When you configure a Multi-Tenant Organization in the Microsoft 365 Admin Center a number of changes occur across a number of services. These allow for features like member or guest sync, cross-tenant people search and different behaviours for joining meetings (treating people in other tenants as internal for meeting join).
You can put all these features together by hand, but the M365 Admin Center wizard will also do it for you. The admin center wizard is documented elsewhere, so this just looks at what gets changed.
Cross-Tenant Sync
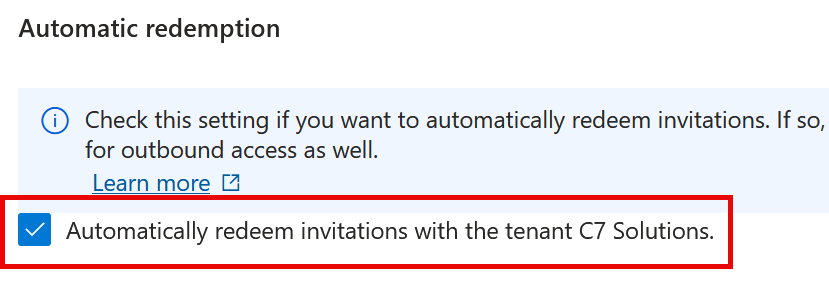
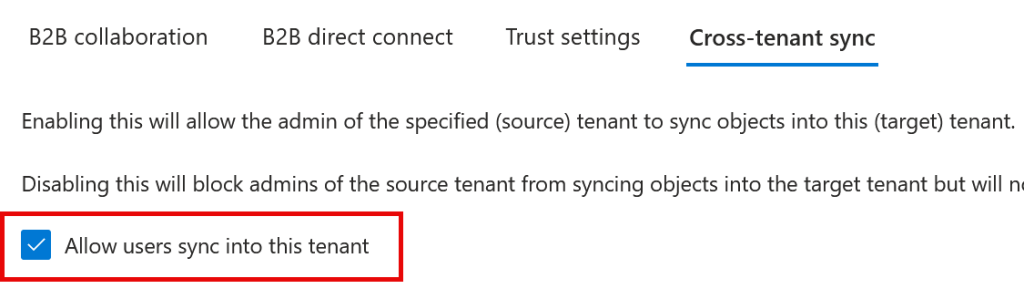
Setting up a Multi-Tenant Organization (MTO) will enable user sync between all the tenants in the MTO. This requires the permission to allow other tenants to sync into your tenant and to remove the consent prompt at the first cross-tenant login. You will find these settings in the Entra ID Portal > External Identities > Cross-Tenant Access Settings, and in the row for each external tenant in the MTO you will find under Inbound both the Trust Settings > Automatically redeem invitations with company name. And under Cross-Tenant Sync > Allow user sync into this tenant.
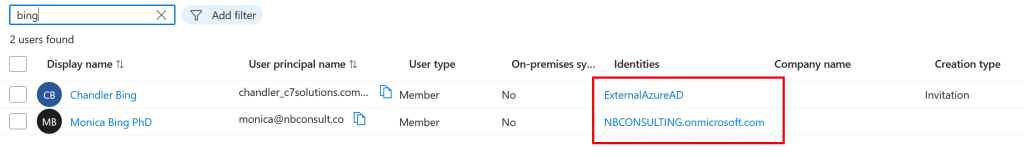
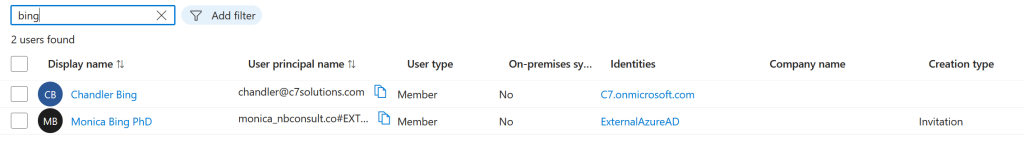
In each tenant there will be synced the users from all the other tenants. In the above two pictures we have user Chandler created in the lower tenant, and synced to the upper tenant and the reverse for the user Monica.
