When you set up Managed Identities in GitHub, using the OIDC app in Entra ID you will see that you are prompted to re-authenticate every hour. This prompt gets in the way and is annoying, as well as training your developers that any sign-in prompt should be completed (and thus making your developers easier to phish).
The GitHub and also the Microsoft documentation for the change is not very clear – so this is what you need to do.
- Create a new Token Lifetime Policy (or if you have one already for another app for the same lifetime you can reuse that one). We will look for existing policies and create a new one below.
- Get the Enterprise App Object ID that you want to associate the Token Lifetime Policy with
- Apply the Token Lifetime Policy to the Enterprise App. We will do all these steps using the Graph Explorer (as the PowerShell cmdlets for this can change every month and so it often proves hard to do or will generate errors if you use a different version of the Graph PowerShell module than I do!
So, open the Microsoft Graph Explorer from https://aka.ms/ge and sign in so you are logged in to your tenant. You need to have GitHub Managed Identities and the OIDC app already in place. Step 1 is to create a new policy, and first looking to see if any policy exists:
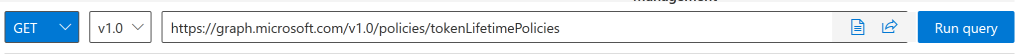
In the Graph Explorer enter the URI “https://graph.microsoft.com/v1.0/policies/tokenLifetimePolicies” and ensure it says GET to the left. Click Run Query. If you do not have permissions to do this you will see this:
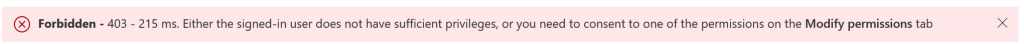
Click the Modify Permissions button in middle-right pane of the screen and you will see a set of permissions, any one of which will give you access to view the policies (if they exist). You will also see higher permissions than you need, but in this example we know what we need and so we will consent all these permissions at this time.
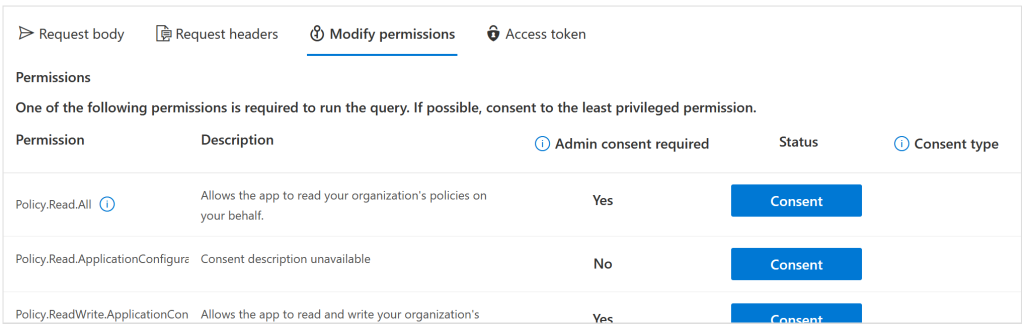
Click on Policy.ReadWrite.ApplicationConfiguation which is shown as the last of three in my example above. Do NOT consent any permissions on behalf of your organization as you need the permission, everyone else does not!
Also consent to Policy.Read.All.
In my tenant, as I have already done all the steps already and am documenting them after the fact. I have a policy as shown:
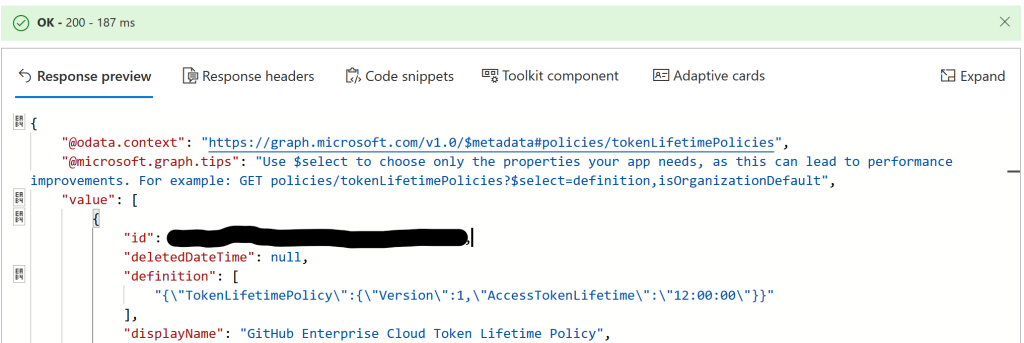
If the policy exists it will have an ID. Record a copy of this ID for later – we will call this ID the TokenLifetimePolicyID. You can see from above that I have chosen a 12 hour timeout for my app.
