Note – the functionality described on this page will change from April 2025. When your Intune tenant is updated to version 2504 then you will get new settings in the App Protection Policy to control the below and various iOS AI tools (Genmoji and Writing Tools). For more, see the end of this article.
A new feature to Intune managed iOS devices, via App Protection Policies, is the ability to block screenshots (“screencapture” in Apple’s terminology). This has started to become available since the end of November 2024 and was mentioned in Message Center MC907517, though this article targeted developers and not administrators.
Microsoft has released two new versions of the Intune SDK for iOS apps (see here), one for developers using Xcode 15 and another for developers using Xcode 16. Upon updating to v20.2.1 (or v19.7.6 if using Xcode 15) a new feature of the SDK is that screen capture can be blocked.
This restriction is enabled via an App Protection Policy in Intune, and may well already be in place in your tenant if you have created an App Protection Policy in the past. If any Intune App Protection Policy that you have created and applies to the user has “Send org data to other apps” set to any setting other than “All Apps” then the restriction will be in place and will take effect as soon as you update to an app that was compiled with the new version of the SDK.
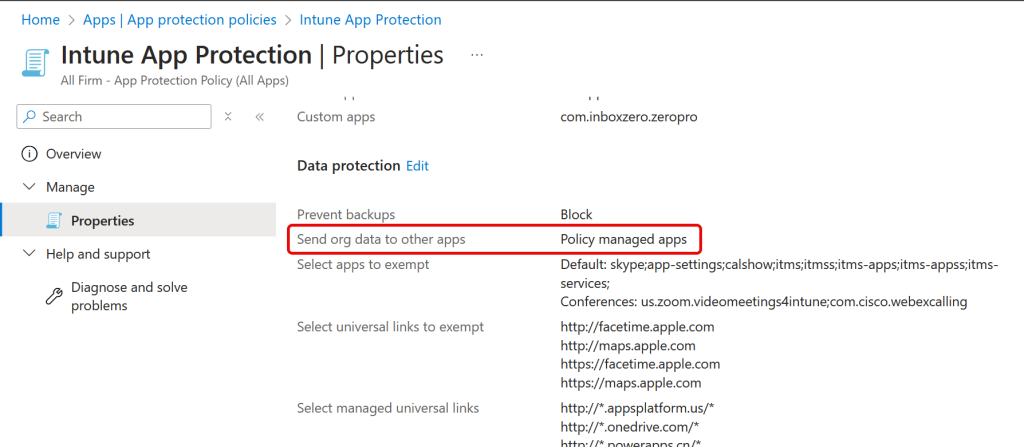
Your first experience of this is likely in the Outlook mobile app. My experience as I write this blog post on 3rd December 2024 is that Word, Excel and the Microsoft 365 (Office) apps are yet to block screen capture, but that Outlook and Planner both do. And the same will be true for any other app that uses the Intune SDK when compiling its apps (for example Zoom for Intune). As each of these apps are recompiled and then released to the Apple App Store, and then update on your device, the block screen shot functionality will appear with them (or possibly never appear if the developer never updates the SDK). So, if you are an app developer reading this post, please recompile your app to the latest SDK and release it for download so that it’s screen grab and screen recording behaviour is consistent with end user expectations.
You are able to tell what Intune SDK version is used with an app, and to see the settings that are applied to the app from the device itself. This will help with any troubleshooting. In the Edge browser (and it needs to be Edge, not Safari etc) browse to “about:intunehelp“. This will show the Intune Diagnostics page, and on this page select “View Intune App Status”. Then from the app names wheel at the top of the page, scroll to the app you are interested in. The below picture has “com.microsoft.Office.Outlook” (aka Outlook Mobile app) selected. You can see the “Intune SDK Version” is at 20.1.2 in my screenshot, and as this is not the latest version of the SDK at the time of writing, my Outlook app is able to do screenshots. Once this changed to 20.2.1 (sorry, I don’t pick the version numbers) then screen recording/screenshots will generate a blacked out (redacted?) screenshot stored in your photos folders. This happened for me when I updated the Outlook app on my phone.
