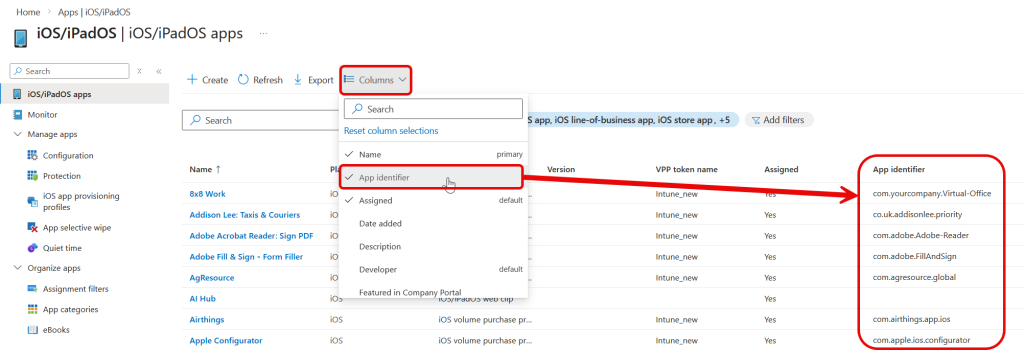
Updated Feb 2026. You can view the bundle ID of any app you push to a phone from Intune. In the list of iOS apps you can add the “App Identifier” column, this shows the bundle ID:
Blog post from 2021 content below.
In Microsoft Intune you can create a secure container where the data in your apps cannot leak outside of. That is, you can restrict copy/paste outside of the supported apps and restrict opening the data in a different app.
But sometimes you need to open the data in a different app and with the Intune Mobile Application Management (MAM) policy (also known as App Protection Policy, APP) in place you are restricted from doing so.
On Android adding the exception for apps is easy – its part of the URL to the app in the Google Play Store. For example to allow data to be sent to Google Maps you would look up the app URL (https://play.google.com/store/apps/details?id=com.google.android.apps.maps&hl=en&gl=us) and exempt the app in Intune MAM policy by using the ID value, so com.google.android.apps.maps in this case.
On iOS this is next to impossible. Microsoft in their article on this subject at iOS/iPadOS app protection policy settings – Microsoft Intune | Microsoft Docs and Data transfer policy exceptions for apps – Microsoft Intune | Microsoft Docs suggest this is done by contacting the app developer. I have had no success doing this, as often the app first line support has no idea what you are asking.
So here is how to get the URL Protocol, or more correctly speaking, the URL Scheme for the app. I think the first battle is in working out the correct terminology!
