD for location based conditional access rules you can select “Multifactor Authentication Trusted IPs” as a location. This short blog post outlines what this is. As an example of the use of this location, it could be used as follows in Conditional Access: The location selected in the above is “Multifactor Authentication Trusted…
-
MFA and End User Impacts
This article will look at the various different MFA settings found in Azure AD (which controls MFA for Office 365 and other SaaS services) and how those decisions impact users. There is lots on the internet on enabling MFA, and lots on what that looks like for the user – but nothing I could see…
-
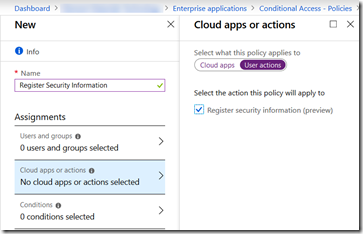
Register For Azure AD MFA From On-Premises Or Known Networks Only
A long request within Azure AD/Office 365 has been the request to be able to register your security info from a known location or only on certain other conditions. Well it looks like this has appeared in Azure AD in the last few days!! Its visible under Azure AD > Conditional Access > New/Existing Policy…
-
Read Only And Document Download Restrictions in SharePoint Online
Both SharePoint Online (including OneDrive for Business) and Exchange Online allow a read only mode to be implemented based on certain user or device or network conditions. For these settings in Exchange Online see my other post at https://c7solutions.com/2018/12/read-only-and-attachment-download-restrictions-in-exchange-online. When this is enabled documents can be viewed in the browser only and not downloaded. So…
-
Improving Password Security In the Cloud and On-Premises
Passwords are well known to be generally insecure the way users create them. They don’t like “complex” passwords such as p9Y8Li!uk%al and so if they are forced to create a “complex” password due to a policy in say Active Directory, or because their password has expired and they need to generate a new one, they…
-
OWA and Conditional Access: Inconsistent Error Reports
Here is a good error message. Its good, because I could not find any references to it on Google and the fault was nothing to do with the error message: The error says “something went wrong” and “Ref A: a long string of Hex Ref B: AMSEDGE0319 Ref C: Date Time”. The server name in…
