If you join a Windows 10 PC to Azure AD and then try and login to that PC over remote desktop you are in for a barrel of laughs! Or not!
The way to get it to work is as follows:
- Ensure that Windows 10 PC is running Version 1511 or later (type WinVer from the Run dialog)
- Ensure the target PC is enabled for Remote Desktop
- Ensure the Network Level Authentication is disabled
- Run MSTSC on your PC (the source) and enter the target PN name, your username (email address) and click Save As (which you will find under “Show Options”):
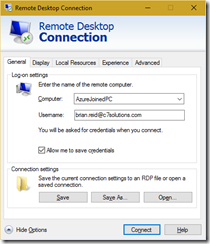
- Close the Remote Desktop Connection window without connecting.
- Open the saved RDP file in Notepad
- Add the following to the bottom of the text in Notepad as shows:
enablecredsspsupport:i:0
- In Notepad this appears as:
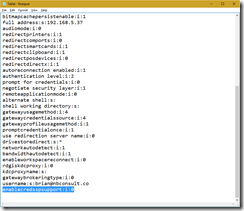
- Save the RDP file and then double-click it to connect. You will now be able to login with your AzureAD account over Remote Desktop
- If you cannot login, check the alternative name that your device uses for your user account. On the AzureAD joined computer, logged in as the target user, run “whoami” from the command line. It will report something like AzureAD\firstlast. You could try that value (both AzureAD and the name) as your username.
Leave a Reply to Brian Reid Cancel reply