To get the information you need you have to have access to the ipa file that is the app on the iOS device. I use iMazing for this and my steps here are for the PC, but a Mac version is also available. iMazing is available for purchase on a per device basis but everything I describe here works with the trial/free version of the product.
Once iMazing is installed you need to plug in your iPhone/iPad to your PC. Ensure the apps you need are installed on the device.
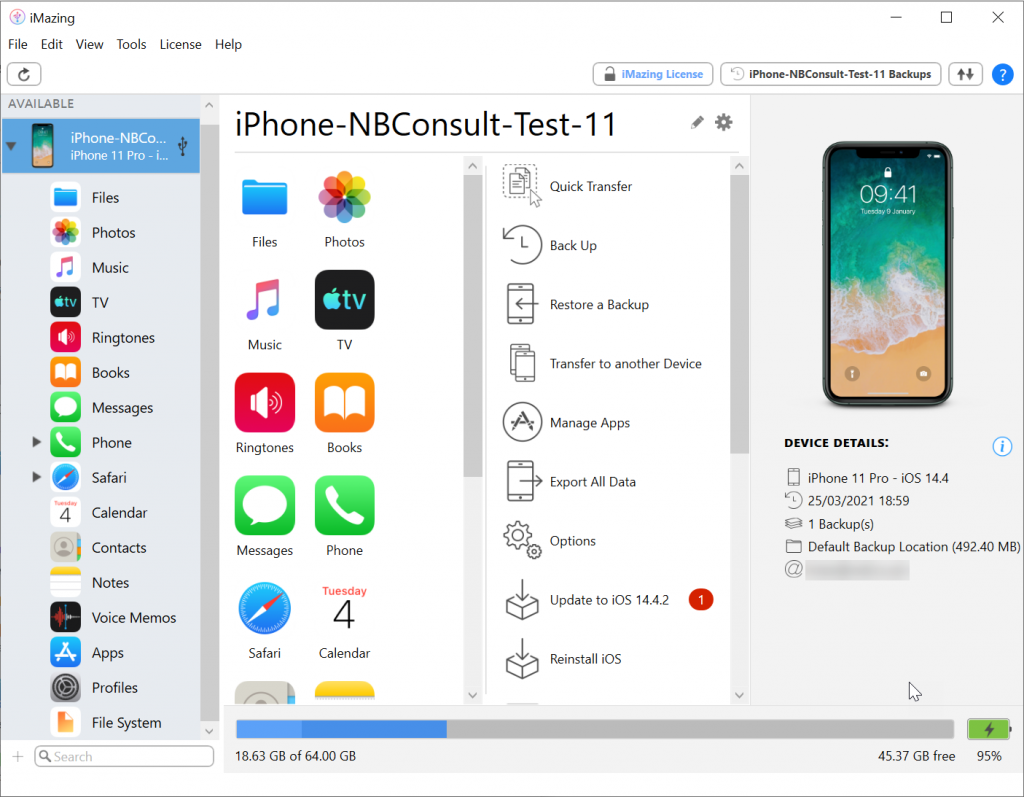
In the middle-right column there is an option called Manage Apps. This lists the library of apps you have on the device and the option to download the app to your PC. I am going to work through the process of getting the URL Scheme for Cisco WebEx Meet, which is the app Microsoft have in their documentation as well, as you can see from my app library below there appears to be two apps called “Webex Meet” – so lets see what is going on.
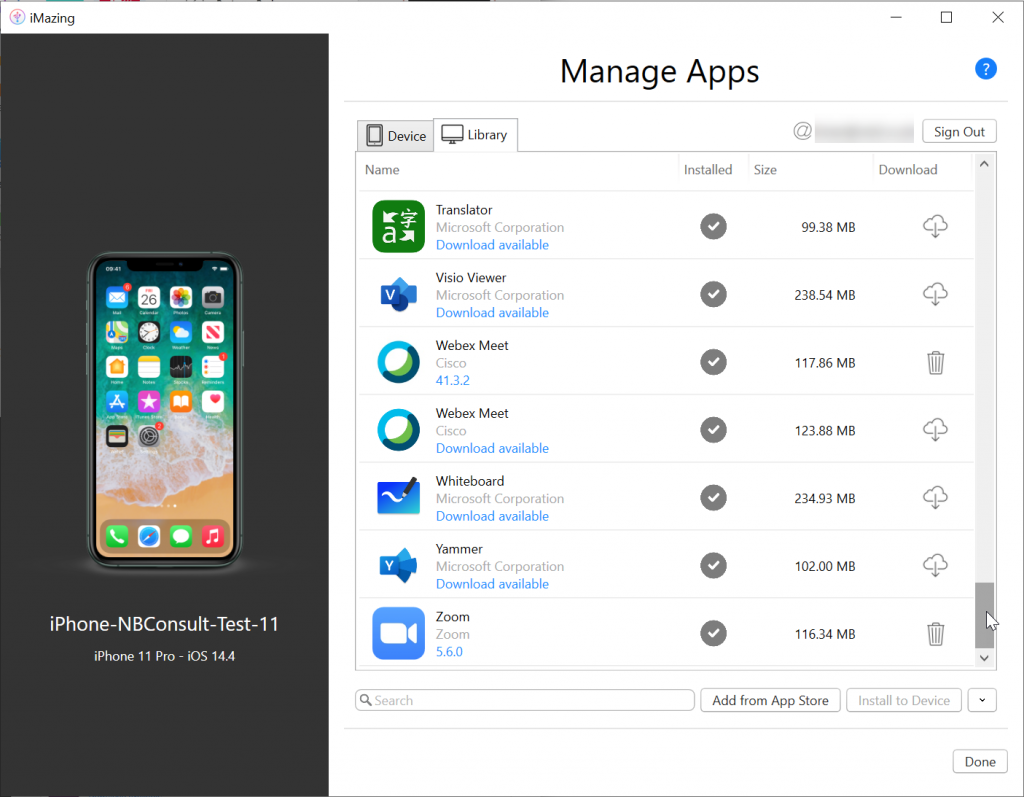
For each app you need to determine the URL Scheme/URL Protocol for, download the app by clicking the “cloud + down arrow” icon to the right of the app.

You will need to login to the Apple account ID used by the iOS device to complete this step.
Once I have downloaded the app the version number is displayed. I had previously downloaded Webex Meet 41.3.2 and the new download is version 41.3.3. So this is why I see multiple versions. The trashcan icon can be used to clean up your download folder. The arrow icon bottom right will give you an option to update all the downloaded apps to their latest version is new versions are available as well.
