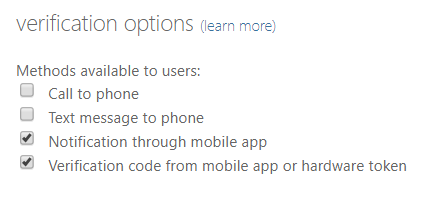
Category: MFA
-

Entra ID Multi-Factor Authentication/Conditional Access and External Federation Implementation
I have a few clients (not many) who have external federation for Entra ID (previously Azure Active Directory) and over the last year or so have been looking into these and integrating them with Entra ID Conditional Access. This has become more of an issue recently with Microsoft’s recently creation of “Microsoft Managed” Conditional Access…
-

Adobe Creative Cloud and Conditional Access Restrictions
In Azure Active Directory it is possible to create Conditional Access rules that restrict applications to only running on company owned or managed devices. Conditional Access approves or rejects the login based on that knowledge – so what happens if the app in question is running on a company (managed or compliant) machine, but the…
-

Migrating MFA Settings To Authentication Methods
Released to Azure AD in December 2022 there is now a process for migrating from the legacy MFA methods and Self-Service Password Reset (SSPR) authentication methods to the unified Authentication Methods policies in Azure AD. This migration window is open until Jan 2024 when the legacy methods will be disabled. This change will allow you…
-
Conditional Access Authentication Strengths
Newly released to Conditional Access in Azure AD is the “Authentication Strengths” settings. These allow you to control the strength of the authentication you need to be used for that conditional access rule. Before this feature was available you had the option of allowing access with no second factor, MFA as a second factor (any…
-
What Is “Multifactor Authentication Trusted IPs”
In Azure AD for location based conditional access rules you can select “Multifactor Authentication Trusted IPs” as a location. This short blog post outlines what this is. As an example of the use of this location, it could be used as follows in Conditional Access: The location selected in the above is “Multifactor Authentication Trusted…
-
Improving Security For MFA Approvals – Number Matching
Rolling out in November 2021 is a new feature – that of requiring the user to enter a number rather than just click approve on the MFA prompt. This update to Azure AD requires the use of Push Notifications and therefore requires the use of the Microsoft Authenticator app. It also requires that MFA is…
-
Adding Location To Azure AD MFA
This Azure AD feature is something that a number of other Multi-Factor Authentication providers have already implemented – that of showing the location of the user login (and the app in use) on the MFA prompt. This feature rolled out to Azure AD in mid November 2021 in preview – so use in non-production tenants…
-
MFA, Admin Roles and AADConnect Sync Failures
Come Feb 29th 2020 and Microsoft are turning off the baseline security policies. If you used these policies to do MFA for all admins (as that was an easy way to achieve this), then a replacement Conditional Access rule might cause errors with AADConnect. The reason being is that you could create a new Conditional…
-
MFA and End User Impacts
This article will look at the various different MFA settings found in Azure AD (which controls MFA for Office 365 and other SaaS services) and how those decisions impact users. There is lots on the internet on enabling MFA, and lots on what that looks like for the user – but nothing I could see…
-
Hardware Tokens for Office 365 and Azure AD Services Without Azure AD P1 Licences
A recent update to Azure AD Premium 1 (P1) licence has been the use of hardware tokens for multi-factor authentication (MFA). This is excellent news if your MFA deployment is stuck because users cannot use phones on the shop floor or work environment or they do not want to use personal devices for work activities.…
-
Token2 Hardware OAuth Tokens and Azure AD Access
This blog post walks through the process of logging into Azure AD resources (Office 365, other SaaS applications registered in Azure AD and on-premises applications that utilise Azure AD App Proxy). First step is to order your desired hardware. For this article we are looking at the devices manufactured by Token2 (www.token2.com). These include credit…
-

Configuring Multi Factor Authentication For Office 365
Given that Office 365 is a user service, the enabling of multi-factor authentication is very much as admin driven action – that is the administrators decide that the users should have it, or that it is is configured via Conditional Access when limiting the login for the user to certain applications and locations. For a…
-
Securing Your Windows 10 Login With Yubikey
The Yubikey is a small USB connected hardware device that can generate a variety of security codes. Being virtually indestructible and easy to clip to a key ring (Yubikey 4) or leave inside your only device (Yubikey 4 Nano) you can now use this token to login to Windows. Once you have got your token…
-
Azure MFA 503 Error When Authenticating
If you have installed version 7 of Azure MFA Server on-premises (7.0.0.9 or 7.0.2.1 at the time of writing) and have enabled IIS authentication with Forms Based authentication and the Native App, but when you need to authenticate you are presented with a 503 DLL error. The reason for this is that version 7 removed…
-
Upgrading Azure Multi-Factor Authentication Server
A new version of Azure MFA Server was released at the end of March 2016, version 7.0.0.9. This provides an in place upgrade to the previous version 6.3.1.1. This version is based on .NET 4.5 and not .NET 2.0, which is the big change in the product, along with new end user functionality in the…
-
Installing Azure Multi-Factor Authentication and ADFS
I have a requirement to ensure that Office 365 users external to the network of one of my clients need a second factor of authentication when accessing Office 365 resources from outside the corporate network. The free Multi-Factor Authentication (MFA) feature of Office 365 will not distinguish between network location so we need to enable…
-
ADFS Adapter Issues With Upgrading MFA 6.3.1 to Version 7
Upgrading the ADFS Adapter is not straight forward, though the readme notes for the upgrade make no mention of issues! To upgrade MFA Server 6.3.1 to 7 (so you can remove .NET 2 as a requirement, as that goes out of support soon) then you need to download the MFA installer to each MFA server…
-
How To Change Your Office 365 App Password
If you are enabled for Multi-Factor Authentication (MFA) in Office 365 then you will need an App Password for some applications that do not support MFA. The user interface for creating a new App Password is well hidden in Office 365 (its not on the Password page for example). Post updated in 2016 to take…
-
Exchange OWA and Multi-Factor Authentication
This article is now out of date Multi-factor authentication (MFA), that is the need to have a username, password and something else to pass authentication is possible with on-premises servers using a service from Windows Azure and the Multi-Factor Authentication Server (an on-premises piece of software). The Multi-Factor Authentication Server intercepts login request to OWA,…
-
Windows RRAS VPN and Multi Factor Authentication
This blog post covers the steps to add Multi Factor Authentication (MFA) to Windows RRAS server. Once this is enabled, and you sign in with a user enabled for MFA in Azure Multi-Factor Authentication Server (an on-premises server) you are required to answer your phone before you can connect over the VPN. That is, you…