The Windows Configuration Designer (WCD) application (installed from the Microsoft Store) allows you to bulk convert standalone Windows 10+ clients to Azure AD Joined clients, and if you have Intune auto-enroll enabled then the client will enrol with Intune as well.
But there are a number of issues with this application that result in errors when trying to obtain a bulk primary refresh token (BPRT). So this article will outline those I know about (have experienced) and one which I cannot see written down anywhere else. And in the meantime we will look at how bulk tokens are obtained.
The WCD designer is designed for use in schools and education establishments, but is useful where you have lots of unmanaged devices and want to avoid adding them to Entra ID (previously known as Azure AD) manually, but this is useful for bringing into management devices such as digital signage, conference room equipment, and “work from home” devices issues during COVID19 lockdowns. Adding them manually means you are the primary user of the device in Intune and there are device limits, sharing of credentials etc that need to be dealt with. The WCD allows you to create a provisioning package that contains a token that can be used in bulk on many machines and to add these machines to Entra ID as Azure AD Joined devices.
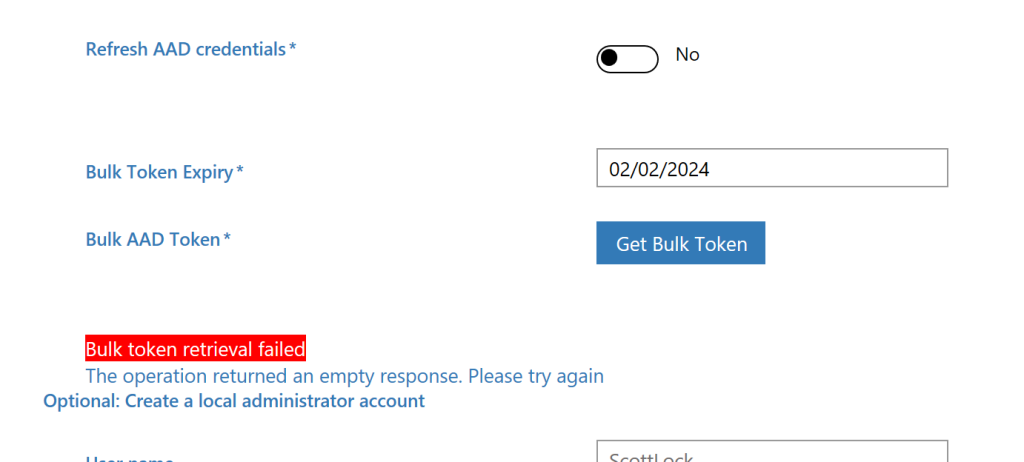
Running the “Get Bulk Token” button in the WCD wizard can result in the following errors:
- Bulk Token Retrieval Failed: The Operation Returned An Empty Response
- Bulk Token Retrieval Failed: Bad Request
The first of these errors is seen in the Windows Store version of the app and the second in the Windows ADK version of the app. Both are fixable (though newly tenants may fail for a different reason)!
Behind The Scenes
To discover these issues and what your particular problem with bulk token retrieval is, you need to look at a couple of log files. The first is ICD.log in the same folder as the files the WCD is creating and the second is the sign-in log folder in Entra ID.
Behind the scenes of WCD and Bulk Token Retrieval there is a series of events that you need to understand to troubleshoot this correctly. First you need to login with a user with the correct rights, and second you need to know that it is not your user account that is doing the token retrieval.
The account that you need to login with for Bulk Token Retrieval needs to be one of the following Entra ID role holders:
- Global Administrator
- Cloud Device Administrator
- Intune Administrator
- Password Administrator
And once you have logged in, a new user account called Package_GUID is created (where the GUID is the ID of WCD package you are creating). This Package_GUID is the Display Name of the account, and each time you login and fail to create a new package, a new account is created. The User Principal Name (UPN) of this account is different every time.