Once you have downloaded the app you can export the .ipa file for the app. This is done via the same arrow button bottom right. It will export the .ipa file for the selected app to a folder of your choosing.
Choose the folder to export to and then open that folder in Windows Explorer
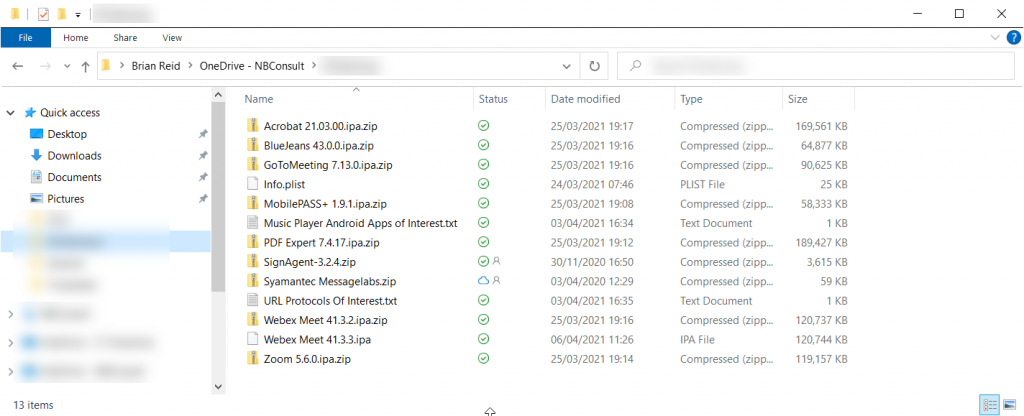
You can see the exported Webex Meet 41.3.3.ipa file in this folder, and the previously downloaded, and renamed, file as well. This rename is the next step. The .ipa file is just a ZIP compressed file, so add .zip to the end of the file name and open the compressed file. Don’t extract the contents of the file, as we are only looking for a single file in all the contents.
If you have downloaded lots of .ipa files then you can rename with in the command prompt in bulk with ren *.ipa *.ipa.zip
Inside the compressed file, navigate into Payload > AppName.app and find info.plist. Copy this file only out of the compressed file.
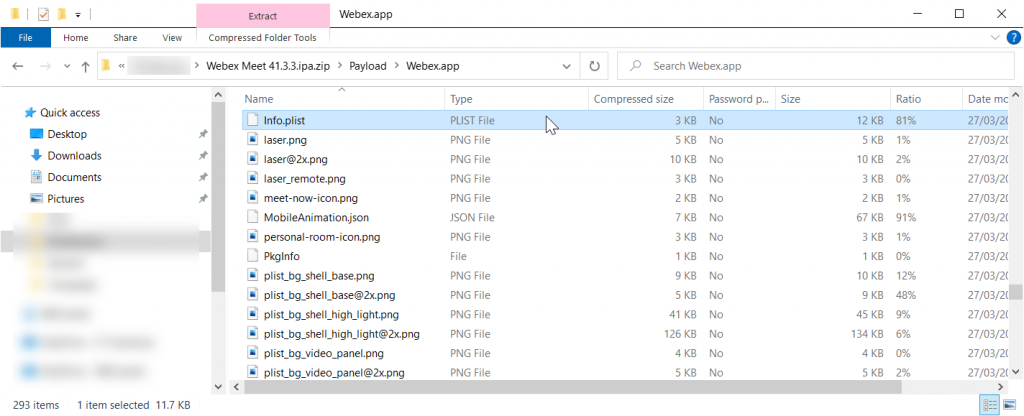
Once you have the info.plist file outside of the compressed folder, open this file in Notepad.
