There are various buttons in the Entra ID portal that can be used in the event of an incident with a user account, but each have different effects and can be used in different circumstances. This blog post outlines the impact of each button on the user.
To do these tests I performed a standard login. I logged in both on an on-premises, hybrid joined Windows client and a seperate in-private browser session on an unrelated machine. The first completed SSO and signed in the user with only an MFA prompt (push notification to Microsoft Authenticator app) and the second required the username, password and MFA prompt. Both browsers were logged into the Office Portal (https://portal.office.com) before any of the following actions, and upon completion of the action and recording the effect, they were logged out and logged in again before the next test.
Additionally for the in-private session, Keep Me Signed In was checked and “Yes” choosen (which persists the login token/cookie), even though its an in-private (incognito) session and closing the browser wipes all tokens/cookies.
As mentioned above, there are various buttons in various portals. We will start with the Authentication Methods for a user – Entra Portal > Users > select a user > Authentication Methods
Reset Password
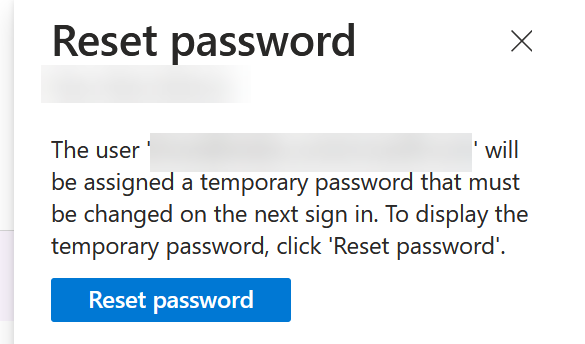
This one is a bit obvious, but for completeness, this button in the Entra ID portal under both the User Overview page and the Authentication Methods page will change the users password to a suggested new password and require the user to change it again at first login. There is no option here for the administrator to say what the new password will be nor an option so that the user does not require their own password change. So actually, compared to the Microsoft 365 Admin Center where this is totally the opposite behaviour, this is not that obvious really!
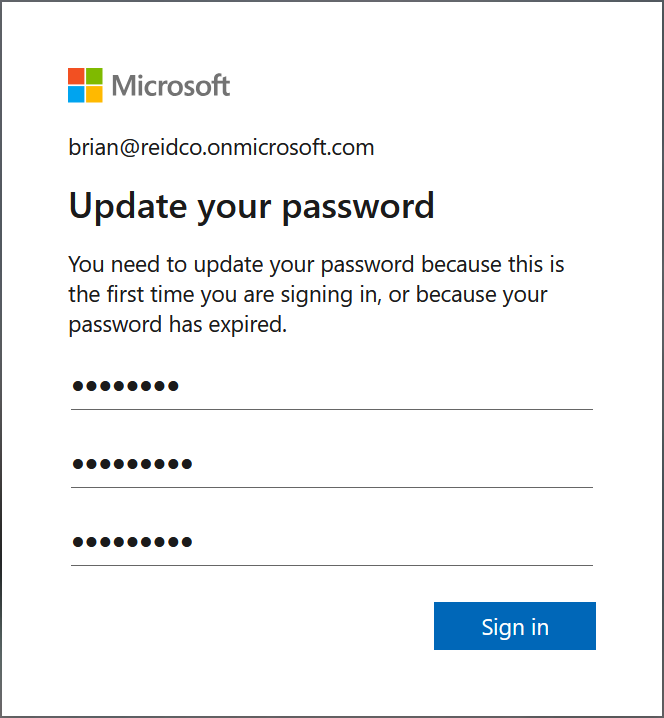
Require re-register multifactor authentication
Pressing this button should require the user to complete MFA registration. Additionally it will deactivate hardware OATH tokens and delete the following authentication methods from this user: phone numbers, Microsoft Authenticator apps and software OATH tokens. This is ideal in situations where the user has lost all their MFA methods for authentication (i.e. a new phone and dont have the old one) becuase once MFA is configured for a user, the easiest way to add new methods is to sign and on the My Account page to add new methods. The add new methods page will require completion of an existing MFA method. So if the user does not have available any old method and options like SMS have been disabled (so a text to an existing number cannot be sent) then pressing “Require reregister MFA” will give the user an option to add new methods and have the old methods removed. This is also useful when an account has been taken over and the malicious actor has added their own methods as well (a common event in my experience).