If I need to make a new Token Lifetime Policy then I need to POST a new policy to the above URI and that will generate an ID for the policy, and that ID will be my TokenLifetimePolicyID.
POST https://graph.microsoft.com/v1.0/policies/tokenLifetimePolicies
{
"definition": [
"{\"TokenLifetimePolicy\":{\"Version\":1,\"AccessTokenLifetime\":\"8:00:00\"}}"
],
"displayName": "Token Lifetime Policy for Contoso Application",
"isOrganizationDefault": false
}
In the above, customise the displayName and the value in h:mm:sec for the AccessTokenLifetime. The example above is 8 hours and zero minutes, zero seconds.
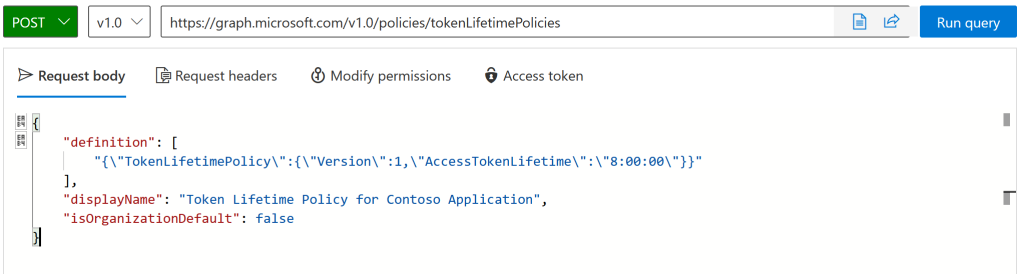
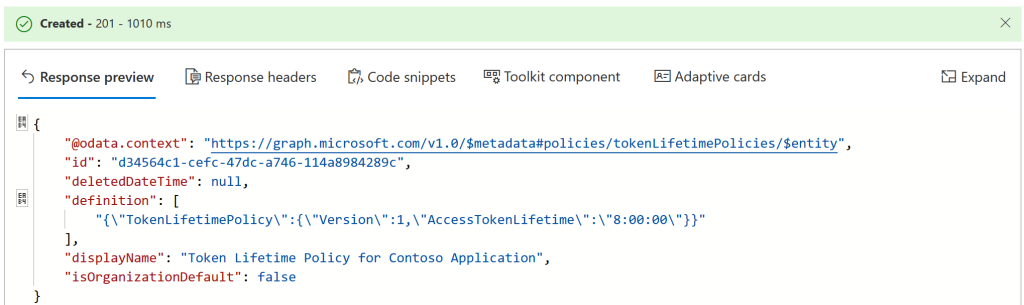
The above picture shows this new policy in the Graph Explorer. Run the query to create the policy. You will get back the ID, which for our purposes is the TokenLifetimePolicyID:
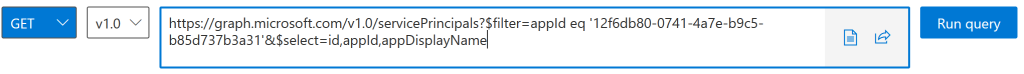
Once you know the Token Lifetime Policy ID you need to get the Object ID of the application. For GitHub Managed Identity OIDC Enterprise App, this is the Object ID of the application, where the Application ID is 12f6db80-0741-4a7e-b9c5-b85d737b3a31. You can query for this as well with GET https://graph.microsoft.com/v1.0/servicePrincipals?