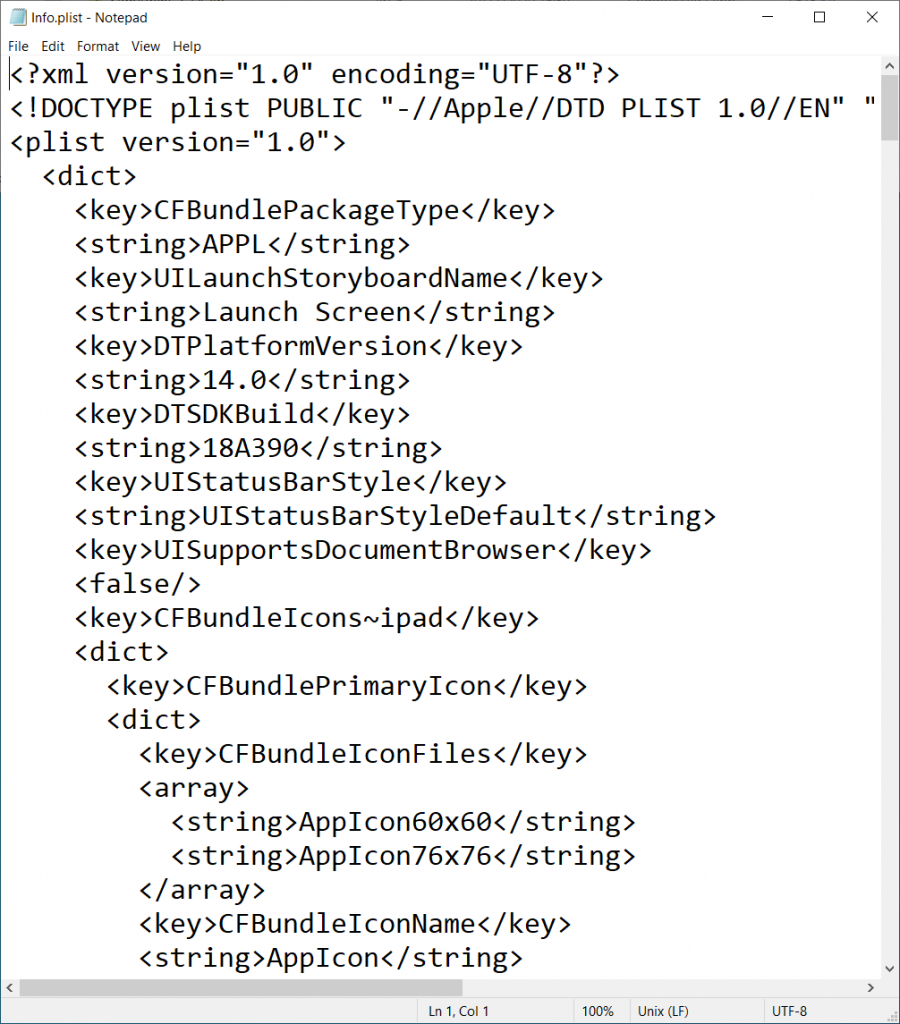
Now to search for the URL Scheme in this file. Search for CFBundleURLSchemes, and unfortunately you may see more than one of these. We know from the Microsoft documentation that they say the URL Protocol for WebEx is wbx and we see this value as a <string> under <array> under <dict> where <key> is CFBundleURLSchemes
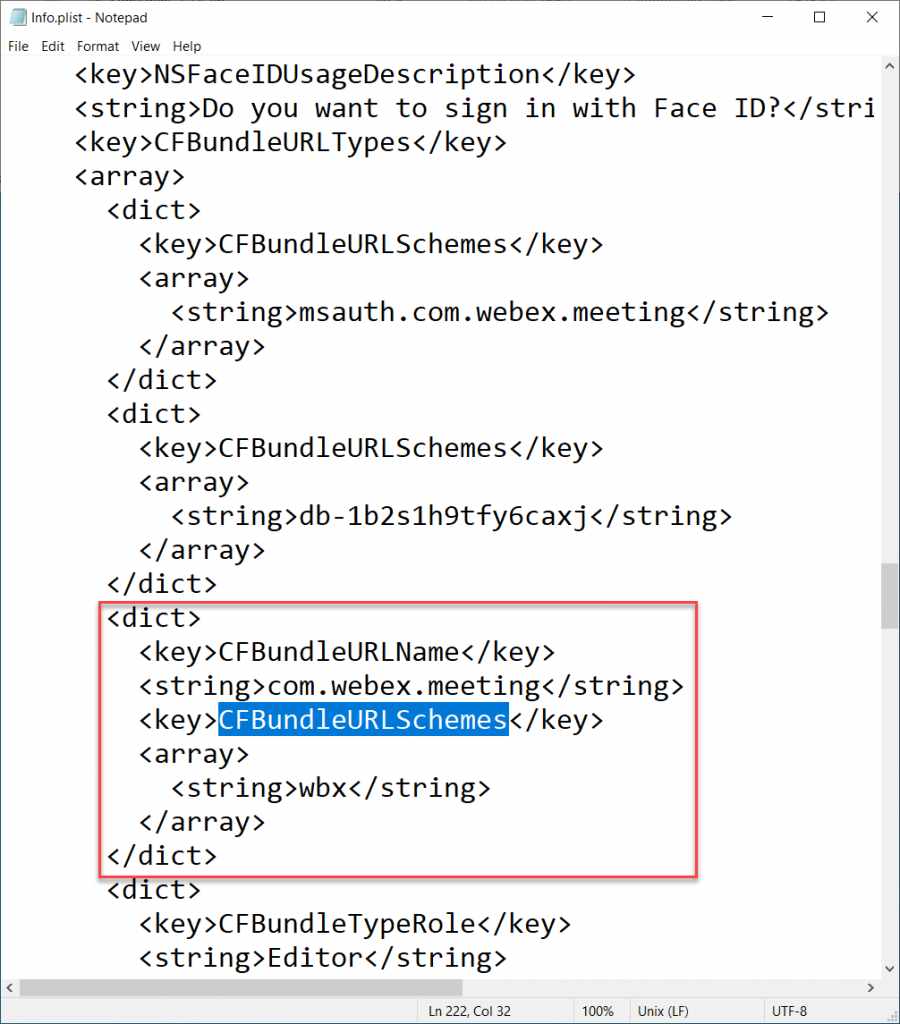
The <string> value is the URL Scheme, and so for WebEx is is wbx. The value is found under Key=CFBundleURLName, Key=CFBundleURLSchemes, String=. At this point it is all down to testing on the device. So add the most likely string to Intune MAM policy exceptions and wait for that to sync to the phone (browse to about:intunehelp in Edge Browser on the device) and click View Intune App Status
Then select an app, for example Outlook, from the scroller at the top and scroll down to ProtocolExclusions near the bottom – once your new addition is listed here you can test to see if you can open the new app from a link in the source app:
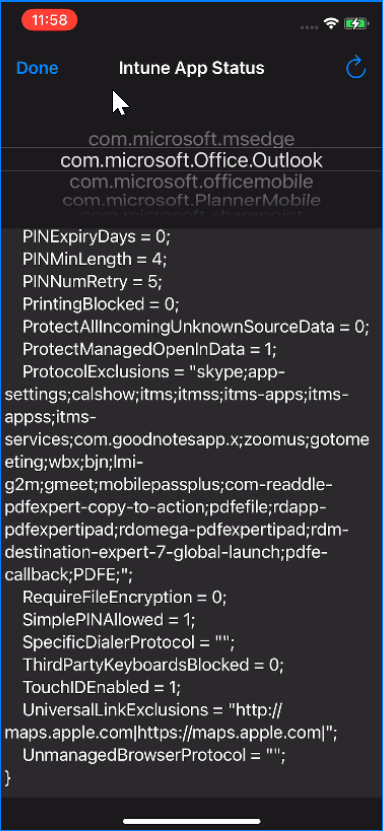
For example, in the above I have the following URL Schemes added as well as some I am still testing:
- zoomus = Zoom
- us.zoom.videomeetings4intune = Zoom For Intune
- gmeet = Google Meet
- bjn (or bjn-intunemam or bjn-a2m) = BlueJeans
- mobilepassplus = Mobile Pass+ from Thales
- otpauth = Duo Security
- com.mimecast.mobile.saml = Mimecast
