Category: Multi-Factor Authentication
-

Easy Sign-In to Entra ID Applications for Frontline Workers With QR Codes
I had the pleasure of staffing the Microsoft Entra stand at the 2025 Microsoft Ignite conference. 17,000 people and the ability for anyone to come and ask their Entra questions and we got lots. It was fun. One of the questions asked was by a gentleman who had users on a factory floor and who…
-

Onboarding New Users In an Entra ID Passkey World
This blog covers the scenario of onboarding new users (or users who have their MFA methods reset) when a passkey is the only required option for authenticating You might wonder why a passkey only world environment might be set up in Entra ID, and though at the time of writing most administrators and organizations will…
-

Configuring and Migrating From Entra ID Custom Controls to External Authentication Methods
Custom Controls date back to the Azure AD days and the ability to link an external MFA provider into authentication but without the full step of federation. This feature was in preview for years and never left preview, and was limited to I think three companies. Over the years I have seen this a number…
-

Bulk Token Retrieval Failed
The Windows Configuration Designer (WCD) application (installed from the Microsoft Store) allows you to bulk convert standalone Windows 10+ clients to Azure AD Joined clients, and if you have Intune auto-enroll enabled then the client will enrol with Intune as well. But there are a number of issues with this application that result in errors…
-

Migrating MFA Settings To Authentication Methods
Released to Azure AD in December 2022 there is now a process for migrating from the legacy MFA methods and Self-Service Password Reset (SSPR) authentication methods to the unified Authentication Methods policies in Azure AD. This migration window is open until September 2025 (originally January 2024) when the legacy methods will be disabled. This change…
-

Conditional Access Authentication Strengths
Newly released to Conditional Access in Azure AD is the “Authentication Strengths” settings. These allow you to control the strength of the authentication you need to be used for that conditional access rule. Before this feature was available you had the option of allowing access with no second factor, MFA as a second factor (any…
-
MFA and End User Impacts
This article will look at the various different MFA settings found in Azure AD (which controls MFA for Office 365 and other SaaS services) and how those decisions impact users. There is lots on the internet on enabling MFA, and lots on what that looks like for the user – but nothing I could see…
-
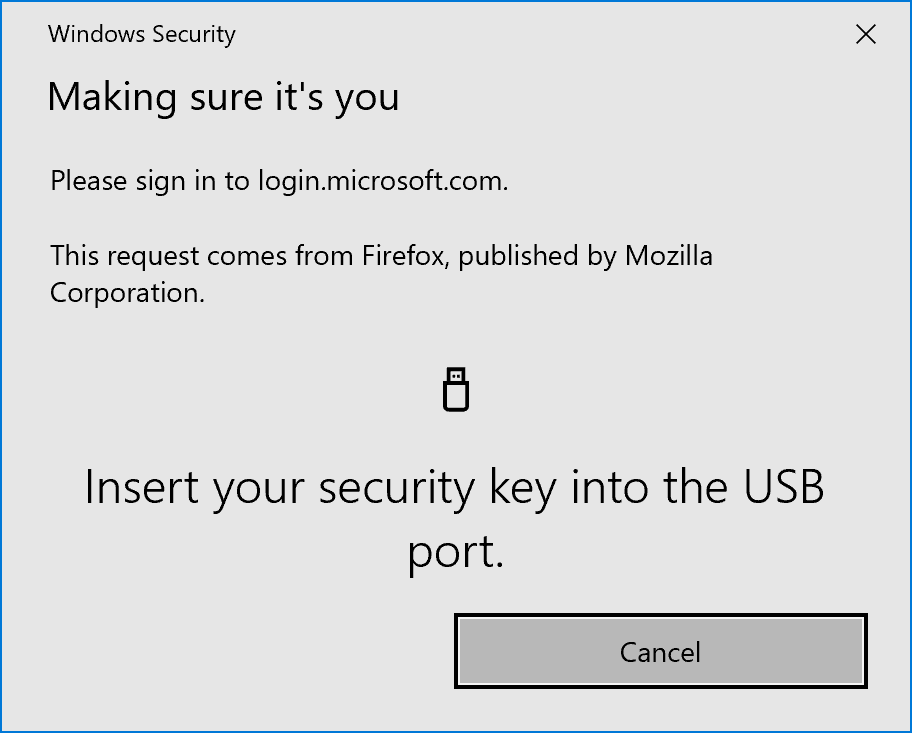
Getting Rid of Passwords in Azure AD / Office 365
This article is based on the public preview of the use of hardware tokens/Microsoft Authenticator to do sign-in without passwords released in July 2019 Using Microsoft Authenticator for Passwordless Sign-in You used to be able to do this by running the following in PowerShell for the last few years New-AzureADPolicy -Type AuthenticatorAppSignInPolicy -Definition ‘{“AuthenticatorAppSignInPolicy”:{“Enabled”:true}}’ -isOrganizationDefault…
-
Hardware Tokens for Office 365 and Azure AD Services Without Azure AD P1 Licences
A recent update to Azure AD Premium 1 (P1) licence has been the use of hardware tokens for multi-factor authentication (MFA). This is excellent news if your MFA deployment is stuck because users cannot use phones on the shop floor or work environment or they do not want to use personal devices for work activities.…
-
Customizing ADFS To Match Azure AD Centered User Experience
Back in December 2017 the User Experience (UX) for Azure AD login changed to a centered (or centred, depending upon where in the world you speak English) login page with pagination. Pagination is where you enter the username on one screen and the password on the next. This was covered in new Azure Active Directory…
-
Azure MFA 503 Error When Authenticating
If you have installed version 7 of Azure MFA Server on-premises (7.0.0.9 or 7.0.2.1 at the time of writing) and have enabled IIS authentication with Forms Based authentication and the Native App, but when you need to authenticate you are presented with a 503 DLL error. The reason for this is that version 7 removed…
-
Upgrading Azure Multi-Factor Authentication Server
A new version of Azure MFA Server was released at the end of March 2016, version 7.0.0.9. This provides an in place upgrade to the previous version 6.3.1.1. This version is based on .NET 4.5 and not .NET 2.0, which is the big change in the product, along with new end user functionality in the…
-
Installing Azure Multi-Factor Authentication and ADFS
I have a requirement to ensure that Office 365 users external to the network of one of my clients need a second factor of authentication when accessing Office 365 resources from outside the corporate network. The free Multi-Factor Authentication (MFA) feature of Office 365 will not distinguish between network location so we need to enable…
-
ADFS Adapter Issues With Upgrading MFA 6.3.1 to Version 7
Upgrading the ADFS Adapter is not straight forward, though the readme notes for the upgrade make no mention of issues! To upgrade MFA Server 6.3.1 to 7 (so you can remove .NET 2 as a requirement, as that goes out of support soon) then you need to download the MFA installer to each MFA server…
-
Office 365 MDM (Mobile Device Management) From A Users Perspective
The following list of steps and screenshots are taken during the enrolment process to add an iPhone and an Android phone to Office 365 once the free MDM solution that comes with Office 365 is enabled for the user. Step Details Image from iPhone Image from Android 1. Once your IT Administrator enables MDM for…
-
How To Change Your Office 365 App Password
If you are enabled for Multi-Factor Authentication (MFA) in Office 365 then you will need an App Password for some applications that do not support MFA. The user interface for creating a new App Password is well hidden in Office 365 (its not on the Password page for example). Post updated in 2016 to take…
