Category: transport
-
Mail Flow To The Correct Exchange Online Connector
In a multi-forest Exchange Server/Exchange Online (single tenant) configuration, you are likely to have multiple inbound connectors to receive email from the different on-premises environments. There are scenarios where it is important to ensure that the correct connector is used for the inbound message rather than any of your connectors. Here is one such example.…
-
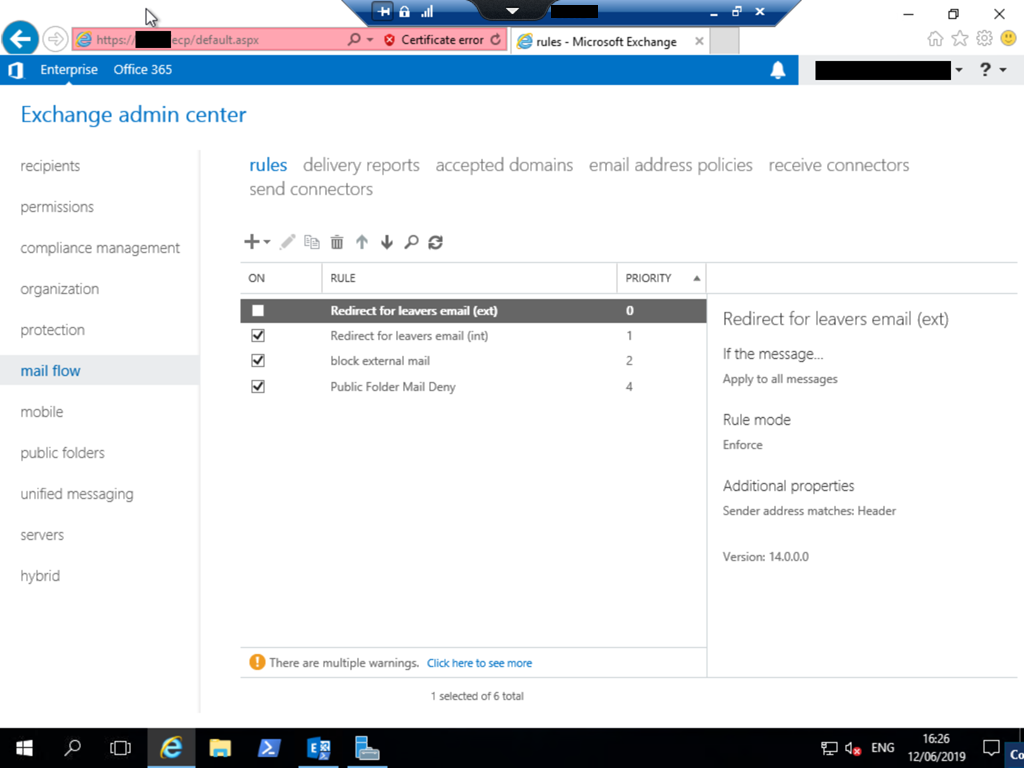
Exchange Transport Rules Corrupt On Installing New Exchange Server Version
When you install Exchange Server into an existing Exchange organization, your existing configuration typically remains intact and associated with the previous servers and some configuration, that is global in nature, also works across both versions. I can across a scenario where this does not work the other day. The scenario was the installation of Exchange…
-
Speaking at TechEd Europe 2014
I’m please to announce that Microsoft have asked me to speak on “Everything You Need To Know About SMTP Transport for Office 365” at TechEd Europe 2014 in Barcelona. Its going to be a busy few weeks as I go from there to the MVP Summit in Redmond, WA straight from that event. My session…
-
The New Rights Management Service
This blog is the start of a series of articles I will write over the next few months on how to ensure that your data is encrypted and secured to only the people you want to access it, and only for the level of rights you want to give them. The technology that we will…
-
Secret NSA Listening Ports in Exchange Server 2013? Of Course Not…
But what do those extra ports in Exchange Server 2013 that are listening actually do. If you bring up a command prompt on an Exchange Server 2013 machine and run netstat –ano | find “:25”. You will get back a list of IP addresses that are listening on any port starting 25. The last number…
-
The Exchange Server Header Firewall
The below Header Firewall video was recorded as “pre-reading” for the Exchange 2010 MCM program. The website that originally hosted this video is no longer available, so I am reposting the video that I recorded here:
-
Ensuring Email Delivery Security with Exchange 2013
To force Exchange 2013 to guarantee the secure delivery of a message can be done a few different ways. In this version of the product and in previous versions it was possible to create a send connector for a given domain and enable Mutual TLS on the connector. Then all messages to the domain(s) that…
-
Moving Exchange Online Protection Junk Mail to the Junk Email Folder
If you use Exchange Online Protection (EOP) to filter your email in the cloud and to remove spam and malware before onward delivery to you, and if you use Exchange 2007 or later on-premises, then you need to configure Exchange to move detected spam to the Junk Email folder in Outlook. By default EOP detects…
-
Removing Edge Subscription When Exchange 2013 Installed
Exchange 2013 does not have an Edge role (at the time of writing – Aug 2013). It is possible to use Exchange 2010 SP3 and install the Edge role should you need one. There is a problem though when it comes to removing the Edge Subscription between an organization that contains Exchange 2013 servers and…
-
Journal Alternative Mailbox and No Inbox Rules
