This is a simple blog post to outline how to turn on Windows LAPS via Intune to ensure that all your managed devices have a local admin account that has a unique password per device. A unique, and frequently changed, local admin password stops lateral movement by malicious actors from a compromised machine across some or all the machines on your network.
Windows LAPS is built into Windows 10 and 11 running the March 2023 security update and later and is turned on with two Intune (or Group Policy / registry key) settings.
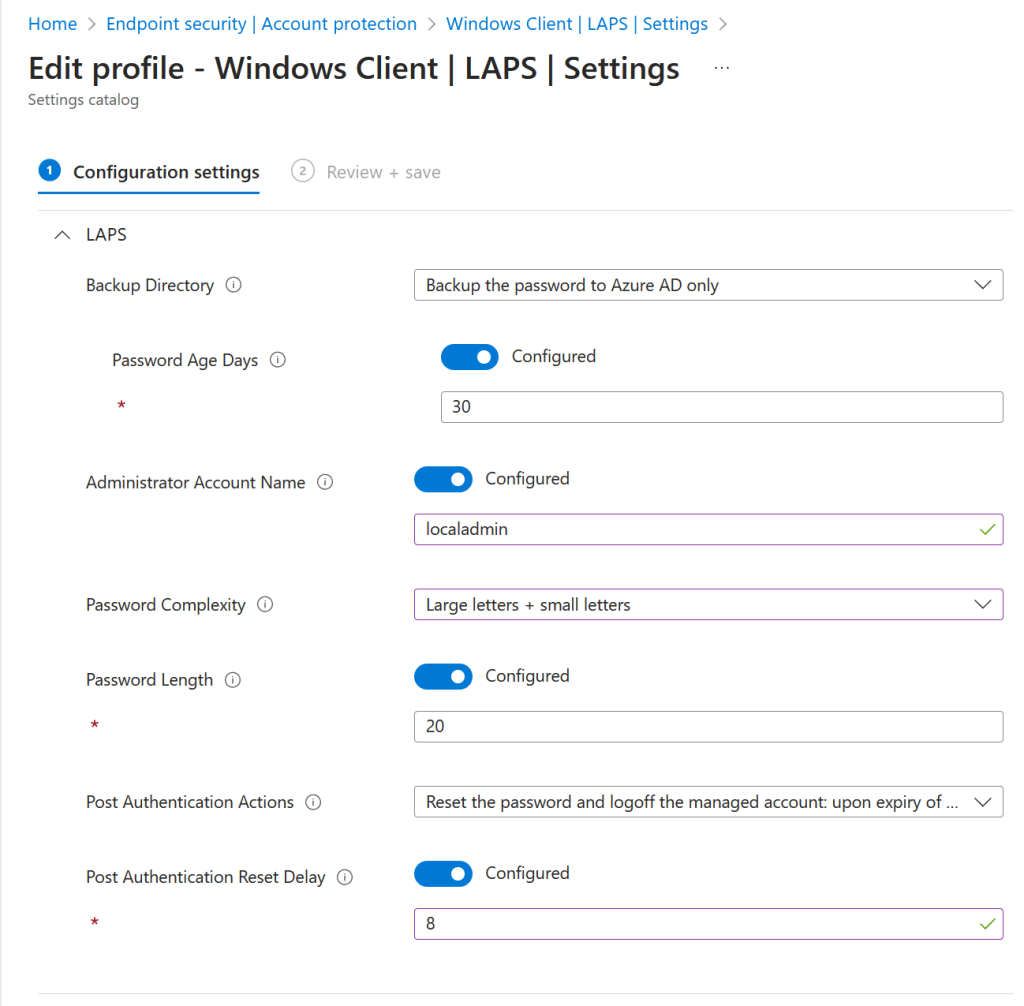
There are six settings that can be enabled, but only one is required. The settings are:
- Backup Directory (required) : Azure Active Directory is the best option as we are using Intune to push these settings, therefore we know AAD exists. Select Active Directory for a non-cloud organization.
- Password Age Days (optional): How often LAPS will automatically change the password of the managed account. Defaults to 30 days if not set.
- Administrator Account Name (optional): The administrator account to use. LAPS does not create this account and we will make it later on in this blog post. If this value is not set then LAPS will use the default administrator account on the machine, which is the first account created on the device. If you have a Microsoft Teams Rooms under management I recommend not to set LAPS against the default administrator account as this will impact some room systems (i.e. Crestron) rely upon a known account and fixed password for room functionality.
- Password Complexity (optional): The default is “large letters + small letters + numbers + special characters” (i.e. the most complex) but this means that once the device administrator has retrieved the password for the device they need to type that in. As the password is encrypted in the directory and rotates often an easier to type password might be more functional and as secure. The set password though needs to meet your password length and complexity policy.
