From 1st March 2026 through to end of April 2026 Microsoft will start to reject some, and eventually all, SMTP AUTH connections (basic or legacy auth to SMTP endpoints) in Exchange Online.
This will not affect modern authentication connections using an app registration/Enterprise Application in your tenant nor any login able to do MFA (as this is also modern authentication). But it will impact any device or service that is unable to do anything but legacy authenticated communications to Exchange Online. All the other protocols apart from SMTP for legacy authentication were turned off in October 2022 and at that time it was an “on” then “off” process. This time connections will start to be rejected on 1st March at a low percentage and reaching 100% on 30th April 2026.
So what do you need to do before 1st March if you have applications or devices that can only do legacy SMTP Auth? Assuming you cannot move them to modern auth, which is the best answer, you need to move the service or device to use a new endpoint that supports SMTP AUTH. Microsoft have two cloud options and there are others by other providers. Microsofts two cloud options are the High Volume Email service or Azure Communication Services. You could redirect your apps and devices to Exchange Server if you have that installed, as this change is for Exchange Online only.
This article will look at the sets to create a user for High Volume Email (HVE) and all the other things you might need to check and configure. These will be, with the details following:
- Create a new HVE account
- Or replace an existing account with a HVE account
- Configure your legacy authentication Conditional Access rules
- Configure your Exchange Online Authentication policies
- Test your service
- Deploy.
So lets begin. You have two choices when it comes to a HVE account and that is a new one with a different email address from the one you are using for SMTP AUTH at present or you delete your current SMTP AUTH account and create a new HVE account. HVE accounts are created in Exchange Online or via Exchange Online PowerShell and CANNOT be users synced from Active Directory or existing Entra ID accounts. So if you have an account with an existing email address and need to reuse that address, this change becomes an out of hours change as you need to delete the current account, which will lose you access to the mailbox, or remove the email address from the existing account (replacing it with another if required) which will keep the mailbox and its data but free up the email address. HVE accounts do not have licences or mailboxes – they are for email sending over SMTP only.
Once the email address is out of use, or you don’t mind creating a new email address, it is time to make the HVE account. This is made from Exchange Online Admin Center (https://admin.cloud.microsoft/exchange) > Mail Flow > High Volume Email. Click Add an HVE account.
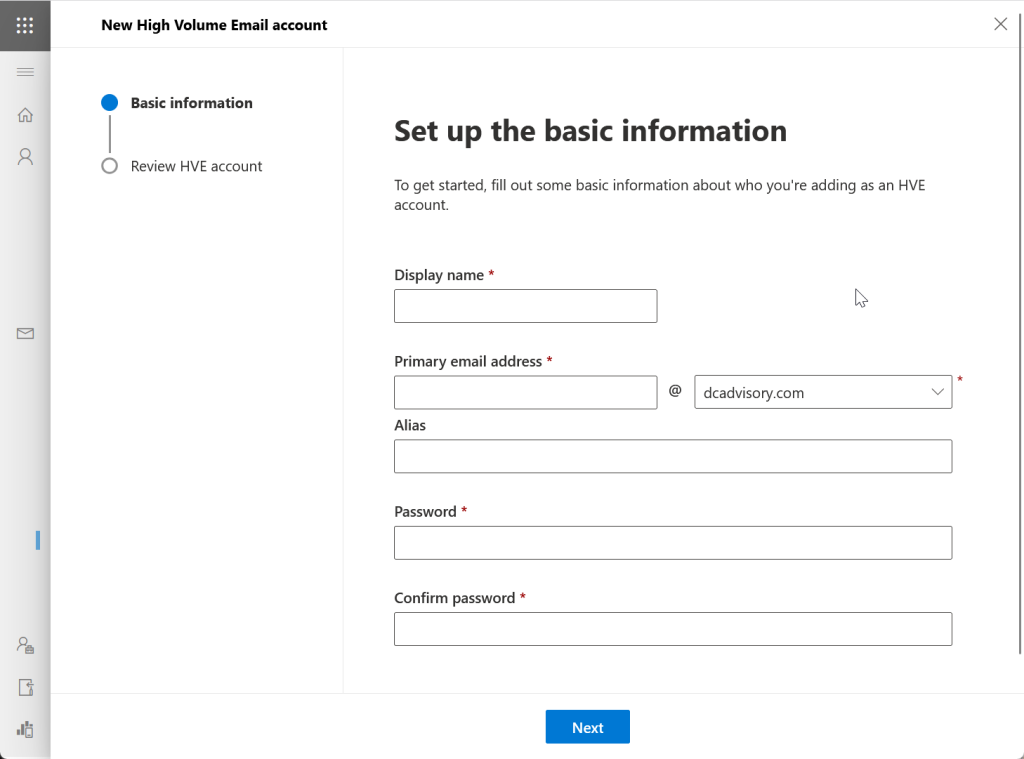
This can also be done from Exchange Online PowerShell:
$securePassword = Read-Host "Enter password" -AsSecureString
New-MailUser -HVEAccount -Name "HVE Account" -Password $securePassword -PrimarySmtpAddress "HVEAccount@contoso.com"
This is now ready to use, if you do not have Conditional Access policies, Secure Defaults enabled or Exchange Online Authentication policies. So as the assumption will be you have at least two of these in place we will look at what you need to do.
