Category: Exchange Server
-

Calendar Sharing In Exchange Online After Multi-Tenant Organizations (MTO) Is In Place
When you configure a Multi-Tenant Organization (MTO) relationship in Microsoft 365 one of the configurations that it can put in place for you is an Exchange Organization Relationship. This relationship allows you to view the Free/Busy status of mailboxes in the other organization(s) in the MTO. But this is not sharing your calendar, though it…
-

Direct Send – What It Is, and What It Isn’t
There are a number of posts online panicking about “Direct Send” and how its the worst thing ever. These appear to have started following Microsoft’s publication of an article on how to turn it off – but lots of the articles get the basic principles wrong and therefore provide poor and inaccurate advice. The blog…
-

Exporting Named Properties From Exchange Online Mailbox
An undocumented Exchange Online cmdlet came my way the other day – the “Get-MailboxExtendedProperty”. This returns all the named properties, or extended properties in the mailbox and can be exported to a file for review: Get-MailboxExtendedProperty username | Export-CliXml MailboxExtendedProperties_username.xml A mailbox should only have a few thousand of these, but if you get too…
-

Blocking onmicrosoft.com Emails in Exchange Online Protection
There is a considerable uptick in emails from the default domain in Microsoft 365 tenants. These emails come from senders @ tenant.onmicrosoft.com and are not your tenant. Microsoft recently announced recipient external sender limits to reduce this, as the default is 10,000 recipients per day, but will get an additional restriction of no more than…
-

Post Tenant To Tenant Migration Calendaring Issues
When you perform a Microsoft 365 tenant to tenant (T2T) migration and run a migration that is either staged over some time or sometime after the migration has completed you cutover the domains from the old tenant to the new tenant (that is, you were doing a rebrand and the new tenant had a new…
-

Blocking More Obvious Phish – Attachment Filtering
One relatively easy way to block some categories of phishing email is to block the attachment type that is sent with some of these messages. For example, I have had a few of these recently: Hovering over the attachment I see the filename, and it ends .shtml. This attachment is for server-side HTML (SSI includes…
-

Exchange Hybrid Wizard – New Tenants and Missing Errors
Rumoured to be fixed end of June 2023 A short blog post on this issue – you see in the Microsoft Exchange Server Hybrid Configuration Wizard logs the following error “Connecting to remote server failed with the following error message: Connecting to remote server outlook.office365.com failed with the following error message : For more information,…
-

Managing Hybrid Exchange Online Without Installing an Exchange Server
In April 2022 Microsoft finally released the ability to manage Active Directory synced attributes (Hybrid Identity) to Azure Active Directory for Exchange without a full Exchange Server installation. Instead, you install the Exchange Management Tools (EMT). You need to install Exchange Server 2019 CU12 or later to do this, and you either uninstall your existing…
-

Outlook AutoDetect And Broken AutoDiscover
Those in the Exchange Server space for a number of years know all about AutoDiscover and the many ways it can be configured and misconfigured – if even configured at all. Often misconfiguration is to do with certificates or it is not configured at all because it involves certificates and I thought I was aware…
-
Unable To Update Defender Preferences
I was trying to add Microsoft Defender exceptions via PowerShell to a clients server (Windows Server 2016 if that matters) the other day and it was always failing – the error was: This was returning “Failed to modify preferences” on the Add-MpPreference cmdlet and the error code 0x80070073 To fix I needed to uninstall Windows…
-
Enabling Better Mail Flow Security for Exchange Online
At Microsoft Ignite 2020, Microsoft announced support for MTA-STS, or Mail Transfer Agent Strict Transport Security. This is covered in RFC 8461 and it includes making TLS for mail flow to your domains mandatory whereas it is currently down to the decision of the sender. You can publish your SMTP endpoint and offer the STARTTLS…
-
Reporting on MTA-STS Failures
This article is a follow up to the Enabling Better Mail Flow Security for Exchange Online which discusses setting up MTA-STS and in this article we cover the reporting for MTA-STS. To get daily reports from each sending infrastructure to receive reports on MTA-STS you just create a DNS record in the following format: It…
-

