Category: smartphone
-
Exchange OWA and Multi-Factor Authentication
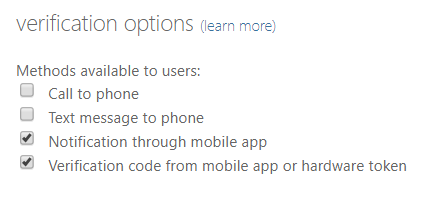
This article is now out of date Multi-factor authentication (MFA), that is the need to have a username, password and something else to pass authentication is possible with on-premises servers using a service from Windows Azure and the Multi-Factor Authentication Server (an on-premises piece of software). The Multi-Factor Authentication Server intercepts login request to OWA,…
-
Can’t Update Media Player Library on Windows SmartPhone
I have found for a while now that I could not view the Windows Media Player library on my phone, and everytime I viewed the library I got a dialog saying “An unexpected error occured”. But now I have fixed it. It must have been a corrupt copy of the libary database on the SDCard…