The errors are recorded in the ICD.log for problems at the above two points. The first is the wrong privilege role and the second is MFA required for device join:
Wrong Roles For WCD User
date time Error Bulk token retrieval failed: {"error":"invalid_request","error_description":"AADSTS240005: Missing required user role to acquire a bulk AADJ token. For more information please go to https://go.microsoft.com/fwlink/?linkid=2224591.\r\nTrace ID: GUID\r\nCorrelation ID: GUID\r\nTimestamp: date time","error_codes":[240005],"timestamp":"date time","trace_id":"GUID","correlation_id":"GUID"}
MFA Required To Join Device
date time Error Bulk token retrieval failed: {"error":"invalid_request","error_description":"AADSTS240004: Authorization code not received from authorize endpoint call. Error: AADSTS50079: Due to a configuration change made by your administrator, or because you moved to a new location, you must enroll in multi-factor authentication to access '01cb2876-7ebd-4aa4-9cc9-d28bd4d359a9'.\r\nTrace ID: GUID\r\nCorrelation ID: GUID\r\nTimestamp: date time\r\nTrace ID: GUID\r\nCorrelation ID: GUID\r\nTimestamp: date time","error_codes":[240004],"timestamp":"date time","trace_id":"GUID","correlation_id":"GUID"}
The first of these is easy to fix – make sure you have the correct roles for the job you are attempting to do. The second is harder to fix, and is the main subject of the rest of this blog
Device Registration Issues
The token that the wizard obtains for you to join many machines to Entra ID is a token that allows a device to be registered in Entra ID. If you have any restrictions on device registration then the obtaining of the token will fail with the above. This includes blocks on device registration and Conditional Access rules that require MFA to join a device. You can check these from the Device Settings pane of the Entra ID portal as shown:
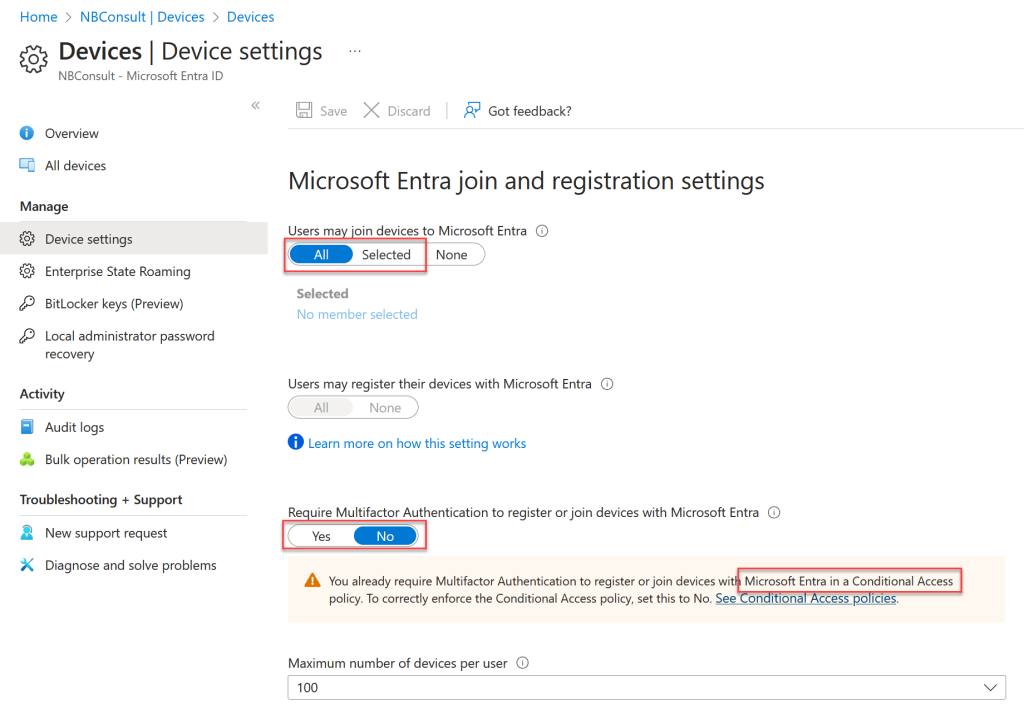
In the above screenshot all users can join devices to Entra. If this was “Selected” it would need to include the Package_GUID user, but given that this is created and the token obtained all in the matter of a few seconds, you cannot add the user and then obtain the token – so this value needs to be “All”. I tried to create a Dynamic Group (DisplayName StartsWith “Package_”) but the user is not added to the group fast enough for the join right to be granted in time for the wizard.
