In Azure AD for location based conditional access rules you can select “Multifactor Authentication Trusted IPs” as a location. This short blog post outlines what this is.
As an example of the use of this location, it could be used as follows in Conditional Access:
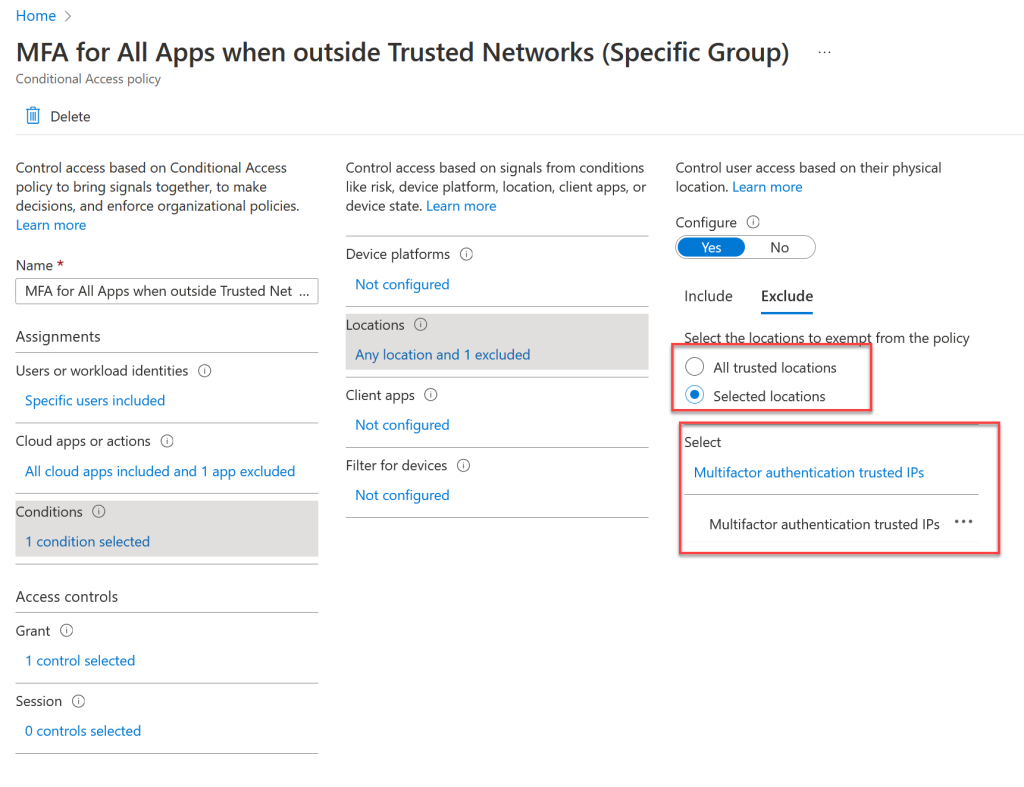
The location selected in the above is “Multifactor Authentication Trusted IPs”. This location is selectable as a location in the Conditional Access rules, but is not a location you can configure in the Named Locations area of Azure AD Security.