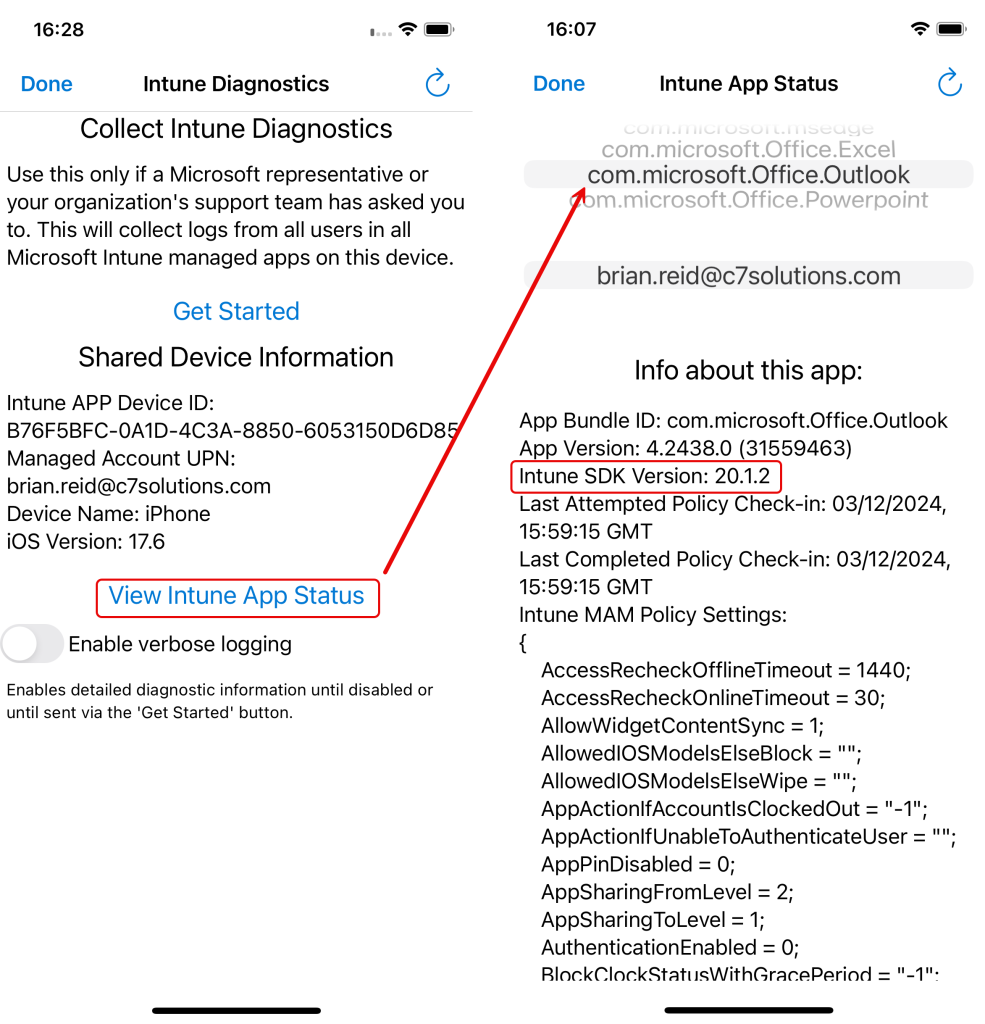
You can scroll down all your apps to see the SDK version for any Microsoft app that was ever installed on your phone. Ensure that all your apps are updated from the App Store before you do this to get the latest results, and ignore entries for any app that is listed but you have uninstalled.
For a more central approach, an Intune admin can see all the app versions and SDK versions from the Microsoft Intune admin center by navigating to Apps > Monitor > App protection status, then review “Platform version” and “iOS SDK version”.
Talking of Excel and Word, as we were above, also at the time of writing these apps were compiled to version 19.7.1 of the SDK, which was released end of Sept 2024 – so on this basis it could be a number of months before they update to SDK 20.2.1 or later, and that is only my guess! Teams and Microsoft 365 (Office) apps are currently using an even older version of the SDK. Update Jan 4th 2025 – Microsoft 365 (Office), Word, Excel and PowerPoint recent updates take them to v19.7.6 of the SDK and screen capture is now blocked in these apps as well. Microsoft Teams is currently on 19.7.5 and so not supporting screen capture block, but suspect this will soon change – use the “monitor” report in the previous paragraph to see what individual devices are running.