People Search
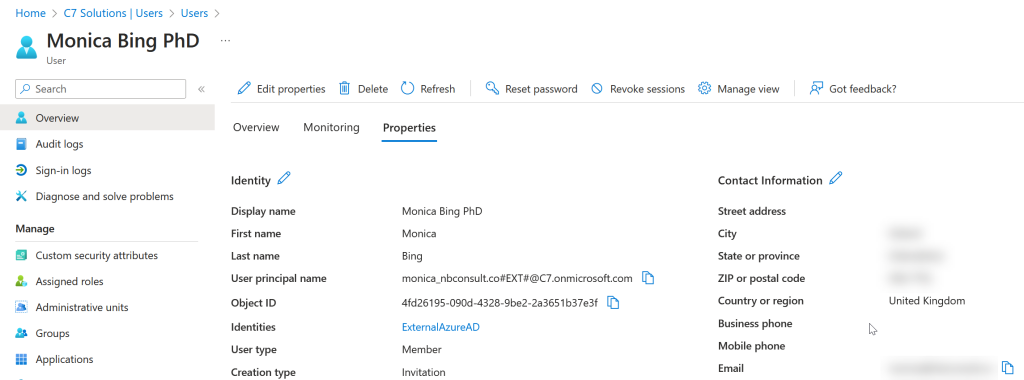
Once the users are synced across you are able to search for them in applications like Teams, SharePoint and Exchange Online. Its not immediate, but they should turn up within a few days and Microsoft says to wait 7 days before raising a support request! Of course, the user needs to be synced for them to appear, so you need to ensure that new users are added to the sync scope in their home tenant.
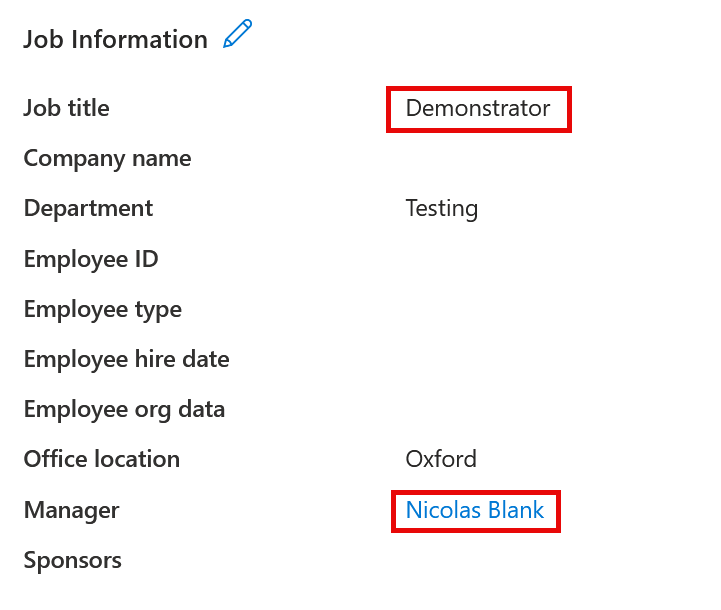
People Search will show features such as display name, names, job title, and manager. The manager user needs to be synced for this to work but if it is, then the organization chart will be correctly populated in People Search. Though you can set a user to have a user in another tenant as your manager, after sync completes this will break as the user object in both tenants is known by a different ObjectID in each tenant. You can set a manager/direct report manually in all tenants. Also manager and direct report being in the same tenant and both in scope of sync will sync, but if manager and direct report are in separate tenants this will not sync (UnableToResolveReferenceAttributeValue is the error). Note that if the manager is different in different tenants this will keep resetting itself every 20 minutes to try and correct it as well.
Calendar
Calendar sync is a feature of Exchange Online that has existed for years. Multi-Tenant Organizations allows you to turn this on between your tenants with one click (per tenant). It is not enabled by default, and it will only work where mailboxes are located in a single place, i.e. Exchange Online and not some in Exchange Server and the rest in Exchange Online.
