Category: AzureAD
-

Enforced MFA on the Azure Portal and Emergency Access (breakglass) Accounts
An emergency access (or break-glass) account is a key design consideration of your M365/Entra tenant. This would be an account that would bypass MFA and you would store the very long and unique credentials offline somewhere. This would be used in the case of configuration breakages that would lock out all your other admins or…
-

Testing Entra ID Claims and Single Sign-On Enterprise Apps
Updated October 2024 Microsoft has removed Claims X-Ray from their website. If I get an answer to this tweet I might discover more. Meanwhile something similar to the below can be done using https://jwt.ms as the redirect URL. There is a class of Enterprise App in Entra ID (previously known as Azure Active Directory) that…
-

Inviting Google (Gmail) Users To Collaborate In Your Teams Channels
This post is not about inviting Google users to your meetings, where you just send them the meeting invite and all is good. This is about adding the Gmail user as a member of a Team, so they can see the Teams channels, chat and collaborate with files and apps along with everyone else in…
-

Is That Domain In Entra ID
Occasionally it is useful to know if a domain name is registered with a tenant in Entra ID (previously known as Azure AD). There is a URL to lookup this information as to my knowledge there is not easy portal to query. The URL requires you to add an email address, though the actual user…
-

Introduction to Microsoft Graph PowerShell SDK
This short blog post is the 10 minute demo I presented at Microsoft Ignite 2023 in Seattle. It was not recorded, but this was the slide deck that went with it. Graph SDK Additional Content.pptx The full speaking text of the presentation might be added here once the jetlag goes away!
-

Bulk Token Retrieval Failed
The Windows Configuration Designer (WCD) application (installed from the Microsoft Store) allows you to bulk convert standalone Windows 10+ clients to Azure AD Joined clients, and if you have Intune auto-enroll enabled then the client will enrol with Intune as well. But there are a number of issues with this application that result in errors…
-
Domain Tenant Move and Device Join Issues
I discovered recently an issue following a tenant to tenant Microsoft 365/Azure AD migration. The issue was that devices would not enroll with Intune in the old tenant because the settings the device was getting was mixed up between the old and new tenants. In the case I had, the new tenant was not yet…
-

Migrating MFA Settings To Authentication Methods
Released to Azure AD in December 2022 there is now a process for migrating from the legacy MFA methods and Self-Service Password Reset (SSPR) authentication methods to the unified Authentication Methods policies in Azure AD. This migration window is open until September 2025 (originally January 2024) when the legacy methods will be disabled. This change…
-

Conditional Access Authentication Strengths
Newly released to Conditional Access in Azure AD is the “Authentication Strengths” settings. These allow you to control the strength of the authentication you need to be used for that conditional access rule. Before this feature was available you had the option of allowing access with no second factor, MFA as a second factor (any…
-

Improving Security For MFA Approvals – Number Matching
Rolling out in November 2021 is a new feature – that of requiring the user to enter a number rather than just click approve on the MFA prompt. This update to Azure AD requires the use of Push Notifications and therefore requires the use of the Microsoft Authenticator app. It also requires that MFA is…
-

