The Yubikey is a small USB connected hardware device that can generate a variety of security codes. Being virtually indestructible and easy to clip to a key ring (Yubikey 4) or leave inside your only device (Yubikey 4 Nano) you can now use this token to login to Windows. Once you have got your token from Yubico (via Amazon or other resellers) for around £40 you start the very simple Windows Hello authentication registration process by downloading the Yubikey app from Windows App Store. Signing in after a restart requires full credentials (password or PIN), which means a stranger who steals your PC and the YubiKey can’t use it to access your device
Open the Store app, search for Yubikey and click the logo for the app.
Click the Get button to install the app then then launch to start it. In a corporate environment you can push the app to your devices with MDM solutions like Intune.
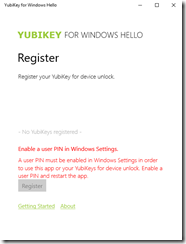
Launch the app. You will need to have a PIN login enabled for the device to work and so you will see a warning if you do not have this enabled.
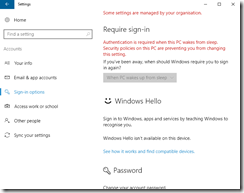
If you need to set up a PIN then close the Yubikey app and type “PIN” in the search box in Windows and choose “Setup PIN sign-in”
Scroll down and click Add under PIN. You will need to reenter your password so other people cannot set up a PIN on your behalf.
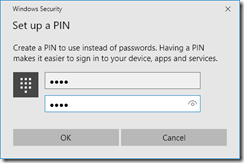
Enter a PIN and confirm the same PIN
You will now be able to use a PIN to sign in. The PIN setup process will continue and you will be asked to confirm your PIN again. You can now use your PIN to sign into your computer, which as it is tied to the computer hardware, is more secure than your password. But we are not stopping there – we can now restart the Yubikey app. Either launch it from the Store app, from the search box on the Start Menu or From the Start menu, select All Apps >Start > YubiKey for Windows Hello
Click Register to start the process of pairing your Yubikey to your computer
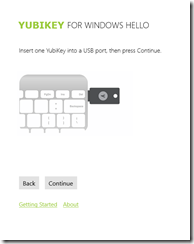
Insert your Yubikey into any USB port on the PC and press Continue
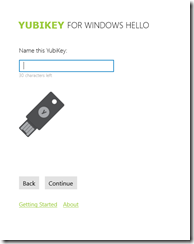
Name the Yubikey, as at login it will ask you to insert this named key. Click Continue once you have a name
At this point it should register the device and all is good!
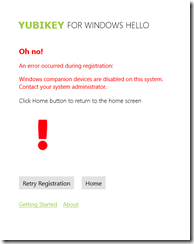
If you find that Windows Companion Devices are disabled then you will get this error:
It reads “Oh no! An error occurred during registration. Windows companion devices are disabled on this system. Contact your system administrator”. This is because the local security policy on your computer or network via your Active Directory and IT driven polices does not allow companion devices. On systems running Windows Pro or Windows Enterprise systems, you must enable the option to Allow companion device for secondary authentication in the Local Security Policy. If your organization manages your security policy, contact your IT administrator and request this change before installing this app. You cannot change local security policy on systems running Windows Home, however this option is enabled by default. Note that you will also get this on domain joined systems as well, as secondary auth is not supported on domain joined machines (even for individual users) at this time.
To modify local security policy
- Open the Local Group Policy Editor. To do this, press the Windows key, type R, and then type gpedit.msc.
- In the Local Group Policy Editor, from the top level Local Computer Policy, navigate to Computer Configuration > Administrative Templates > Windows Components > Microsoft Secondary Authentication Factor.
- In the right pane, click the link to Edit policy setting. (You can also double-click the setting to Allow companion device for secondary authentication.) The default state is Not configured.
- In the setting screen, select the option for Enabled, and click OK. If this option is already selected, your policy is set and you can click Cancel.
- Exit the Local Group Policy Editor and the Management Console.
Leave a Reply to ADUser Cancel reply