$filter=appId eq ’12f6db80-0741-4a7e-b9c5-b85d737b3a31’&$select=id,appId,appDisplayName
Consent to Application.Read.All to see this information:
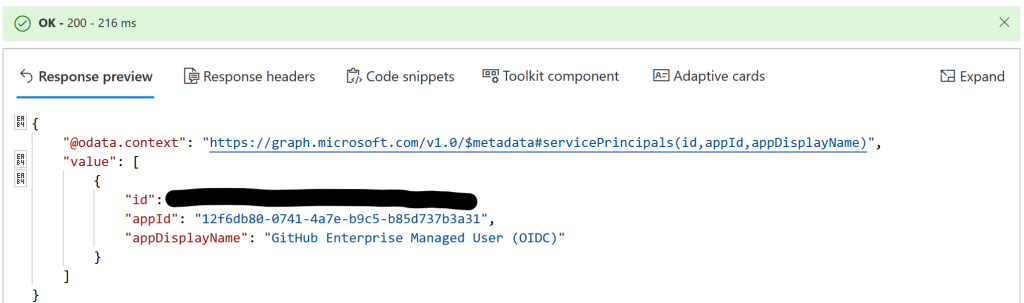
This ID is the ObjectID.
Finally, you need to assign the TokenLifetimePolicyID to the ObjectID as shown:
POST https://graph.microsoft.com/v1.0/servicePrincipals/ObjectID/tokenLifetimePolicies/$ref
{
"@odata.id":"https://graph.microsoft.com/v1.0/policies/tokenLifetimePolicies/TokenLifetimePolicyID"
}
Replace ObjectID in the POST URI with the actual ObjectID of the application and the TokenLifetimePolicyID in the JSON body:
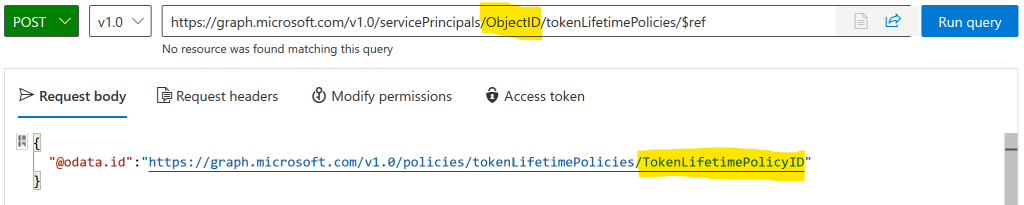
Replace the highlighted text with your policies and Run Query.
Once this is done you can run a GET query to see the linked policy:

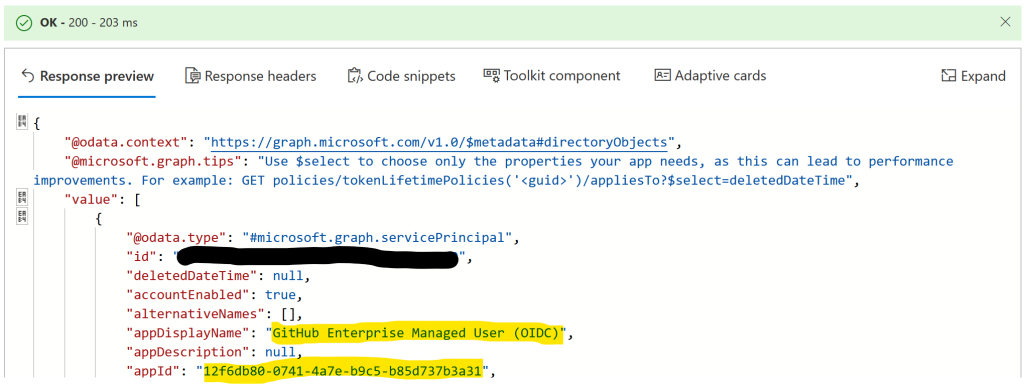
Your developers will see one more sign-in prompt within the hour, and after that will receive an ID Token with a length of the new policy, and so less sign-in prompts.

Leave a Reply