Category: security
-

What Is “mx.microsoft”?
mx.microsoft is the new MX delivery domain for Exchange Online. For years now it has been mail.protection.outlook.com, but this domain will not work with the new DNSSEC extensions that Exchange Online will start to support. When you added a new domain (called a vanity domain) to Microsoft 365, it would show you the MX record…
-

Windows LAPS and Granting Roles to Administrative Units
This blog post discusses how to create both a custom admin role for reading the LAPS password and settings stored in Entra ID and then assigning that role so that only device administrators of an Entra ID Administrative Unit can see the local admin password for the subset of devices they are able to manage.…
-

Entra ID Multi-Factor Authentication/Conditional Access and External Federation Implementation
I have a few clients (not many) who have external federation for Entra ID (previously Azure Active Directory) and over the last year or so have been looking into these and integrating them with Entra ID Conditional Access. This has become more of an issue recently with Microsoft’s recently creation of “Microsoft Managed” Conditional Access…
-

SSL Inspection and Microsoft 365
There are a number of features in Microsoft 365 that do not work if SSL Inspection (also known as TLS Interception) is enabled on your device or network provider. You need to disable the listed URLs that Microsoft provides in its documentation. The problem is there is a lot of disconnected documentation! This blog post…
-

Blocking More Obvious Phish – Attachment Filtering
One relatively easy way to block some categories of phishing email is to block the attachment type that is sent with some of these messages. For example, I have had a few of these recently: Hovering over the attachment I see the filename, and it ends .shtml. This attachment is for server-side HTML (SSI includes…
-

Adobe Creative Cloud and Conditional Access Restrictions
In Azure Active Directory it is possible to create Conditional Access rules that restrict applications to only running on company owned or managed devices. Conditional Access approves or rejects the login based on that knowledge – so what happens if the app in question is running on a company (managed or compliant) machine, but the…
-

More Frequent Quarantine Notifications in Exchange Online Protection
Available from the end of April 2023 there is now an option to increase the notification interval to end users about items in the quarantine. The Microsoft 365 Quarantine is at https://security.microsoft.com/quarantine and though this is a good link to add corporate intranets, its also a useful one for users to remember and bookmark. Up…
-
Conditional Access in Defender for Cloud (MCAS)
I was asked this question last week at Microsoft Ignite following a talk that I did, and as it was a question it was clearly not as clear cut as maybe I thought it was. The question was, “why is Conditional Access found in Azure AD and Defender for Cloud?” (Defender for Cloud was previously…
-
What Is “Multifactor Authentication Trusted IPs”
In Azure AD for location based conditional access rules you can select “Multifactor Authentication Trusted IPs” as a location. This short blog post outlines what this is. As an example of the use of this location, it could be used as follows in Conditional Access: The location selected in the above is “Multifactor Authentication Trusted…
-
Allowing “Phish” Training Emails in Exchange Online
With the introduction of “Secure by Default” in Exchange Online, where you used to add IPs and other settings such as allow-lists to allow your phish training emails to get through to your users this will no longer work, and shortly it will no longer work to bypass the Exchange Online filters using mail flow…
-
Intune MAM Exemptions – Discovering URL Protocols
In Microsoft Intune you can create a secure container where the data in your apps cannot leak outside of. That is, you can restrict copy/paste outside of the supported apps and restrict opening the data in a different app. But sometimes you need to open the data in a different app and with the Intune…
-
[New] External Email Notification in Exchange Online
This is a new feature released in March 2021 that adds support in Outlook (Mac, OWA, Mobile) for the display of the external status of the sender – note at the time of writing it does not add this feature to Outlook for the PC. This should be used to replace the way this has…
-
Free Web Content Filtering With Microsoft Defender ATP
Well free as in you need an MDATP licence first, but as this used to be an add on feature on top of MDATP with an additional cost, this is now effectively free once you are licensed for MDATP. The feature enables your organisation to track and regulate access to websites based on their content…
-
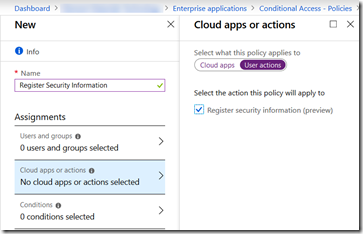
Register For Azure AD MFA From On-Premises Or Known Networks Only
A long request within Azure AD/Office 365 has been the request to be able to register your security info from a known location or only on certain other conditions. Well it looks like this has appeared in Azure AD in the last few days!! Its visible under Azure AD > Conditional Access > New/Existing Policy…
-
Improving Password Security In the Cloud and On-Premises
Passwords are well known to be generally insecure the way users create them. They don’t like “complex” passwords such as p9Y8Li!uk%al and so if they are forced to create a “complex” password due to a policy in say Active Directory, or because their password has expired and they need to generate a new one, they…
-
Forcing Transport Level Secure Email With Exchange Online
In Exchange Online there are a few different options for forcing email to require an encrypted connection. These depend upon the level of licence you have, and some of them are user based (Office 365 Message Encryption for example), but there are two ways to force TLS (transport layer security) for the email between when…
-
Securing Your Windows 10 Login With Yubikey
The Yubikey is a small USB connected hardware device that can generate a variety of security codes. Being virtually indestructible and easy to clip to a key ring (Yubikey 4) or leave inside your only device (Yubikey 4 Nano) you can now use this token to login to Windows. Once you have got your token…