Entra Password Protection service is a component of Entra Plan 1, and allows you to have a custom password block list in Entra and have that list and Microsoft’s “secret” list downloaded to your domain controllers and influence your on-premises password changes.
It works by installing an agent on each domain controller and one (or more) proxy servers for each Active Directory forest. Microsoft has all the documentation to install and configre the proxy and DC agents, but does not cover what to do when you need to decommission the proxy server and move the Entra Password Protection Proxy service to a new machine. It turns out the steps are easy.
First, download and install the Password Protection proxy service from Microsoft’s web site. When you installed it on a first server, the installation steps included registering the proxy so it could communicate with Entra ID (previously known as Azure AD). This registration process generated a certificate so the proxy could communicate securely with Entra and registered the proxy in Active Directory.
Installing additional proxy servers in the same forest just pick up this configuration – so as long as your current password protection proxy server is still running and is maintaining the forest certificate(s), installing a new server will use the current certificate and continue as if nothing has changed. It will register itself with Active Directory (as a child object under the server object in the directory, you can view this with ADSIEdit.msc if you wish) and existing DC Agents will start to use this proxy as well as the previous one.
Version number mismatch across proxies and DC Agents is allowed – any version of the proxy and any version of the DC Agent can talk to each other. The proxy self-updates so should always be on the latest version, but the DC Agent does not. Therefore, before testing your new proxy it is probably worth the few seconds it will take to generate a list of all the proxies and agents, as well as their versions, in the forest. An agent should be on each domain controller and no domain controller should be missing the agent. Ensure that you are running version 1.2.172.0 (Feb 2021) or later as these come with the below PowerShell test and reporting cmdlets:
# Get a list of all the Entra Password Proxies in the forest along with their version:
Get-AzureADPasswordProtectionProxy
# Get a list of all the Entra Password DC Agents installed:
Get-AzureADPasswordProtectionDCAgent
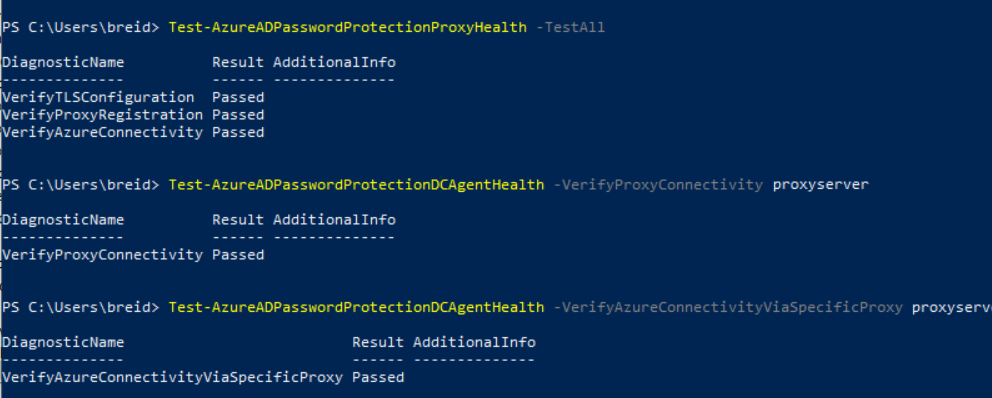
You can validate that the new installation is working with a few administrative PowerShell cmdlets. These are as follows, with a description next to each line on what they do – all these should return “Passed”:
# Test the Entra Password Proxy Health - all tests run, should return three "Passed" entries (run on the proxy server):
Test-AzureADPasswordProtectionProxyHealth -TestAll
# Test an already installed DC Agent connecting to your newly installed proxy server:
Test-AzureADPasswordProtectionDCAgentHealth -VerifyProxyConnectivity newproxy.domain.com
#Then testing from the same DC Agent to the new proxy and onward to Azure for complete connectivity
Test-AzureADPasswordProtectionDCAgentHealth -VerifyAzureConnectivityViaSpecificProxy newproxy.domain.com
If this is not working, then perform the proxy registration steps to configure the service as if it is the first time you are installing the service as found on the Microsoft documentation for the product.
Once your proxy is working, you can now uninstall the previous proxy server and remove its entry from the domain. If you are removing the server from the domain and deleting its entry in Active Directory you do not need to do the following, but if you are leaving the server in place and just uninstalling the software, then you should tidy up the configuration in Active Directory.
$scp = "serviceConnectionPoint"
$keywords = "{ebefb703-6113-413d-9167-9f8dd4d24468}*"
Get-ADObject -SearchScope Subtree -Filter { objectClass -eq $scp -and keywords -like $keywords }
Don’t miss the * at the end of line 2 above. This returns all the proxy servers in each domain, repeat for different domains if you have them. It will show the path in the directory for each installed proxy server.
Remove unneeded proxy servers by uninstalling the service and then cleaning up Active Directory by removing that object using ADSIEdit or Remove-ADObject PowerShell cmdlet. It is important to uninstall the proxy server first, as running proxy servers recreate the Active Directory configuration periodically.
Photo by Pixabay: https://www.pexels.com/photo/umbrella-lot-268941/

Leave a Reply