- pdfe-callback (or pdfe2int1 or pdfefile) = PDF Expert
- Editor (or msauth.com.adobe.Adobe-Reader) = Adobe Reader
- com.microsoft.azureauthenticator = Microsoft Authenticator
- com.google.chrome.ios = Google Chrome
- com.microsoft.companyportal = Intune Company Portal
- com.microsoft.azureauthenticator = Microsoft Authenticator
- com.microsoft.copilot = Copilot AI Assistant
- com.microsoft.msedge = Microsoft Edge
- com.microsoft.Office.Excel = Microsoft Excel
- com.microsoft.skydrive = Microsoft OneDrive
- com.microsoft.Office.Outlook = Microsoft Outlook
- com.microsoft.Office.Powerpoint = Microsoft PowerPoint
- com.microsoft.skype.teams = Microsoft Teams
- com.microsoft.Office.Word = Microsoft Word
- com.slack.slackintune = Slack for Intune
- com.tinyspeck.chatlyio = Slack
- com.dealcloud.mobileapp = Deal Cloud
It is still a bit hit and miss once you have info.plist, but you have a list of values for the URL Protocol that you can test against now.
Note that I have added some Microsoft apps to the above list. This is because it is also possible, via Device Configuration Profiles for iOS in Intune, on a managed device (supervised, via Apple Business Manager) to control the notification prompts that an app presents at first use as well as the “Device Features > Single Sign On App Extension” feature. The above URL Schemes are used for these settings as well.
Leave a Reply to Ryan Cancel reply