Microsoft have released a tiny update to Exchange Online that has massive implications. I say tiny in that it take like 30 seconds to implement this (ok, may 60 seconds then).
When this is enabled, and below I will describe a simple configuration for this, your users when using Outlook Web Access on a computer that is not compliant with a conditional access rule in Azure AD, will result in OWA that is read only – attachments can be viewed in the browser only and not downloaded. There is even a mode to have attachments completely blocked.
So how to do this.
Step 1: Enable the OwaMailboxPolicy New Setting
Only users whose OWAMailboxPolicy have the ConditionalAccessPolicy set to ReadOnly or ReadOnlyPlusAttachmentsBlocked are impacted by this feature and only when the Conditional Access policy so restricts their session. For example if you wanted a subset of users to always have this restriction regardless, but not other users then you would create a new OwaMailboxPolicy and set the ConditionalAccessPolicy setting. Once that is done you would apply the policy to the selected users, but if you wanted this restriction to apply to all users, but only when they are on a personal (not-compliant or trusted), then you would apply the OWA policy to all users and the conditional access policy to All Users as well.
In my example I am just going to update the default policy, becuase I want read only view for all users who fall out of the conditions of the policy. So in Exchange Online PowerShell I run the following:
Set-OwaMailboxPolicy -Identity OwaMailboxPolicy-Default -ConditionalAccessPolicy ReadOnly
This, once the conditional access policy takes effect will restrict downloads in OWA. The second option is to use ReadOnlyPlusAttachmentsBlocked instead of ReadOnly. This blocks attachment viewing as well. The value “Off” turns off the restrictions again. “Off” is the default value.
Step 2: Create a Conditional Access Policy in Azure AD
You need an Azure AD Premium P1 licence for this feature.
Here I created a policy that applied to one user and no other policy settings. This would mean this user is always in ReadOnly mode. In real world scenarios you would more likely create a policy that applied to a group or All Users and excluding network ranges or compliant devices and not individual users and forced ReadOnly only when other conditions such as non-compliant device (i.e. home computer) where in use.
The steps for this are:
The pictures, as you cannot create the policies in the cmdline, are as follows:
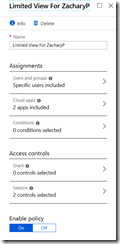
a) New policy with a name. Here it is “Limited View for ZacharyP”
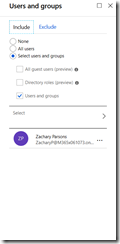
b) Under “Users and Groups” I selected my one test user. Here you are more likely to pick the users for whom data leakage is an issue
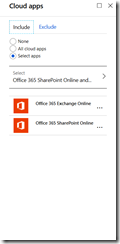
c) Under “Cloud apps” select Office 365 Exchange Online. I have also selected SharePoint, as the same idea exists in that service as well
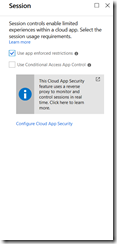
d) Under Session, and this is the important one, select “Use app enforced restrictions”. For Exchange Online, app enforced restrictions is the value of ConditionalAccessPolicy for the given user.
Step 3: View the results
Ensure the user is licenced to have a mailbox and Azure AD Premium P1 and ensure they have an email with an attachment in it for testing.
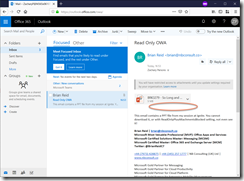
In the screenshot you can see circled where the Download link is normally found:
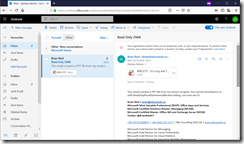
And where the attachment is clicked, there is now a greyed out Download button and a banner is seen in both views telling the user of their limited access.
The user interface to OWA (in 2018) looks as follows:
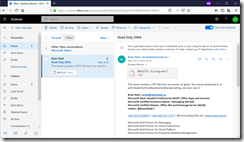
With ReadOnlyPlusAttachmentsBlocked set as the ConditionalAccessPolicy value, the attachment cannot be viewed. This is what this looks like (new OWA UI):
And SharePoint and OneDrive, just because it is very similar!
This is outlined in https://c7solutions.com/2019/04/read-only-and-document-download-restrictions-in-sharepoint-online
Leave a Reply