Note that this button will not always cause the user to reregister their account. Testing showed that if the user has a passkey then this keeps working, but other methods having been removed means that this is the only way to login. If a user has a passkey then this will still work to sign the user in. To get the user past the passkey requirement and to force the user to visit the MFA registration portal you need to issue the user a TAP.
This button differs from just issuing a TAP (Temporary Access Pass) for the user because although that allows the user to register new methods, a TAP does not remove the old methods (though it warns you to do this). Therefore, you might need to do a TAP and force reregister (if the user has passkeys including Windows Hello) if you need the user to reregister. To add a TAP ensure that it is enabled via the new Authentication Methods page and click “Add authentication method”. After the user uses the TAP to login, direct them to https://aka.ms/mysecurityinfo to update any MFA method required.
Revoke multifactor authentication sessions
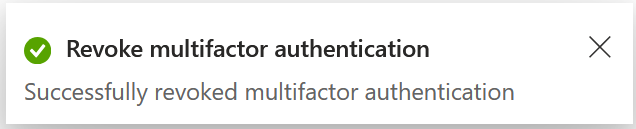
This has no effect on browser based sessions, but will require you to redo MFA in applications. In a single test of many I did for writing this blog post, the Edge browser also signed out on the first press of the button but I could only get this to repeat in frequently.
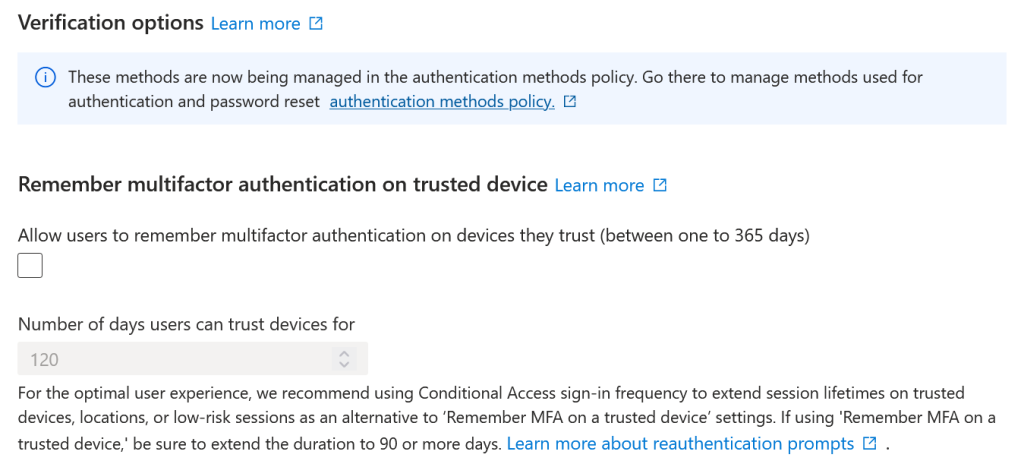
For tenants not yet migrated to the modern Authentication Methods policies there is the option to “Remember MFA on trusted device”. This button in the Entra ID portal to revoke MFA sessions will cancel this saving of MFA on trusted devices. Therefore, only on “trusted devices” where the user has previously checked to keep their MFA session for x days will this session not be kept and be re-prompted for. The user is not asked to reregister their MFA methods but only to provide MFA again at next login.
View authentication methods policy
This button shows the effective authentication policy for the selected user. This is based on the new Authentication Methods migration process and does not include legacy settings.
On the Entra ID portal, Users > select your user, you get to the Users Overview page. On this page there is a “Revoke Sessions” button. This is the button that often should be used along with your selected option above. Revoking a session makes the login token invalid, updates the earliest time a token can be valid from to the current date/time and then as this means the current token is invalid, the user is signed out. This could be next to instantaneous in apps like Exchange Online and Teams, or within the hour on any app that does not use Continious Access Evaluation (CAE). On the users Properties page you can see their “Sign in sessions valid from date” property. Click “Revoke session” and this will change to the current time. The user will need to sign in again within the hour but immediately in Teams, SharePoint and Outlook.
Photo by Life Of Pix: https://www.pexels.com/photo/brass-colored-metal-padlock-with-chain-4291/

Leave a Reply to S Cancel reply