The Microsoft AntiMalware agent is a virtual machine extension in Azure that adds support for build in antimalware management within your virtual machines hosted in Azure. The agent can be added easily when you are creating a new VM, which we will show first below using the resource manager model, but also can be added after the virtual machine creation and updated with changes as you need. We will show how to do that in the section part of this article.
Adding AV protection to new VM
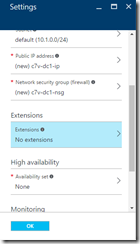
The addition of malware protection to your new virtual machine happens during the VM creation process. To add it create a new VM in the Azure portal and from the Settings blade choose Extensions
Click Add Extension:
Click Add extension and then choose Microsoft Antimalware
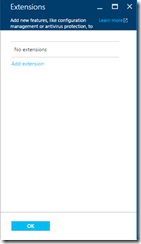
From the Install Extension blade enter your exclusions, scan times etc. as required:
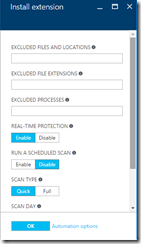
To enable antimalware with the default configuration, click Create on the Add Extension blade without inputting any configuration setting values. To enable antimalware with a custom configuration, input the supported values for the configuration settings provided on the Install Extension blade and click OK. Monitoring the antimalware is done via Windows Event Logs and is enabled automatically to your selected storage account.
Before you click OK, click Automation Options and grab the scripts needed to modify this extension later. Copy the Template text into Wordpad (not Notepad) and then copy paste again into Notepad if you want to just quickly edit it. Or use an editor of your choice, but make sure the line breaks etc. remain the same as directly pasting into Notepad breaks the line breaks!
Click the PowerShell tab (shown) and copy the code from here. This code is used to upload the template that you just downloaded with changes to allow you to adjust the settings on the Microsoft Antimalware settings on your virtual machine later. See more on that below.
Once you have downloaded or copied the code close the Template blade and click OK on the Install extension blade.
Click OK on the Extensions blade. Click OK to create your virtual machine.
Adding Microsoft Antimalware To existing virtual machines
To customise the Microsoft Antimalware extension on an existing virtual machine or to install it on a virtual machine where it does not exist becuase it was not added when the server was initially provisioned. Both of these scenarios, updating settings and adding new are covered in this section.
Both of these scenarios require scripting and cannot be configured in the portal, unlike the install during virtual machine provisioning.
Adding Microsoft Antimalware to an existing virtual machine
The first thing that you need to do to add Microsoft Antimalware is the template. If you ran through the above steps you would have downloaded the template as an additional step in the creation process. If you did not grab a copy of the template then it looks similar to this. The template provided by Microsoft takes input from the PowerShell that you also downloaded. In its simplist form it can be reduced to the following:
{ "AntimalwareEnabled": true, "RealtimeProtectionEnabled": "true", "ScheduledScanSettings": { "isEnabled": "false", "day": "7", "time": "120", "scanType": "Quick" }, "Exclusions": { "Extensions": "", "Paths": "", "Processes": "" } }To customise this template just each of the values and save the file to the filesystem. If you use the above template without change then you get the default settings for the extension, so the “blank” template is actually functional. In the template Paths is a semicolon delimited list of file paths or locations to exclude from scanning, where each path is escaped, so for example c:\\temp\\blog would be the value if you wanted to exclude c:\temp\blog and all subdirectories from being scanned. Extensions is again a semicolon separated list starting with the dot, so “.ci;.edb;.log;” would be a valid string. Processes is again semicolon separated list of processes. RealtimeProtectionEnabled and isEnabled are true or false and day is 1=Sunday and 7=Saturday etc. Time is the number of hours past midnight, so 180 is 3am
We will take the default template and use it to add the extension to an existing virtual machine that does not have the extension.
To add the extension to an existing virtual machine we need to login to Azure using PowerShell. This starts with Login-AzureRmAccount cmdlet. Once you are logged in, if you have more than one subscription, use Select-AzureRmSubscription to select the subscription that contains your virtual machine.
To check if Microsoft Antimalware is already enabled on a virtual machine run the following PowerShell:
$resourceGroupName = "<name of resource group>" $vmname = "<name of vm>" Get-AzureRmVMExtension -ResourceGroupName $resourceGroupName –VMName $VMName -Name "IaaSAntimalware"If some JSON is returned, then the Microsoft Antimalware extension (IaaSAntimalware) is enabled on this virtual machine. Note that PublicSettings “AntimalwareEnabled:” shows if the extension is actually running on the virtual machines, and not just that the extension exists on the virtual machine. If an error is returned then the extension is not enabled on the virtual machine.
To add the extension to an existing virtual machine you either need the full template JSON file above, if you want lots of customization, or if you want to do it simply then you can use a very small bit of JSON:
‘{ "AntimalwareEnabled": true,"RealtimeProtectionEnabled": true}’;The above JSON enables the AV software and turns on real time protection. If you want more control, use the full JSON file above, with your customizations, saved to the filesystem.
The code to use the above JSON or the JSON file is:
# Use this "-SettingString $SettingsString" value for simple setup $SettingsString = ‘{ "AntimalwareEnabled": true,"RealtimeProtectionEnabled": true}’; # Use this "-SettingString $MSAVConfigfile" to configure from JSON file $MSAVConfigfile = Get-Content "C:\Scripts\IaaSAntimalware.json" -RawThe code to add the extension is as follows. To run the below you need to set the $location variable to the same location string as the virtual machine. To get this you can run:
$location = (Get-AzureRmVM -VMName $VMName -resourceGroupName $resourceGroupName).locationYou also need the available version numbers for the extension, and to use the latest version of the extension. To work this out you need the following script snippet:
$allVersions= (Get-AzureRmVMExtensionImage -Location $location -PublisherName "Microsoft.Azure.Security" -Type "IaaSAntimalware").Version $typeHandlerVer = $allVersions[($allVersions.count)–1] $typeHandlerVerMjandMn = $typeHandlerVer.split(".") $typeHandlerVerMjandMn = $typeHandlerVerMjandMn[0] + "." + $typeHandlerVerMjandMn[1]So to actually set the extension on the virtual machine, run the following:
Set-AzureRmVMExtension -ResourceGroupName $resourceGroupName -VMName $VMName -Name "IaaSAntimalware" -Publisher "Microsoft.Azure.Security" -ExtensionType "IaaSAntimalware" -TypeHandlerVersion $typeHandlerVerMjandMn -SettingString $SettingsString -Location $locationCustomizing Microsoft Antimalware deployments in Azure
Once the extension is enabled you can customize the settings by uploading a config file or settings string with adjusted settings. For example is I took a copy of my above config file and changed time so the value was now 180 (instead of 120 as shown) and I set an Extensions and Paths value in the file, then I would update my virtual machine using the following:
$MSAVConfigfile = Get-Content "C:\temp\blog\Antimalware Azure\antimalware-edit.json" -Raw Set-AzureRmVMExtension -ResourceGroupName $resourceGroupName -VMName $VMName -Name "IaaSAntimalware" -Publisher "Microsoft.Azure.Security" -ExtensionType "IaaSAntimalware" -TypeHandlerVersion $typeHandlerVerMjandMn -SettingString $MSAVConfigfile -Location $locationThe other values have not changed from the above, so you still need to work out $typeHandlerVerMjandMn, $location etc.
Once you have applied the settings then you can use Get-AzureRmVMExtension -ResourceGroupName $resourceGroupName –VMName $VMName -Name “IaaSAntimalware” to check the settings have applied – it usually takes a minute or two for the correct data to be returned to show the change in place.
Leave a Reply