- Password Length (optional): Defaults to 14 characters if not configured
- Post Authentication Actions (optional): This will reset the password of the LAPS managed admin account and log that account off 24 hours after the account is used unless the next option is also set to change the timer. Other options such as reset password and reboot are also available
- Post Authentication Reset Delay (optional): After how long to reset any used password on the device. Defaults to 24 hours.
So pick the options you want and create a Windows LAPS policy from the Intune portal: https://endpoint.microsoft.com/ > Endpoint Security > Account Protection > New Policy > Windows 10 and later > Local admin password solution (Windows LAPS)
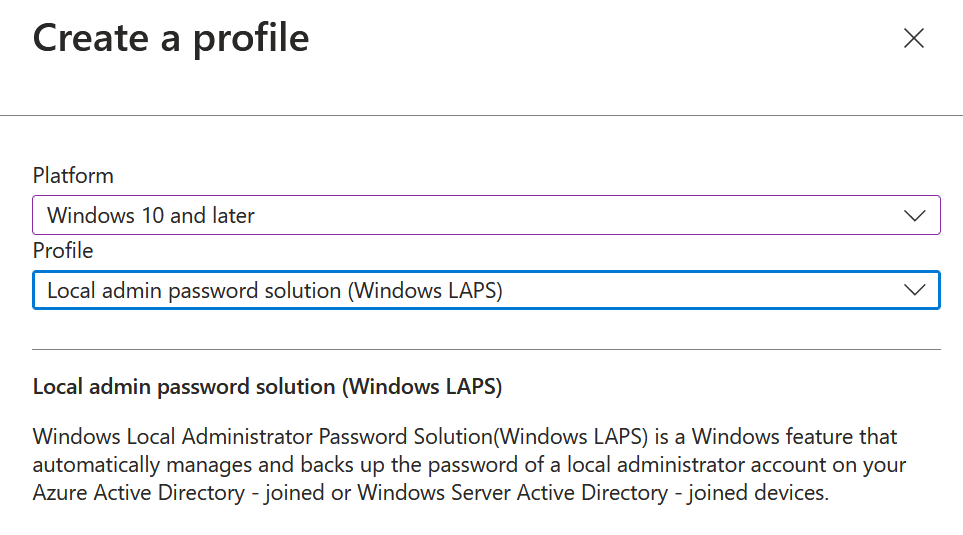
Give the new profile a name and optional description. Choose the Backup Directory option. Configure any other options you want and click Next.
Set Scope Tags is required and then assign the policy to All Devices. You have now set up your Windows LAPS policy.
This will deploy to the targeted Windows devices within 8 hours and then within 30 minutes of that the Windows LAPS agent on Windows (built in, no software needed to be installed, its part of the March 2023 and later monthly updates) will reset the account password that it is managing.
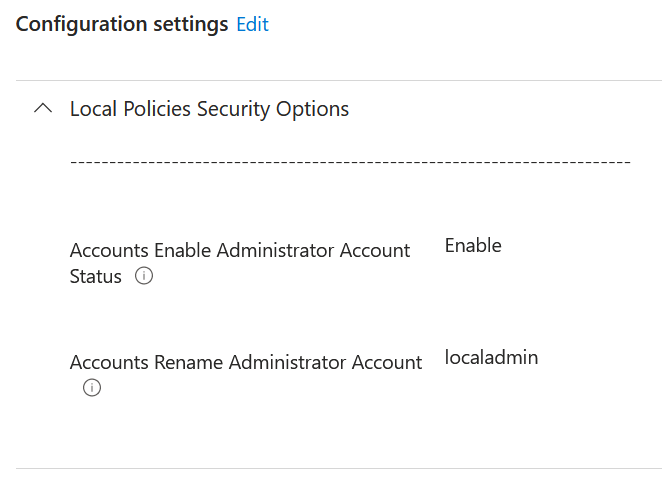
If you use LAPS to configure the default local “Administrator” account (well, the account with with well known identifier ending in -500) you need to ensure that the account is enabled and preferable renamed. This can be configured with the Intune setting catalog setting called “Local Policies Security Options/Accounts Enable Administrator Account Status”. Another policy in this same category (Accounts Rename Administrator Account”) can be used to rename the built-in Administrator account. See the note earlier about Microsoft Teams Room systems and needing the admin account to work.
If the admin account you pick does not exist LAPS will not create it, and for that you need an additional Intune configuration. For this there are two options. The first is a fixed password that Windows LAPS will rotate within 30 minutes or a script to create a local admin account with a random password (recommended).