For Conditional Access policies, if you have any policies for blocking legacy authentication, the HVE account needs to be exempted from this policy. Best thing to do is to create a group called (say) “Exchange-HVEUserAccounts” in Entra ID. Note that when adding these users to the group you can only search for the user by the display name that provided and not by email address or other properties. In PowerShell above the Name value is used for both the Name and DisplayName attributes.
With this group and the HVE users added to it, exclude this group from any Conditional Access rule that blocks legacy authentication and any rule that requires MFA or compliant devices.
If you have a Conditional Access rule that blocks unknown devices, exempt this group from that rule as well.
If in early 2025 you had no Conditional Access rule to block legacy authentication, or have created a new tenant since then, you will see a “Microsoft Managed” Conditional Access rule called “Block legacy authentication”. You will need to add your group to the exclusion list for this policy.
If you are using Security Defaults to protect your tenant then you will need to turn these off – they do not work with High Volume Email users because they block legacy authentication. We strongly recommend that you move to a Conditional Access model (requiring Entra ID Plan 1 licences) if you need HVE users as you need Security Defaults OR Conditional Access rules – not having either is a serious security miss!
And finally, there is a setting in Exchange Online called the Authentication Policy. This dates back to before the shutdown of all the other legacy authentication protocols in October 2022, where you could create a policy to block those protocols before Microsoft did. There was also a page in the M365 Admin Center to turn these off and behind the scenes an Authentication Policy was made and applied to all users.
So, in Exchange Online PowerShell, check if you have an Authentication Policy, and check if that policy is set as the default. If you do and you only have one policy that has AllowBasicAuthSmtp set to False then you need to create a new policy with AllowBasicAuthSmtp set to True and assign that policy to the HVE user account. The PowerShell for all this is as follows:
# Check if you have Authentication Policies
Get-AuthenticationPolicy | FL Name
# Check if it is used as the organization wide default
Get-OrganizationConfig | FL DefaultAuthenticationPolicy
# Check if that policy listed as the org default blocks SMTP Auth
# If this returns False you need to have another policy that has this set to True
Get-AuthenticationPolicy BlockBasic* | FL AllowBasicAuthSmtp
# Creating a new Authentication Policy if required
New-AuthenticationPolicy "Allow Basic Auth SMTP" -AllowBasicAuthSmtp
# Assign this SMTP Auth allowed policy to the HVE user account and reset any authentication token so this policy takes effect immediately
Set-User HVEAccount@contoso.com -AuthenticationPolicy "Allow Basic Auth SMTP" -STSRefreshTokensValidFrom $([System.DateTime]::UtcNow) -Confirm:$false
If you have no Authentication Policies then nothing to do here. You are not impacted by turning off SMTP Auth on individual accounts or disabling Direct Send, which are two related to SMTP policies that you might recently have set.
Finally, time to test your HVE Account. For this we are going to use the deprecated Send-MailMessage, but it works for this scenario. Remember that HVE only supports internal emails, so the recipient of the test needs to be a mailbox in your tenant. This PowerShell will first prompt for the username and password of the HVE Account and then send an email using the HVE endpoint.
$cred = Read-Host -AsSecureString -Prompt "HVE Account Credentials"
Send-MailMessage -SmtpServer smtp-hve.office365.com -To user@contoso.com -From HVEAccount@contoso.com -Subject "HVE Test" -Body "This is a simple test email via HVE" -BodyAsHtml -Credential $cred -UseSsl -Port 587
This cmdlet uses the HVE endpoint of smtp-hve.office365.com. Once your test is successful, update your devices and applications with the new endpoint (so smtp.office365.com will NOT work here) and the new username and password.
If this is not working for you, and you are having issues with High Volume Email, then check my 2024 article on errors you might see or my 2025 article on some of the issues I have seen with the service.
Photo by Pixabay: https://www.pexels.com/photo/high-angle-view-of-paper-against-white-background-248537/

Leave a Reply