Category: MDM
-
Adding Apple Well-Known RemoteManagement JSON to IIS Web Servers
To do Account driven BYOD device enrolment in Intune for iOS devices you need to publish to the website on your domain a JSON file that contains your tenant ID. The URL for this file is https://c7solutions.com/.well-known/com.apple.remotemanagement where the domain (c7solutions.com in this case) is the same as the domain of the username on the…
-

Enabling BitLocker In Silent Mode Using the Settings Catalog (2023)
There are many blog posts and articles online about the old way to configure silent BitLocker. These used a template that Microsoft added to Intune. Since March 2023 BitLocker has moved (along with lots of other configurations) to using the Settings Catalog. Often the settings are similar and you can take a old blog post…
-

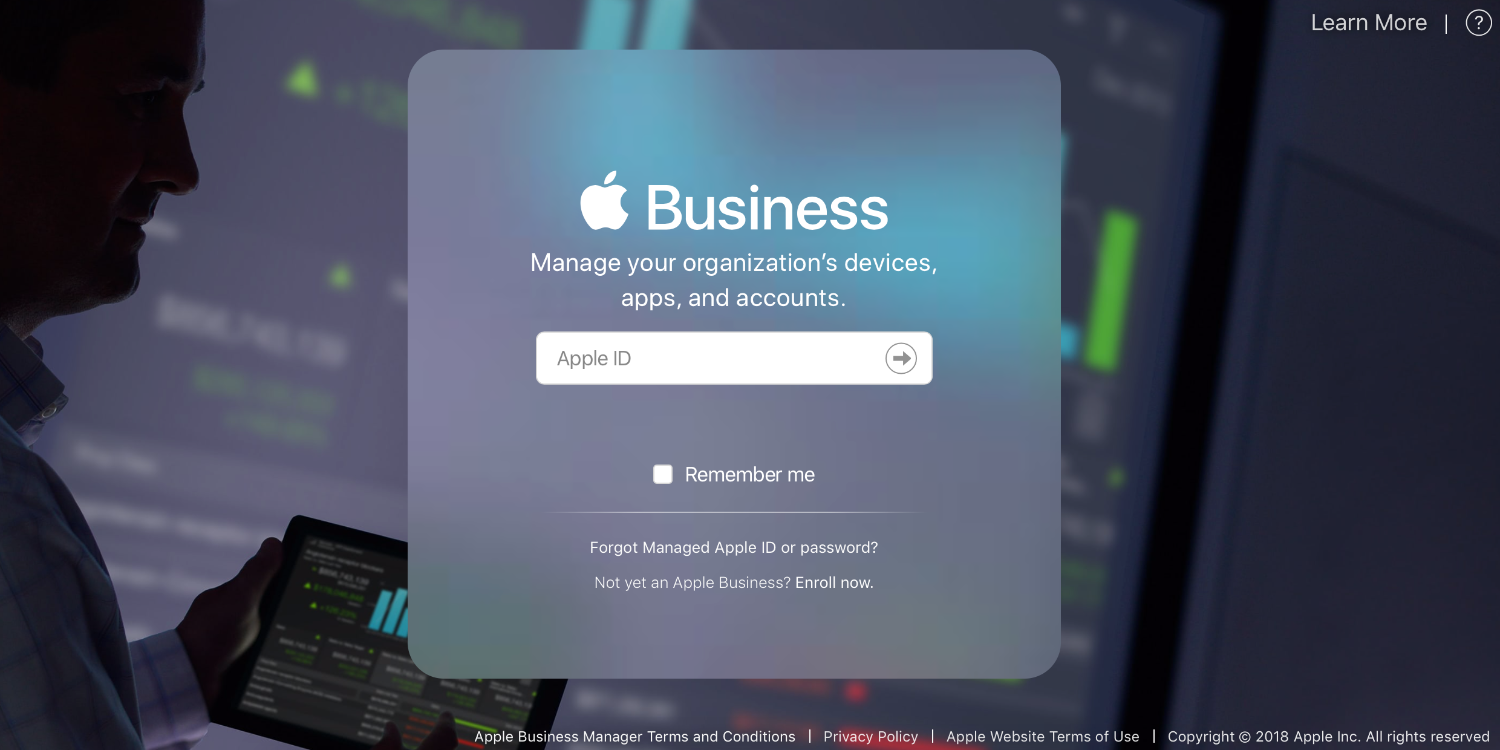
Adding App Tokens To Intune From Apple Business Manager (VPP)
Documentation on this process is hard to come by. Either Microsoft says “download the Apple Business Manager location token (Apple VPP token) for your account” but does not say how, or other documentation covers other bits of the process, but not this step. So, how do you download and create a Apps Content Token so…
-
Blocking Apps With a Low Reputation
One of the benefits of Microsoft 365 is the interaction across many products and features to create services that otherwise you might not have available to you or need to implement unrelated and unconnected additional software and maybe client agents as well. Recently announced is an interaction between Windows Defender (client AV and other security…
-
Renewing Apple APN for Office 365 Mobile Device Management
Office 365 MDM (Mobile Device Management) allows you to manage iOS based Apple devices. Once you have had Office 365 Mobile Device Management is use for a year, the Apple APN certificate that you would have created a year ago for this purpose will expire. If you did not add this renewal date to your…
-
Office 365 MDM (Mobile Device Management) From A Users Perspective
The following list of steps and screenshots are taken during the enrolment process to add an iPhone and an Android phone to Office 365 once the free MDM solution that comes with Office 365 is enabled for the user. Step Details Image from iPhone Image from Android 1. Once your IT Administrator enables MDM for…