Or “How to customize Microsoft 365 Preset Security Policies“!
The Preset Security Policies in Microsoft 365 allow you to assign to users, groups or domains the recommend anti-spam, anti-spoofing and anti-malware settings (amongst others). In the Microsoft 365 Security Portal (https://security.microsoft.com) where you set this there appears to be no way to customize these policies – and part of that is the point. Microsoft change and manage the policy for you.
But you might have a reason to do this, and one such reason is when you have Microsoft Teams Rooms and Direct Guest Join enabled. Direct Guest Join is when people use WebEx or Zoom to run meetings and you want this meeting displayed on your Microsoft Teams Room conference equipment.
Microsoft Teams Rooms detect the 3rd party conference service by checking the URL in the meeting invite, and as the meeting invite can be sent by the original sender or forwarded to the room by a recipient we need to ensure that Safe Links does not rewrite external or internal meeting invites for a select series of URLs.
Zoom Rooms have exactly the same process, except they show Zoom natively and meetings in other software via the web browser – for example Teams Meetings can be shown in a Zoom Room.
If you are not using Preset Security Policies you can add these exceptions to your policy as shown:
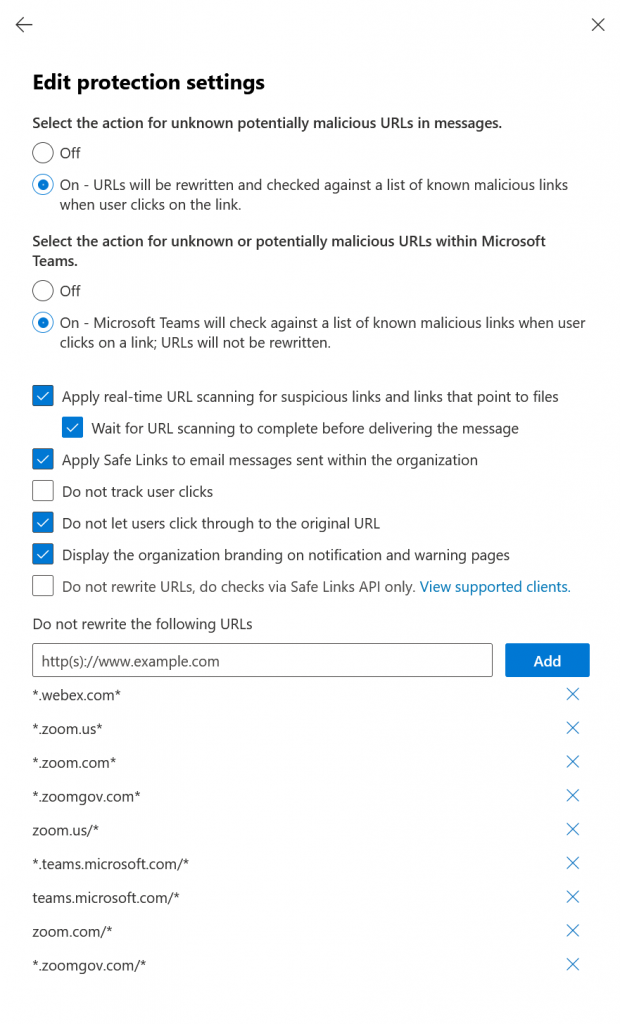
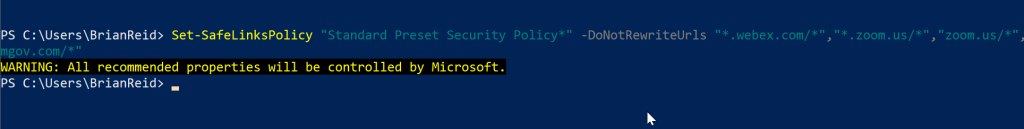
But with Preset Security Policies in place you need to use Exchange Online PowerShell to write the above exception to the three preset policies (after you have created the first two of them using the GUI and the last one is the auto-created policy to protect all users that is new to M365 at the time of writing).
Set-SafeLinksPolicy "Standard Preset Security Policy*" -DoNotRewriteUrls @{Add="*.webex.com/*","*.zoom.us/*","zoom.us/*","*.teams.microsoft.com/*","teams.microsoft.com/*","zoom.com/*","*.zoom.com/*","*.zoomgov.com/*","*.bluejeans.com/*"}
Set-SafeLinksPolicy "Strict Preset Security Policy*" -DoNotRewriteUrls @{Add="*.webex.com/*","*.zoom.us/*","zoom.us/*","*.teams.microsoft.com/*","teams.microsoft.com/*","zoom.com/*","*.zoom.com/*","*.zoomgov.com/*","*.bluejeans.com/*"}
Set-SafeLinksPolicy "Built-In Protection Policy" -DoNotRewriteUrls @{Add="*.webex.com/*","*.zoom.us/*","zoom.us/*","*.teams.microsoft.com/*","teams.microsoft.com/*","zoom.com/*","*.zoom.com/*","*.zoomgov.com/*","*.bluejeans.com/*"}
You will get a warning back saying “WARNING: All recommended properties will be controlled by Microsoft.” so it is possible that Microsoft will overwrite these “DoNotRewriteUrls” values at a later time – but for now, this works. The above PowerShell will append the suggested URLs to any existing URLs you have already added.
For Teams Rooms you need the SafeLinks rewrite exempting the other products, i.e. Zoom, WebEx, Bluejeans etc. For Zoom Rooms you need to include Teams URLs in the exception list.
When you use URL rewriting in other products, for example Mimecast, you may also find functionality in Teams and Teams Rooms breaks – for example I have seen cases where the Join button in Teams does not work because the link has been rewritten. Therefore, ensure that the above URLs are exempt from all the products you have on your estate that rewrite URLs.
Photo by Mike Bird: https://www.pexels.com/photo/silver-chain-145683/

Leave a Reply