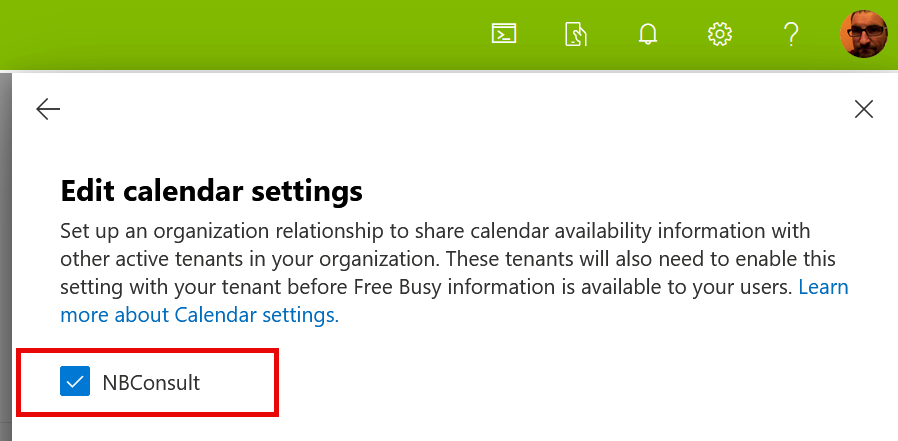
This setting under MTO is located in Manage Settings > Edit calendar settings. It can also be found in Exchange Online Admin Center > Organization > Sharing. Setting up the organization relationship under MTO when it already exists in Exchange Online will fail the config under MTO. So if it is already in place under Exchange Online, MTO will show an unticked box, though it is in place and working.
Calendar sharing is one way – you need to configure it on both sides separately.
External In Outlook
This is a more recent setting to MTO. This was not visible in the summer of 2025 (I think), but I first saw it in December 2025.
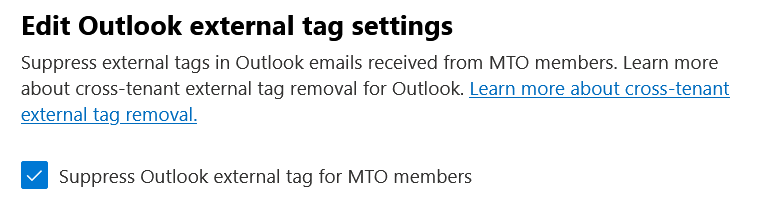
This allows you to set members of the MTO group to not appear as “External” in Outlook – all the members of the multitenant organization are seen as internal from the viewpoint of Exchange Online/Outlook Web Access (OWA) and the Outlook client. Note this has no impact on manually added banners or subject changes to add the word or words to the effect of “…external email…” and only controls the External icon in Outlook on each message.
This controls the IsInternal property of the RemoteDomain setting (PowerShell) from Exchange Online. You can see this with the PowerShell command:
Get-RemoteDomain *MTO* | DomainName, IsInternal
This does not change the AllowedOOFType property, so these domains still get your external Out of Office message! This will also only add the default domain to the Remote Domain list and not all of the domains in the tenant, so if you have an MTO with Zava, and they set their default domain to the tenant domain of zava.onmicrosoft.com, then this will be the value of the Remote Domain that is created, which means zava.onmicrosoft.com will not get external icons, but zava.com will do. So you might need to create additional Remote Domains to complete this configuation.
MFA and Device Trust
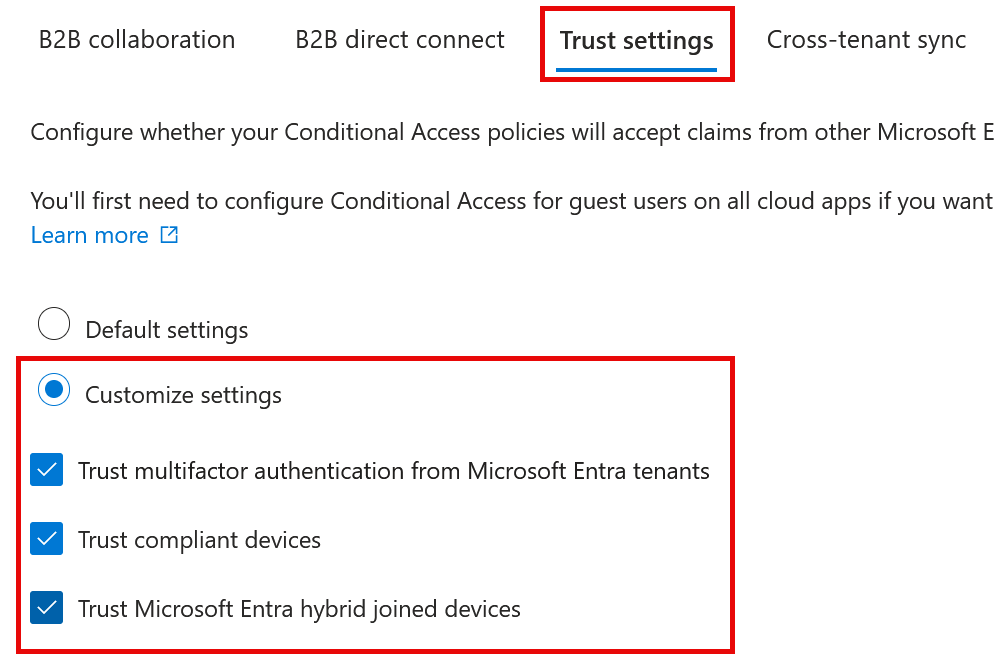
MTO will not set up a trust for multi-factor authentication or devices, but now that you have Entra ID > External Identities > Cross-Tenant access settings > each tenant > Inbound > Configure > Trust Settings (or just configure the default) and then turn on each of the following as you require (and repeat in the other tenants):
- Trust multifactor authentication from Microsoft Entra tenants
- Trust compliant devices
- Trust Microsoft Entra hybrid joined devices
Labels
You can have a label under each user in each tenant (in Teams only at the time of writing) that shows either nothing (so not “External” which it will show by default) or a label per tenant (for example if you have a tenant per country, you could label each tenant “UK”, “NL” etc. Or you could have a single label per synced user. This can only be set by the MTO owner tenant, and only after some time (its not available immediately as I write this).
