I had been struggling with password writeback testing and was coming across the following set of errors, and found that searching for them uncovered nothing online. So I wrote this blog to remind me and help you solve these issues. These errors are all visible in the Application log of the Event Viewer.
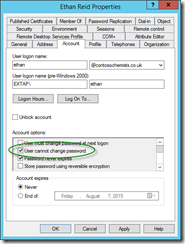
User Restrictions
The following error is because the user has “user cannot change password” option set in Active Directory:
EventID 33004: TrackingId: 7344da2c-ab9d-42ef-adea-4a17d07fdeb9, Reason: Synchronization Engine returned an error hr=80230626, message=The password could not be updated because the management agent credentials were denied access., Context: cloudAnchor: User_9b83f544-ba22-4ffb-bff5-c1c2374d654c, SourceAnchorValue: F39SWQrM2EidaboN8UC8Ww==, UserPrincipalName: ethan@contoso.co.uk, Details: Microsoft.CredentialManagement.OnPremisesPasswordReset.Shared.PasswordResetException: Synchronization Engine returned an error hr=80230626, message=The password could not be updated because the management agent credentials were denied access.
at AADPasswordReset.SynchronizationEngineManagedHandle.ThrowSyncEngineError(Int32 hr)
at AADPasswordReset.SynchronizationEngineManagedHandle.ChangePassword(String cloudAnchor, String sourceAnchor, String oldPassword, String newPassword)
at Microsoft.CredentialManagement.OnPremisesPasswordReset.PasswordResetCredentialManager.ChangePassword(String encryptedChangePasswordRequestString, String publicKeyEncryptedSymmetricKey, String publicKeyEncryptedSymmetricIV)
And also, as the second error generated:
Event ID 6329: An unexpected error has occurred during a password set operation.
“BAIL: MMS(5716): ..\server.cpp(11139): 0x80230626 (The password could not be updated because the management agent credentials were denied access.)
Azure AD Sync 1.0.8641.0″
Group Policy Restrictions
Its possible that the errors you see for password writeback in the application log are due to restrictions on the user’s password that they have chosen. If the password is not complex enough then you get a warning in the password reset page the user is visiting in Azure, but you can also get this is a Group Policy restriction is in place even if you have set a strong password. The text in the error message in the Azure password change portal reads “This password does not meet your corporate password policy. Please make sure to use a mix of upper and lowercase letters, numbers, symbols, and to update your password to one that you haven’t used previously.”. Therefore though Azure accepted the passwords (original and new) the on-premises server rejected them with the following:
Event ID 33008: TrackingId: 3c8c78dc-9167-4286-9384-e2f0e777af87, Reason: Synchronization Engine returned an error hr=80230619, message=A restriction prevents the password from being changed to the current one specified., Context: cloudAnchor: User_9b83f544-ba22-4ffb-bff5-c1c2374d654c, SourceAnchorValue: F39SWQrM2EidaboN8UC8Ww==, UserPrincipalName: ethan@contoso.co.uk, Details: Microsoft.CredentialManagement.OnPremisesPasswordReset.Shared.PasswordResetException: Synchronization Engine returned an error hr=80230619, message=A restriction prevents the password from being changed to the current one specified.
at AADPasswordReset.SynchronizationEngineManagedHandle.ThrowSyncEngineError(Int32 hr)
at AADPasswordReset.SynchronizationEngineManagedHandle.ChangePassword(String cloudAnchor, String sourceAnchor, String oldPassword, String newPassword)
at Microsoft.CredentialManagement.OnPremisesPasswordReset.PasswordResetCredentialManager.ChangePassword(String encryptedChangePasswordRequestString, String publicKeyEncryptedSymmetricKey, String publicKeyEncryptedSymmetricIV)
and
Event ID 6329: An unexpected error has occurred during a password set operation.
“BAIL: MMS(5236): ..\server.cpp(11139): 0x80230619 (A restriction prevents the password from being changed to the current one specified.)
Azure AD Sync 1.0.8641.0″
This of course seems self explanatory – your password is not complex enough for your rules on-premises but complex enough to get past the Azure initial checks that it imposes.
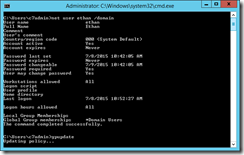
This error though is especially annoying in test scenarios where you have turned off all the complexity checks. To test why you are getting this error, first check its a password change error and not something else, and try and change the users password on-premises. You should get the same restriction. Then use the cmd prompt to check the password settings for the user.
</p> <p>net user username /domain</p> <p>
This will report the following:
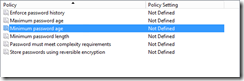
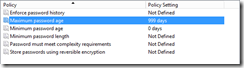
In this example, notice the highlighted. Here there password minimum age requirement in Group Policy has been removed:
But the domain controller (after running gpupdate to force the change to the domain controller) still enforces a single day to allow the change to occur.
For test scenarios, modify group policy to 0 days (rather than not defined) and probably increase the max age from the suggested default of 30 days:
After running gpupdate, you get the following for the net user command:
Password last set 7/8/2015 10:42:05 AM
Password expires Never
Password changeable 7/8/2015 10:42:05 AM
Now you should be able to change your password in Azure against an on-premises user.
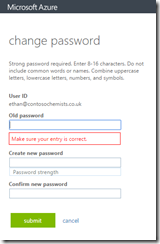
Strong Password Required
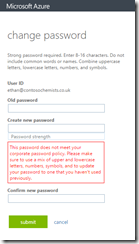
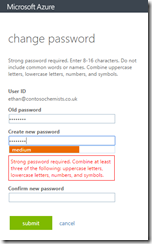
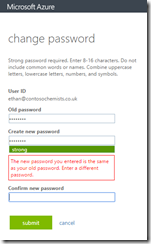
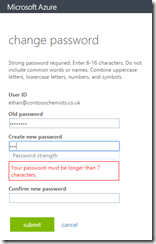
In the password change portal, the user is required to enter a strong password regardless of any restrictions that you have on-premises. So even if you are testing and have removed all history and complex and renewal requirements for the password, Azure will ensure that a strong password of 7 or more characters is entered regardless of your on-premises policy. In fact, Azure does not know your on-premises policy for password restrictions and enforces its own in addition to the one you have.
You get errors in the portal that read “Strong password required. Combine at least three of the following: uppercase letters, lowercase letters, numbers, and symbols.”. You also cannot reset the password to the same and the errors you get look like the following options:
Success
For completion of the blog, here is what you should see in the event log when it is working:
Event ID 31006: TrackingId: f430189d-984c-41d5-a4a6-333c66ffae1f, ChangePasswordRequestStart, Details: ethan@contosochemists.co.uk
Event ID 31007: TrackingId: f430189d-984c-41d5-a4a6-333c66ffae1f, ChangePasswordSuccess, Details: Context: cloudAnchor: User_9b83f544-ba22-4ffb-bff5-c1c2374d654c, SourceAnchorValue: F39SWQrM2EidaboN8UC8Ww==, UserPrincipalName: ethan@contosochemists.co.uk
Leave a Reply to shevopato Cancel reply