I have a requirement to ensure that Office 365 users external to the network of one of my clients need a second factor of authentication when accessing Office 365 resources from outside the corporate network. The free Multi-Factor Authentication (MFA) feature of Office 365 will not distinguish between network location so we need to enable MFA on ADFS (or Federated) authentication for external connections. External connections are those that come through a WAP server to the ADFS server and not those that come to ADFS directly.
To set this up, first install ADFS on Windows Server 2012 R2 and install additional ADFS servers and load balancers as required. Install the WAP servers in your DMZ and connect them to the on-premises ADFS server(s). Once this is all up and running enable MFA in Azure. You will need to create an MFA instance for billing purposes. Once this is created you can download the MFA software to the ADFS Server. For this blog we are using MFA Server version 7, released April 2016. This version does not need .NET 2.0 installed and works with .NET 4.0
On the ADFS Server run the MFA installer and follow the prompts. Make sure you have the Dec 2014 Cumulative Update or later (preferable the latest) installed. Accept the prompts for the two Visual C++ Runtime installations and complete the installation.
Following installation the wizard runs to configure MFA and MFA replication. I suggest making a group (called ADFS) and not using the default and setting up replication. The email address and password is obtainable from the MFA download page and is valid for 10 minutes.
Once installed start the MFA software and go to the AD FS page. Install the AD FS connector by pressing the button. On the primary ADFS server you then need to enable ADFS/MFA integration by running in PowerShell .\Register-MultiFactorAuthenticationAdfsAdapter.ps1. You can find this in Program Files\Multi-Factor Authentication Server. This is not needed on secondary servers.
Repeat the MFA install on all ADFS servers and install the MFA connector.
To allow users to set their own phone number and MFA settings install the SDK, User Portal and Mobile App features. These are detailed below:
User Portal
This requires that you install IIS/Web Server role on the server. In the role services for IIS include the HTTP Redirection feature, the ASP.NET 4.5 feature (under Application Development) and IIS 6 Metabase Compatibility (under IIS 6 Management Compatibility). Other role services are added because of these options.
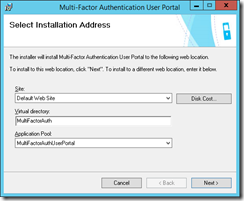
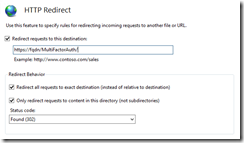
Accept the prompts to create the users. You will be taken to a page about virtual directories. I tend to select the defaults here, apart from the app pool, which I set the the one that matches the name of the feature I am installing. I use HTTP Redirect feature to redirect the user from the root directory to HTTPS://fqdn/MultiFactorAuth.
Once the User Portal is installed I set the relevant options in the MFA admin program such as the User Portal URL and the auth methods allowed. If you are going to install the Mobile App feature then allow users to use this option.
If you are configuring HTTP Redirection then set this on the root directory of the default website now. Redirect only the root directory to HTTPS://fqdn/MultiFactorAuth
Make sure you turn HTTP Redirect off on all subdirectories and virtual directories of the application will not be reachable. Also check that HTTPS is bound to a certificate in IIS and to the website.
SDK
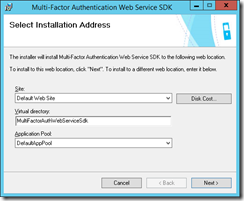
To install the SDK go to the Web Service SDK node in MFA on each ADFS server and click the Install Web Service SDK button. This requires Basic Authentication enabled in IIS. This is not a default role service, so you will need to add it to the server at this time.
Install the SDK and select the defaults:
If you have HTTP Redirection enabled, check it is disabled for the virtual directory as it won’t be by default.
Mobile App
To use the Azure Authenticator app to sign in to ADFS (as a second factor of authentication) you need to enable the Mobile App and have the URL reachable from the internet. The URL can be published through the WAP servers as these are available to you. To publish the MFA mobile app through WAP you can use the following cmdlet (changing the URL and certificate thumbprint as required):
Add-WebApplicationProxyApplication -BackendServerUrl ‘https://auth.domain.co.uk/mfaApp/’ -ExternalCertificateThumbprint ‘xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx’ -ExternalUrl ‘https://auth.domain.co.uk/mfaApp/’ -Name ‘Multi-Factor Authentication’ -ExternalPreAuthentication PassThrough -ClientCertificateAuthenticationBindingMode None -BackendServerCertificateValidation None -InactiveTransactionsTimeoutSec 300 -ClientCertificatePreauthenticationThumbprint ”
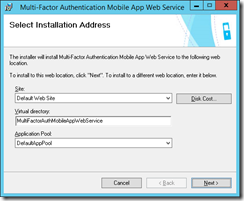
The mobile app needs to be installed on each ADFS server. Do this by opening a command prompt as admin and browse to the installation folder of the MFA server (C:\Program Files\Multi-Factor Authentication Server). Then run MultiFactorAuthenticationMobileAppWebServiceSetup64.msi
Change the Virtual Directory to something short, as users might need to enter this on their phone. I use mfaApp for this. Install and when finished If you have HTTP Redirection enabled, check it is disabled for the virtual directory as it won’t be by default.
Open this folder in admin cmd prompt (C:\inetpub\wwwroot\mfaApp in my case) and edit web.config. Modify the following two keys as follows:
<add key=”WEB_SERVICE_SDK_AUTHENTICATION_USERNAME” value=”” />
<add key=”WEB_SERVICE_SDK_AUTHENTICATION_PASSWORD” value=”” />
The username and password here needs to be a member of the PhoneFactor Admins group in Active Directory.
Then locate <setting name=”pfpaws_pfwssdk_PfWsSdk” serializeAs=”String”> and change the Value string that follows from http://localhost:4898/PfWsSdk.asmx to https://fqdn/MultiFactorAuthWebServiceSdk/PfWsSdk.asmx.
Finally enter the MFA App URL in the Mobile App section of the MFA admin program – this setting needs to be done once, as it will replicate to the other servers.
Restart the servers and you are ready to go.
Leave a Reply