The fixed account password uses OMA-URI settings in Intune and writes the settings to the local device. But it cannot then read the settings back again (as the setting is the admin password and that is not retrievable from Windows), so though this option works it does always show an error for all devices in Intune – as shown below:
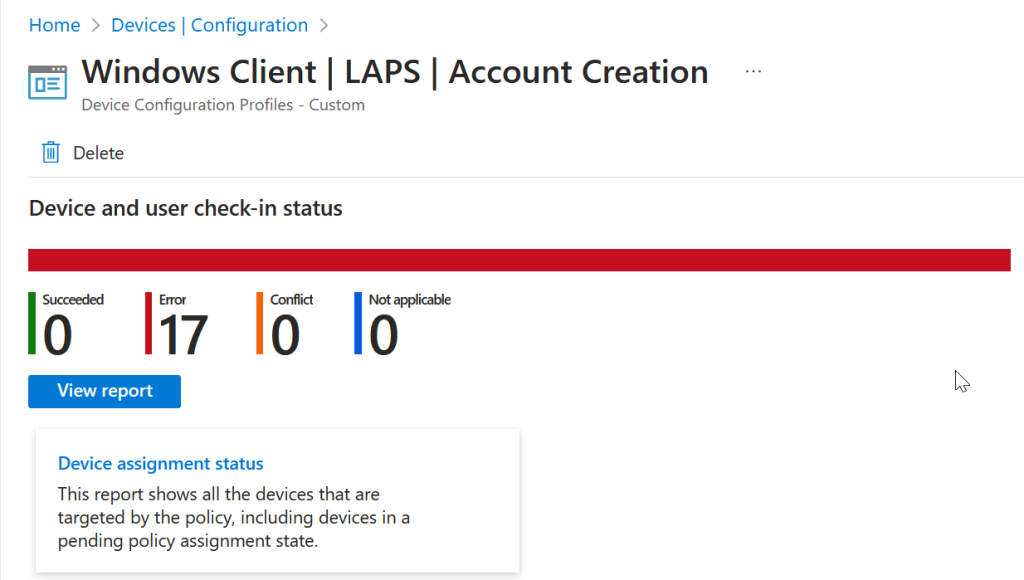
The error code for the above is -2016281112 for your reference. To create this Configuration Profile create a Custom Configuration Profile and add these two OMA-URI settings:
- ./Device/Vendor/MSFT/Accounts/Users/localadmin/Password
- ./Device/Vendor/MSFT/Accounts/Users/localadmin/LocalUserGroup
The first of these is a String value, and the value is the initial password you want for the LAPS admin account – so set a very long random string – you will never use it as LAPS agent will reset it shortly per device. The second is an Integer and needs to be set to 2, which means add the account to the Administrators group.
In both of the OMA-URI above, the “localadmin” is the name of the account you are creating and so needs to match the name of the account LAPS is managing in its settings.
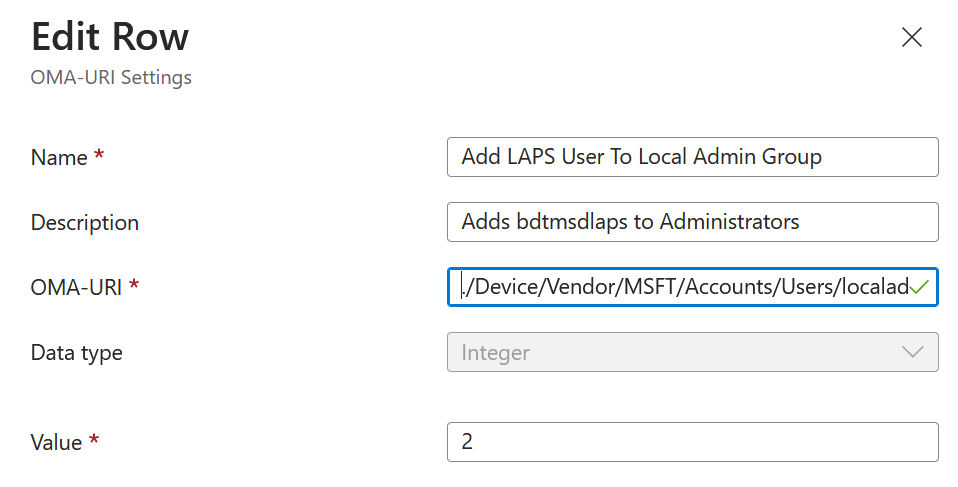
Deploy this custom Configuration Profile to the same group of devices as the LAPS policy (i.e. above we used All Devices).
An alternative to creating a initially fixed local account is to use a script. This is based on New-LAPSAdmin.ps1 by Nathan McNulty and is available at his GitHub.