Sharing
Users from each tenant are synced as members when setting up MTO in the M365 Admin Center. You can change this via the Cross-Tenant Sync settings in the Entra ID portal (so users are guests in other tenants) but if users are members in other tenant they will have a more seamless collaboration experience. This includes access to files using “people in your organization” sharable links. You should consider using sensitivity labels if you need to limit who can access a file with a “people in your organization” link.)
Sharing settings can be adjusted individually per site in the SharePoint Online admin center, or globally in a number of places, but as we are in SharePoint Online Admin Center its under Policies > Sharing.
Sensitivity Labels, as with sharing policies, are not changed by MTO and so you adjust these via the Compliance Admin Center.
Meetings
You can join meetings in Teams as a synced member or a synced guest. If you are a guest user then the Guest Access policies apply (https://admin.teams.microsoft.com/company-wide-settings/guest-configuration), but if you are a member account then the standard policies (Global by default) will apply. If you want different policies to apply to synced users, create a dynamic group and then one or more Teams policy that applies to members of that group.
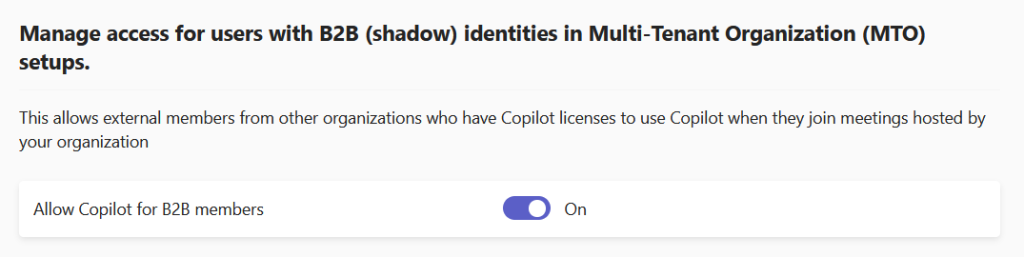
Copilot
Users who have a Copilot licence can use that licence in meetings hosted by the MTO tenant. Usually when in a meeting with an external tenant that they host, you cannot use Copilot. This needs enabling in the host tenants Teams Admin Center > Users > B2B Member Access, (or with the new centralised Settings page via Settings & Policies > Global > External Collaboration > B2B Member Access).
Chat
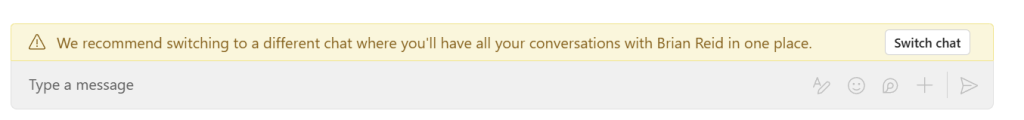
When an existing user is invited as a guest to your tenant, they are made in the directory as an External Guest. You can chat with the external guest user or with the external user account in the home tenant. This means two separate chats to manage.
Once you sync the user, and change the UserType to Member (this is not the default configuration of a cross-tenant sync, but is the default for a MTO created cross-tenant sync) then the desktop and mobile Teams clients will block access to any existing chat to the guest user and instead suggest that you “switch chat” to the external user so that you have an maintain one chat going forward. The Teams web client does not do this, so you can maintain two chats if using the web client!

Leave a Reply