In the event of your journal mailbox going offline, any journal reports destined for these mailboxes will queue. After two days (though this time is the expiry time for messages in your Exchange organization, so may be different) the message will expire and an NDR sent to the sender of the journal report. The problem…
-
Domain Secure and Edge Servers
I was asked a question recently on the Microsoft Certified Master course for Exchange 2010 and was told that the answer was not clearly written up on the internet. So I thought I would write this blog post. The question was based on the idea that Domain Secure worked from a Hub Transport server in…
-
Enabling Exchange 2013 to Filter OneNote and Publisher Files
Exchange Server 2013 includes the Search Foundation product to index and search most of the file types that needed IFilters installed for in previous versions including PDF files, so the Adobe IFilter is no longer needed. That said, it does not filter OneNote and Microsoft Publisher files. To filter these files so that you can…
-
Missing the Message Tracking Log Explorer in Exchange 2013? Not anymore…
Exchange 2013 has removed a number of user interfaces that existed in Exchange 2010, one of them being the Message Tracking toolbox utility: In Exchange 2013 you can search for an individual messages in the Exchange Control Panel (https://servername/ecp) by selecting mail flow > delivery reports. But this tool requires you to specify the source…
-
Create Shadow Redundancy Cross Forest in Exchange 2010
Send connector cross forest shadow redundancy New-SendConnector ToTailspin -AddressSpaces SMTP:tailspin.com -SmartHosts mail.tailspin.com -ProtocolLoggingLevel verbose -DNSRoutingEnabled $False -SmartHostAuthMechanism ExternalAuthoritativeGet-SendConnector ToTailspin | Add-ADPermission -user “MS Exchange\Externally Secured Servers” -ExtendedRights ms-Exch-SMTP-Send-XShadow Receive connector cross forest shadow redundancy New-ReceiveConnector FromFabrikam -RemoteIPRanges 192.168.100.1 -Bindings 0.0.0.0:25 -ProtocolLoggingLevel verbose -Banner “220 Tailspin XShadow SMTP Server” -AuthMechanism ExternalAuthoritative Get-ReceiveConnector FromFabrikam | Add-ADPermission…
-
Creating GeoDNS with Amazon Route 53 DNS
UPDATE: 13 Aug 2014 – Amazon Route 53 now does native GeoDNS within the product – see Amazon Route 53 GeoDNS Routing Policy A new feature to Exchange 2013 is supported use of a single namespace for your global email infrastructure. For example mail.contoso.com rather than different ones for each region such as uk-mail.contoso.com; usa-mail.contoso.com…
-
How To Speed Up Exchange Server Transport Logging
In Exchange 2010 SP1 and later any writing to the transport log files for activity logging (not the transaction logging on the mail.que database) is cached in RAM and written to disk every five minutes. In a lab environment you might be impacted by this as you might have sent an email and want to…
-
Shadow Redundancy and Server Outages
Exchange Server 2010 has a feature that tries to ensure that emails in transport cannot be lost. This feature is called Shadow Redundancy and lots of information on how it works can be found on the Internet. But what happens if a mailbox server or site is unavailable? Items will queue in a single location,…