$lapsAdmin = "localadmin"
if (!(Get-LocalUser -Name $lapsAdmin -ErrorAction SilentlyContinue)) {
[securestring]$password = ConvertTo-SecureString -String (New-Guid) -AsPlainText -Force
New-LocalUser $lapsAdmin -Password $password -Description "LAPS managed account"
Add-LocalGroupMember -Group "Administrators" -Member $lapsAdmin
}
The above script will check if the user “localadmin” exists and if not will create it with a random password (using New-GUID to be the source of this password, for example running this on my machine resulted in 3051de52-6ef0-4e10-8cf3-ad1792182102, which would pass most password length and complexity rules).
As above, this script needs to run checking for the account that LAPS is set up to manage and this value exists as a variable $lapsAdmin at the top of the script. Set this to match the account LAPS is managing.
Send this PowerShell script to the managed devices using Intune, Devices > Windows > PowerShell Scripts and deploy the script to the same group of devices that LAPS is managing as shown:
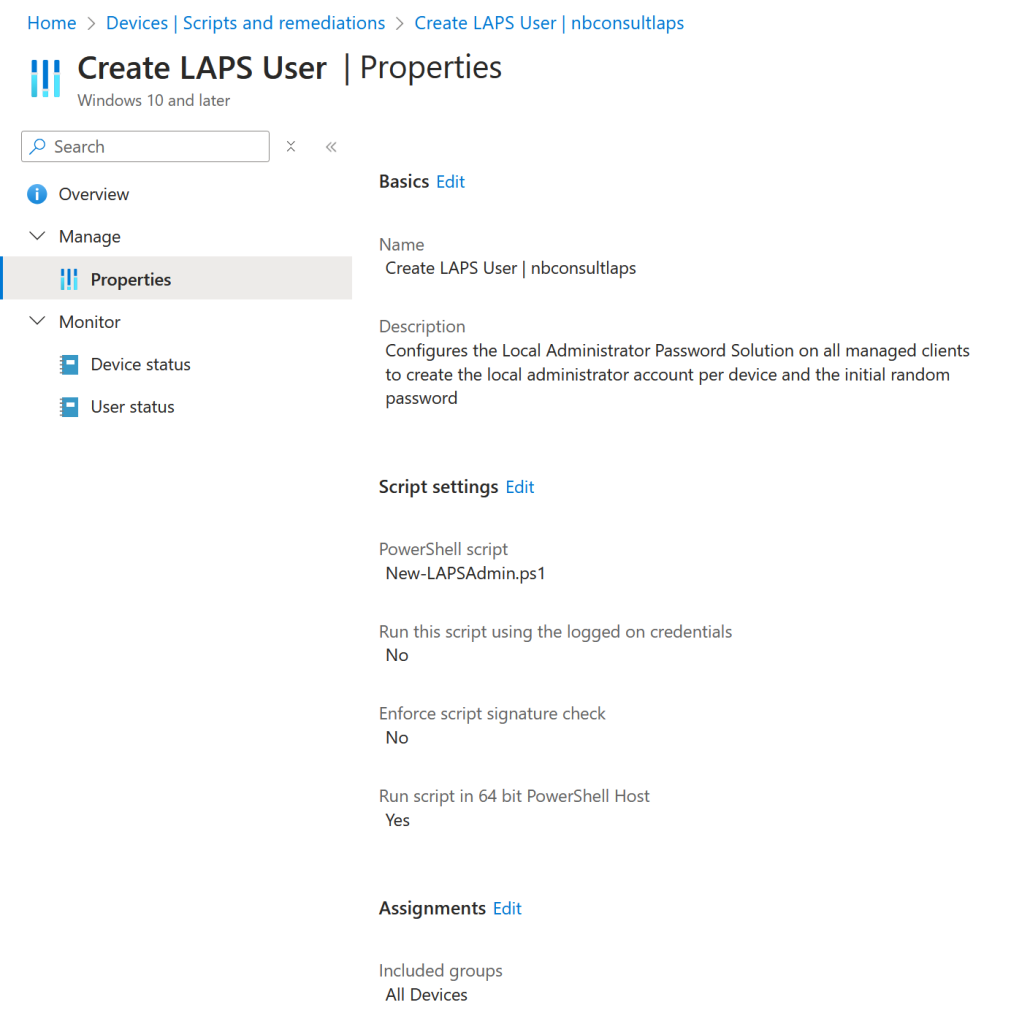
Note that the PowerShell script must run as 64 bit. If you do not set this option the script will run in 32-bit PowerShell on 64-bit platforms. In this scenario the New-LocalUser cmdlet does not exist (as its a 64-bit only cmdlet on these platforms), and so the script will fail to create the user account for LAPS.

Leave a Reply