The instructions from Microsoft at https://docs.microsoft.com/en-us/azure/active-directory/device-management-hybrid-azuread-joined-devices-setup are missing some of the steps on setting up hybrid device join to Azure AD. This is a complete list of steps when Pass-Thru auth with SSO is enabled on the domain.
- Enable SSO – this is covered elsewhere. You can also do hybrid device join on a federated domain, though this is not covered here.
- On your AADConnect server ensure that the MSOnline PowerShell add in is installed – this is the AdministrationConfig-3.msi executable that is needed to run cmdlets like Get-MSOLUser. Is only supported by the MSOnline PowerShell module version 1.1.166.0. To download this module, use this link
- Open an administrative PowerShell
-
cd 'C:\Program Files\Microsoft Azure Active Directory Connect\AdPrep'
-
Import-Module .\AdSyncPrep.psm1
- This will enable the AD module and import some scripts for device writeback and device registration. We are looking at device registration here
-
$aadAdminCred = Get-Credential
#Enter a global admin credential
-
Initialize-ADSyncDomainJoinedComputerSync –AdConnectorAccount [connector account name] -AzureADCredentials $aadAdminCred
#[connector account name] is the name of your domain (domain.local for example) as shown in the AADConnect Synchronization Service Manager –
- You should see the message “Initializing your Active Directory forest to sync Windows 10 domain joined computers to Azure AD.” followed by “Configuration Complete”. Errors about Azure Registration mean you are running the wrong version of the Azure AD PowerShell cmdlets
- The required settings in AD (for one forest) are now done. If you have multiple forests, return to the above referenced document and run the script to register the Devices Registration Configuration node to AD
- If you have conditional access available (have at least one Azure AD Premium licence assigned to your admin account) then you can add Trusted Sites to Azure AD to control where MFA prompts for device join will happen outside of. Add each office public NATed IP address with /32 (or whatever is needed at the end) into Azure Active Directory (under portal.azure.com) > Conditional Access > Named Locations > New Location
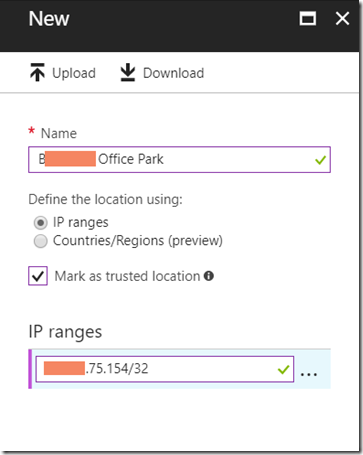
- Add the same IPs to the “Configure MFA trusted IPs” link on the same page that you see the IP’s listed above
- Your list of devices under Azure Active Directory should now increase as users reboot Windows 10 1703 machines and later. See the above document about the GPO setting needed to role this out to older versions of Windows (Workplace Join settings)
Leave a Reply