If you have MFA enabled for device join (which you absolutely should) then the Package_GUID account will fail to get the bulk token as it cannot register for MFA. And like the dynamic group suggestion above, it cannot be added to any Conditional Access rule exclusions in time to work as well, as its is a newly created account.
Therefore you either need to turn off the requirement for MFA for device join for the whole tenant for the five or so minutes that it takes the change to take effect and in which you can login to WCD and retrieve a Bulk Token. Remember to turn it on again afterwards! Or, implement a Conditional Access rule for device registration or join and exempt either the network location where you are performing the WCD wizard steps or the account that performs the actions. If you are working from home to do this, you could even exclude your location and not impact anyone else. This is shown in the following screenshot:
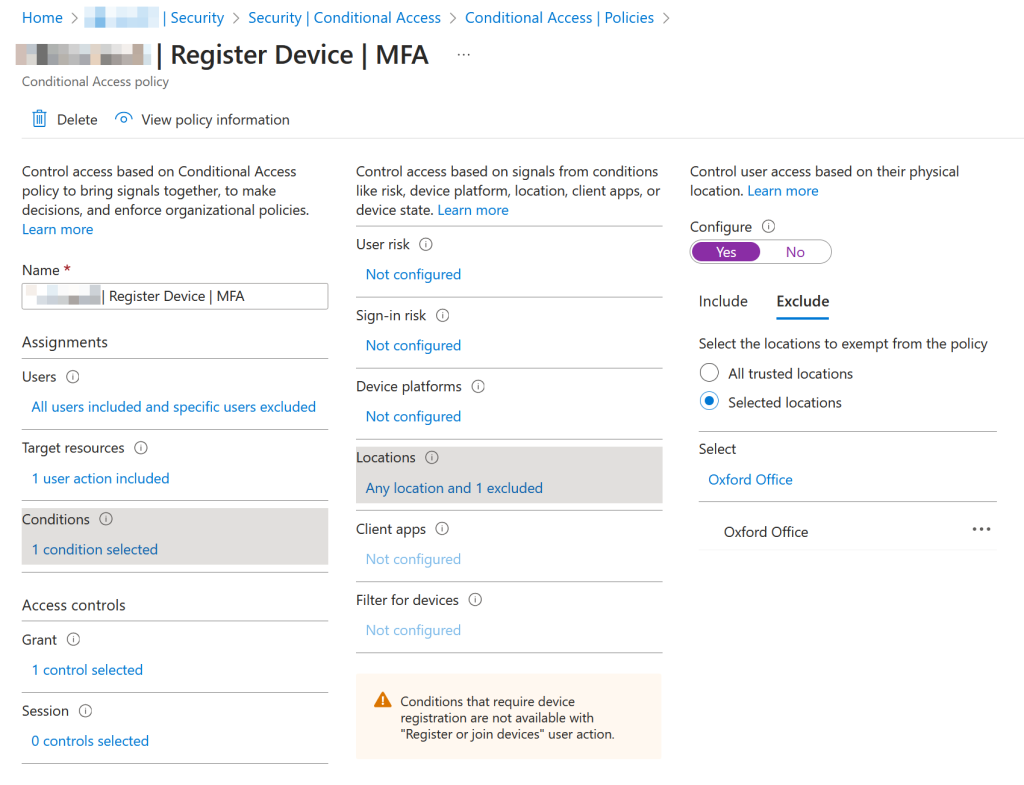
As for the account that performs the actions of creating the “package” user, this is the Microsoft.Azure.SyncFabric service principal and this could be exempt from the Conditional Access rule along with your user account.
Note there is a case where the Microsoft.Azure.SyncFabric service principal can be missing in your tenant and this will also break bulk token creation, so read this post by my NBConsult colleague Thomas on LinkedIn on how to check and create this service principal if needed.
As above, remove the exclusion to the rule once the WCD wizard is complete.
Once you have retrieved the bulk token, complete the steps of the wizard and create the package file that you can use to bring your various devices into management.
Image Generated with AI ∙ 6 October 2023 at 11:54 am

Leave a Reply