This article is the sixth in a series of posts looking at Microsoft’s new Rights Management product set. In the previous post we looked at turning on the feature in Office 365 and in a later post we will see how to integrate this into your on-premises servers. In this post we will look at how to add templates to Microsoft Rights Management so that you can protect content with options other than the two default templates of “Company – Confidential” and “Company – Confidential View Only”. In this series of articles we will look at the following:
- What is Rights Management
- Turning on Azure Active Directory Rights Management
- Managing Azure Active Directory Rights Management
- Enabling and Configuring AADRM in Exchange Online
- Enabling Microsoft Rights Management in SharePoint Online
- Creating Microsoft Rights Management Templates and Policies (this article)
- Configuring Exchange On-Premises to Use AADRM (the RMS Connector)
- Configuring Exchange On-Premises to Use AADRM
- Configuring SharePoint On-Premises to Use AADRM
- Using Microsoft Rights Management from Microsoft Office
- Using Microsoft Rights Management to protect anything/everything else
The items above will get lit up as the articles are released – so check back or leave a comment to the first post in the series and I will let you know when new content is added.
One of the most requested features of Microsoft Right Management (that which used to be called Azure RMS) is custom templates. Custom templates let you define the protection policies you would like to roll out within your organization. Whether your organization is using Azure RMS in as part of your on premises deployment (via the RMS connector) or as part of Office 365, you can now do this via the Azure Management Portal.
First thing though is you (currently) need an Azure subscription. To get an Azure subscription you need a credit card, even though you are doing something in Azure that is not charged for. If all you do in Azure is what is in this blog then the card will never be charged – but as you can do so much you will probably not do just what is here in the blog. Note though that if you are doing this for lab and testing purposes, you will still need a credit card, but you cannot use the same card for more than one subscription. This is awkward, as it means each client I set this up for needs to provision their own lab tenant for me and then grant me permissions. A free Azure showing just the free features and no credit card requirement would be very useful. So to create your Microsoft Rights Management custom templates login to Azure at https://manage.windowsazure.com and sign up if necessary. Make sure you login with the same Office 365 global administrator account that you used when you where enabling RMS in Office 365.
- Do not sign in with your Microsoft ID (ex Live ID), always sign in here with your Organizational ID.
- Scroll down the left of the management screen and click Active Directory.
- To use Microsoft Rights Management you must have synced your on-premises Active Directory to Azure Active Directory and you can manage AD from here now as another free feature of this subscription you have created.
- Select Rights Management on the main screen:
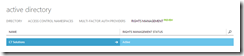
- Click your company name and then in the getting started screen select Manage your rights policy templates. You will see the two default templates of “Company – Confidential” and “Company – Confidential View Only”.
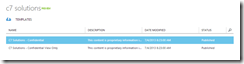
These two templates protect content so that it can only be seen by members of your company (that is, users who’s account is synced to your Azure Active Directory tenant from your on-premises Active Directory). The “Company – Confidential” is editable by anyone in the company but cannot be opened if you are outside the company. The “Company – Confidential View Only” template is used to protect content that you want people in your company to view, but not edit. Again this is not viewable for users who do not have a login at your company. With the custom templates that you can now add you can designate different groups of users that will have access to documents protected with these templates, and you can define an access level or a list of rights for each of these groups. You can also control for how long content protected with these templates will be accessible, and you can define whether you want to require users to be online to access the content (thus, getting maximum control over their ability to access the document in case your policies change over time and ensuring all accesses to the documents get logged) or you want to allow them to cache document licenses so they get the ability to access the content from disconnected locations for up to a defined period of time.
To begin the process click Add on the bottom of the management web page and fill in the details required:
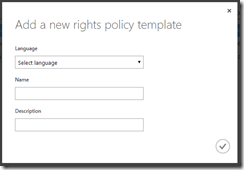
Though you can have any name and description, the recommendation is to have a short enough list that your users can scan easily and that contains the company name and a brief outline of the rights granted. The following might be good example names:
- Contoso – Board Level Confidential (Grants access to company board level staff only)
- Contoso – All Full Time Employees Only (Visible to all Full Time Employees only)
- Contoso – Legal Time Sensitive View Only (Grants the legal team online access to document for 7 days)
The name of the template appears in the yellow banner at the top of the application, so should clearly identify who can view and what they can do with the document. You can also set different languages. Applications will pick the most suitable language version, with US English being the top of the list as downloaded from Microsoft and so the version that appears if your specific language does not appear. Tick the circle and the template is added. The management console returns with “Successfully added the template. Clients won’t see the changes until they refresh their templates”. Note though that templates start their life as “archived” templates that cannot be used, but this is fine, as we have not finished configuring the template anyway. Click on the name of the template to get to the properties pages for the template. You will be presented with the “Quick Start” page: 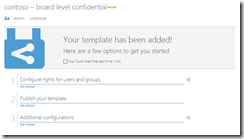
Click “Get started” under “Configure rights for users and groups” to say which groups or users from your Active Directory can access the content protected with this template. This info is synced from your AD every three hours – so any new users or groups will appear in a short while: 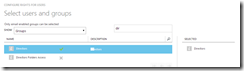
Keep in mind that your groups must have an email address for you to be able to use them in a custom template. If the group cannot be selected that will be the reason, but also remember the previous comment about a three hour sync from AD.
So if you do mail enable a group on-premises, it will be a good idea to continue creating this template now and then returning in a number of hours and adding the additional groups and rights. Select the rights you wish to apply to content protected with this template: 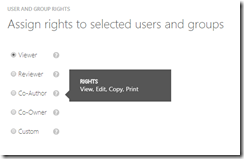
Once the rights are added for the groups/users selected you can add additional groups and users with different rights. To add additional names and descriptions (in different languages) click Configure on the top menu bar:
![]()
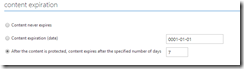
And if your template has content expiration settings, these too can be set under Configure:
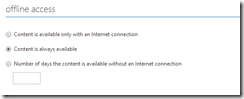
And finally, before you publish your template, you need to decide if you content can only be viewed online (that is with a connection to Microsoft RMS) or if you are allowed to cache the rights to open the content and if so, how long you can cache those rights for:
At the top of the Configure screen select Publish to make a template accessible to users (or Archive to restrict access to it again, and of course all the content protected by the template). Save the template. Clients will be able to use the template to protect their content once they have updated their templates.
For example Exchange Server will refresh its templates every 30 minutes from the RMS Connector and OWA will show them at next login, but if you are running Exchange Online you need to refresh the templates manually. See http://technet.microsoft.com/library/dn642472.aspx#BKMK_RefreshingTemplates for the steps to refresh different clients and servers.
Leave a Reply