Enable EOP Enhanced Filtering for Mimecast Users
Enhanced Filtering is a feature of Exchange Online Protection (EOP) that allows EOP to skip back through the hops the messages has been sent through to work out the original sender. Take for example a message from SenderA.com to RecipientB.com where RecipientB.com uses Mimecast (or another cloud security provider). The MX record for RecipientB.com is…
-
Mail Flow To The Correct Exchange Online Connector
In a multi-forest Exchange Server/Exchange Online (single tenant) configuration, you are likely to have multiple inbound connectors to receive email from the different on-premises environments. There are scenarios where it is important to ensure that the correct connector is used for the inbound message rather than any of your connectors. Here is one such example.…
-
Force Mailbox Migration With Bad Items To Complete (2020)
It used to be easy to complete an Exchange Server > Exchange Online move request that had bad items, but this has changed recently. In the last short while Move Requests (and Migration Batches) have begun to include a property called DataConsistencyScore If the result from the above is “Investigate” then you will not be…
-
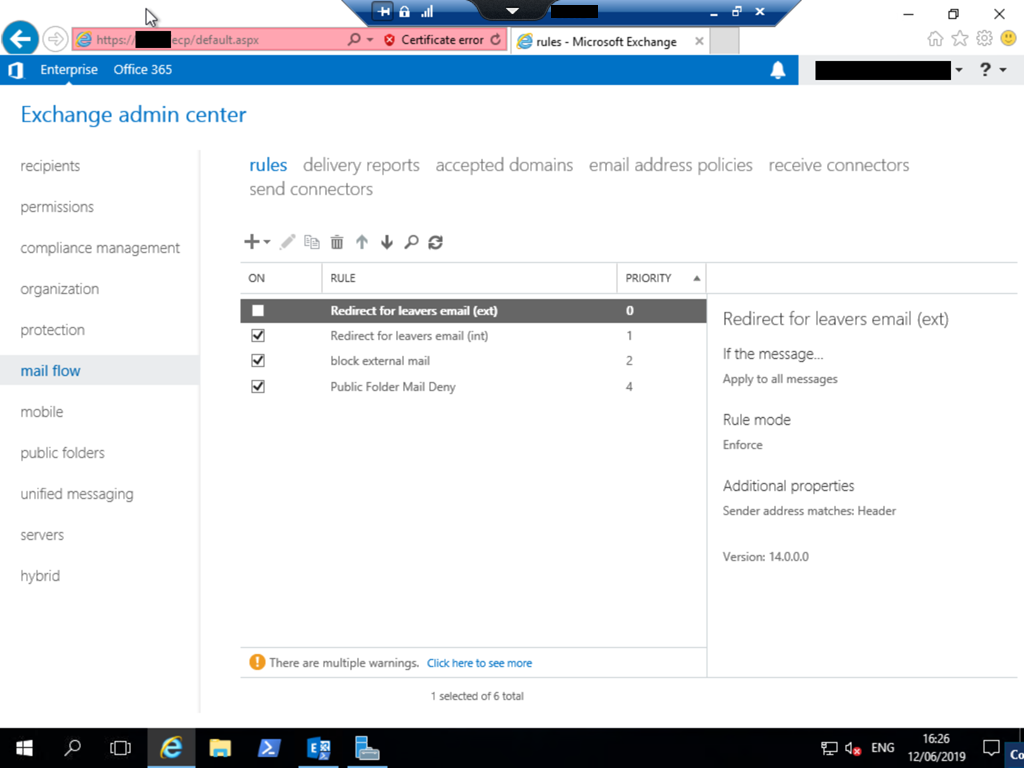
Exchange Transport Rules Corrupt On Installing New Exchange Server Version
When you install Exchange Server into an existing Exchange organization, your existing configuration typically remains intact and associated with the previous servers and some configuration, that is global in nature, also works across both versions. I can across a scenario where this does not work the other day. The scenario was the installation of Exchange…
-
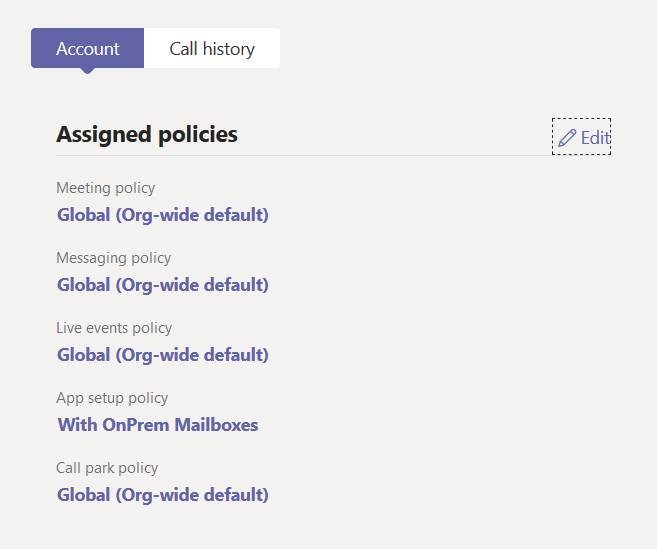
Teams Calendar Fails To On-Premises Mailbox
Article Depreciated: Microsoft now auto-hides the Calendar icon in Teams if your on-premises Exchange Server is not reachable via AutoDiscover V2 and at least Exchange Server 2016 CU3 or later. Once you move your mailbox to Exchange Online (or a supported on-premises version), assuming you did not do any of the below, your Calendar icon…
-
![Save Time! Have All Your Meetings End Early [or start late]](https://c7solutions.com/wp-content/uploads/2019/04/image_thumb-1.png)
Save Time! Have All Your Meetings End Early [or start late]
Updated April 22nd 2021 with new global default settings I am sure you have been in a meeting, where the meeting end time rolls around and there is a knock at the door from the people who want the meeting room now, as their meeting time has started and yours has finished. What if you…
-
Too Many Folders To Successfully Migrate To Exchange Online
Exchange Online has a limit of 10,000 folders within a mailbox. If you try and migrate a mailbox with more than this number of folders then it will fail – and that would be expected. But what happens if you have a mailbox with less than this number of folders and it still fails for…