The source of this data comes instead from the legacy, or per-user MFA settings that should now not be used (instead use Security Defaults or Conditional Access). The settings for per-user MFA include a list of IPs that MFA can be skipped from, and this list is empty by default:
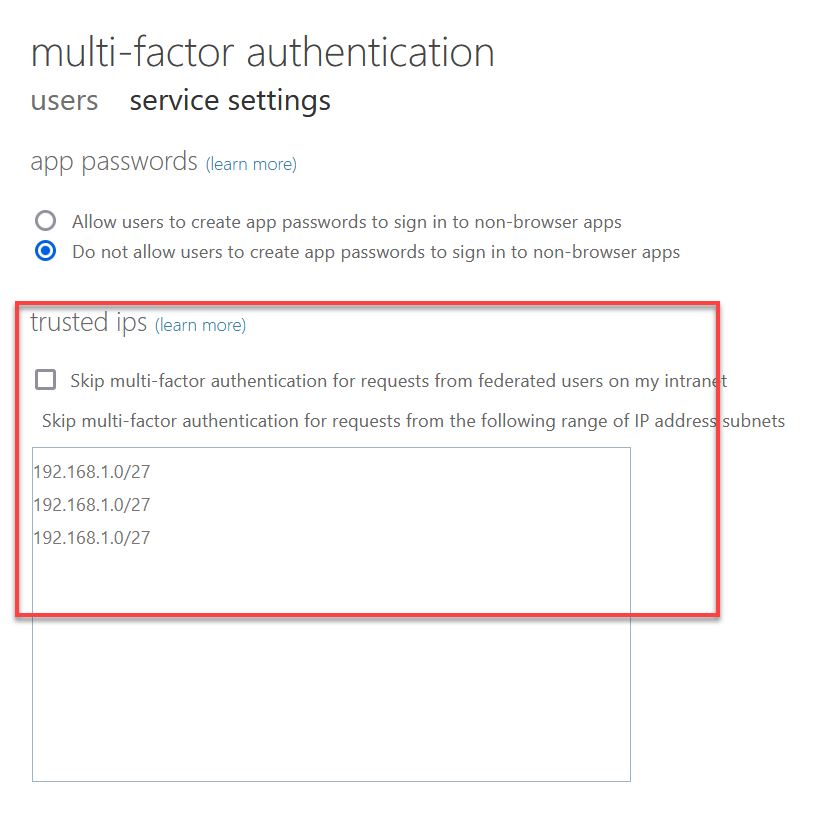
Though this dialog lists 192.168.1.0/27 three times, if you click on this dialog in the per-user MFA service settings page, these values disappear (and they should be public IP addresses anyway if in use).
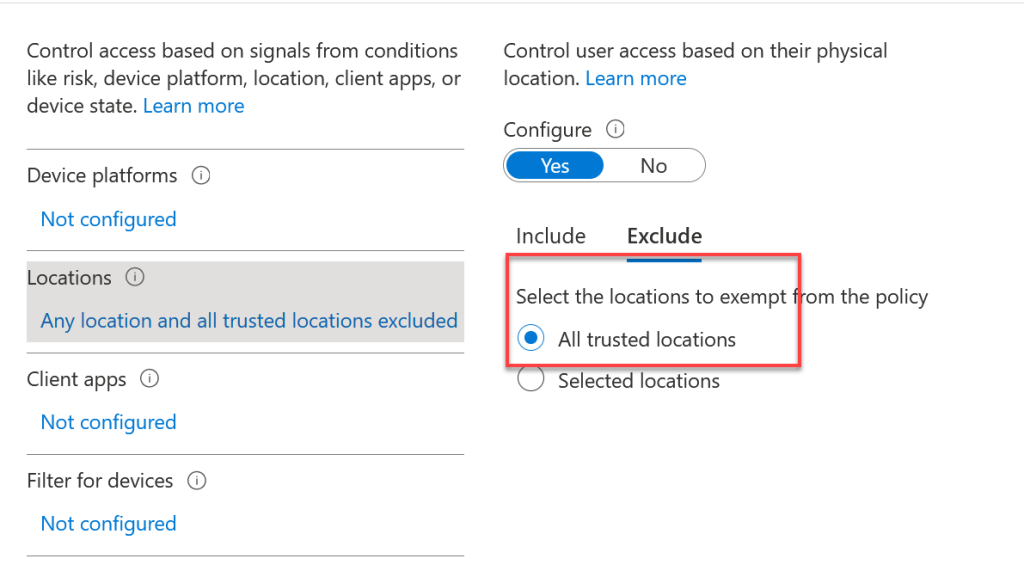
Therefore, it is better to use Named Locations in Conditional Access rules (for example “All Trusted Locations” as shown below) instead of the legacy setting, especially as you might never have set it if you have never used the per-user settings:

Leave a Reply