To reverse this, should you require screenshots and screen recording but also require App Protection Policies, you can configure an app configuration policy setting of “com.microsoft.intune.mam.screencapturecontrol = Disabled”. This setting will allow screen capture for your iOS devices overriding the sharing settings discussed above. Note this is an App Configuration Policy (not the App Protection Policy discussed in the rest of this blog post) and it is added on the Settings page, and not via the Settings Catalog page (where there is nothing to add). It also needs to be assigned to “Managed Apps” and probably to “All Apps” in the policy Basics page:
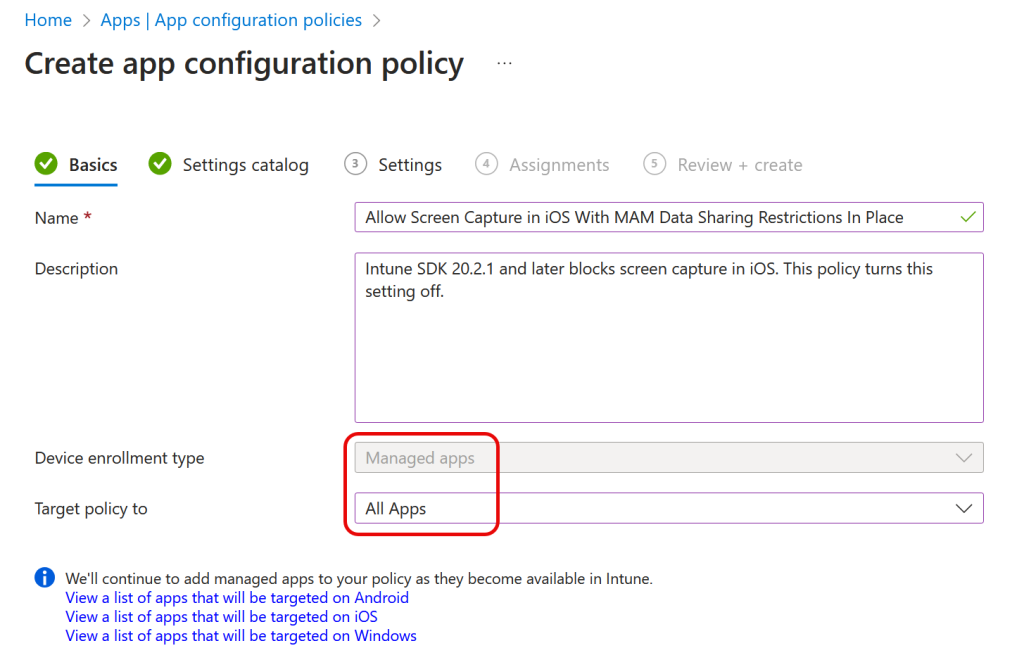
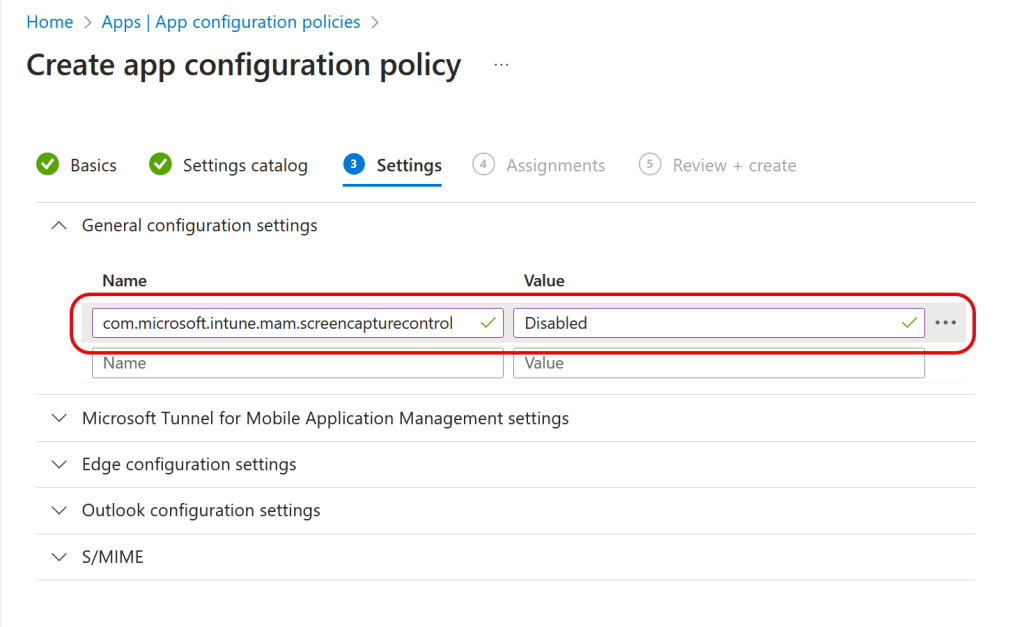
If you turn on this setting then it will take effect on your phones once the configuration policy downloads to the device and you restart the app, which could take 24 hours though I saw it working after leaving the device overnight.
This functionality has been available for App Protection Policies for Android devices for some considerable time. This is only new for iOS devices.
April 2025 Changes To Intune
From Intune version 2504 and onwards (see your Intune tenant settings for the version you have) then the App Protection Policy settings will gain three new settings:
- Genmoji
- Writing Tools
- Screen Capture
Its the last of these that is of interest to this article, and you will see that Screen Capture has been added to the App Protection Policy (APP). The default value for each of the above will be “block” if the “Send Org Data to other apps” is anything other than “All apps”.
If you have created an App Configuration Policy as described above to turn screen capture back on, then this will keep it turned on. That is the App Configuration Policy (ACP) will override the new settings in the APP.
We recommend that if this applies to you (ACP turns on screen capture and the new Intune settings block it again) then you set the APP to “Allow” for screen capture, and once the settings have had time to sync to the devices, to delete the ACP.
Independent of the screen capture changes, also consider what you want to do with Writing Tools and Genmoji and allow them if you want to.
These changes are all described in Message Center post MC1025202
Photo by Pixabay: https://www.pexels.com/photo/access-antique-bolt-close-277574/

Leave a Reply