Adding Location To Azure AD MFA
This Azure AD feature is something that a number of other Multi-Factor Authentication providers have already implemented – that of showing the location of the user login (and the app in use) on the MFA prompt. This feature rolled out to Azure AD in mid November 2021 in preview – so use in non-production tenants…
-
Why Do Comments In Microsoft 365 Planner Disappear?
So first you need an Exchange Online mailbox for comments to work. Comments to the tasks of Plans are stored in the Microsoft 365 Group mailbox, and you need an Exchange Online mailbox to access the M365 Group mailbox. Behind the scenes, or actually not that behind the scenes, the process for comments is as…
-
MFA, Admin Roles and AADConnect Sync Failures
Come Feb 29th 2020 and Microsoft are turning off the baseline security policies. If you used these policies to do MFA for all admins (as that was an easy way to achieve this), then a replacement Conditional Access rule might cause errors with AADConnect. The reason being is that you could create a new Conditional…
-
Baseline Policy Replacements: Conditional Access MFA for Administrators
From Feb 29th 2020 Microsoft will remove the “baseline policies” from Azure AD. These were very useful in the past to enable blanket settings like MFA for all admin accounts (well, selected admin roles) and to disable legacy auth for the same admin roles. With the removal of the baseline policies you need to ensure…
-
MFA and End User Impacts
This article will look at the various different MFA settings found in Azure AD (which controls MFA for Office 365 and other SaaS services) and how those decisions impact users. There is lots on the internet on enabling MFA, and lots on what that looks like for the user – but nothing I could see…
-
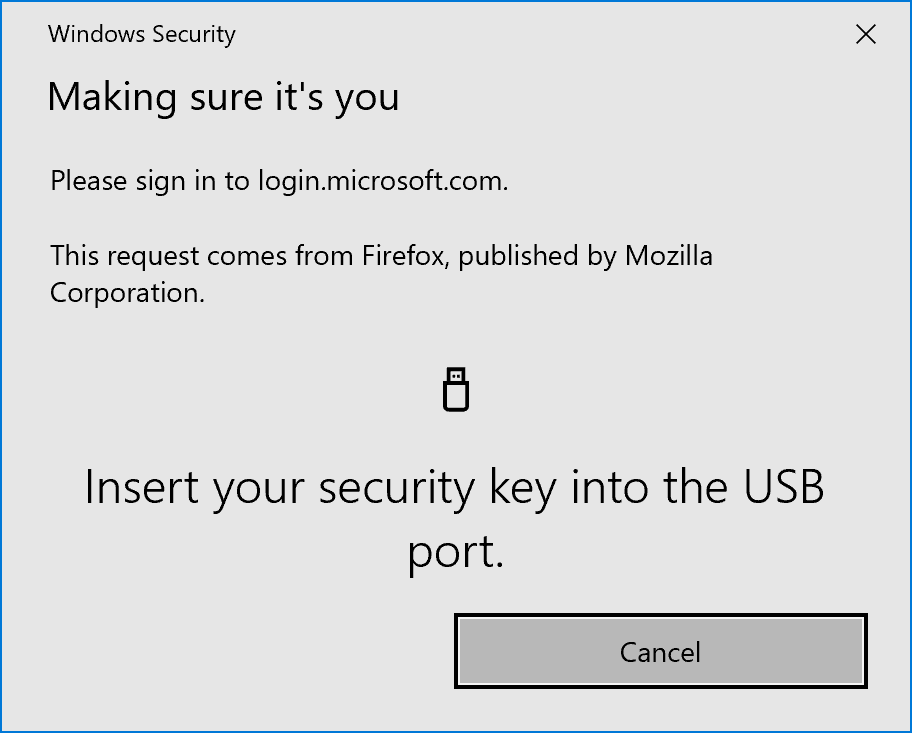
Getting Rid of Passwords in Azure AD / Office 365
This article is based on the public preview of the use of hardware tokens/Microsoft Authenticator to do sign-in without passwords released in July 2019 Using Microsoft Authenticator for Passwordless Sign-in You used to be able to do this by running the following in PowerShell for the last few years New-AzureADPolicy -Type AuthenticatorAppSignInPolicy -Definition ‘{“AuthenticatorAppSignInPolicy”:{“Enabled”:true}}’ -isOrganizationDefault…
-
Decommission ADFS When Moving To Azure AD Based Authentication
I am doing a number of ADFS to Azure AD based authentication projects, where authentication is moved to Password Hash Sync + SSO or Pass Through Auth + SSO. Once that part of the project is complete it is time to decommission the ADFS and WAP servers. This guide is for Windows 2012 R2 installations…
-
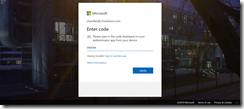
Hardware Tokens for Office 365 and Azure AD Services Without Azure AD P1 Licences
A recent update to Azure AD Premium 1 (P1) licence has been the use of hardware tokens for multi-factor authentication (MFA). This is excellent news if your MFA deployment is stuck because users cannot use phones on the shop floor or work environment or they do not want to use personal devices for work activities.…
-
Token2 Hardware OAuth Tokens and Azure AD Access
This blog post walks through the process of logging into Azure AD resources (Office 365, other SaaS applications registered in Azure AD and on-premises applications that utilise Azure AD App Proxy). First step is to order your desired hardware. For this article we are looking at the devices manufactured by Token2 (www.token2.com). These include credit…

