Category: exchange online
-

Blocking onmicrosoft.com Emails in Exchange Online Protection
There is a considerable uptick in emails from the default domain in Microsoft 365 tenants. These emails come from senders @ tenant.onmicrosoft.com and are not your tenant. Microsoft recently announced recipient external sender limits to reduce this, as the default is 10,000 recipients per day, but will get an additional restriction of no more than…
-

What Is “mx.microsoft”?
mx.microsoft is the new MX delivery domain for Exchange Online. For years now it has been mail.protection.outlook.com, but this domain will not work with the new DNSSEC extensions that Exchange Online will start to support. When you added a new domain (called a vanity domain) to Microsoft 365, it would show you the MX record…
-

Outlook Reactions – Unsubscribe and Resubscribe
You can “answer” and email in Outlook with a emoji, called a reaction. If you get a reaction in response to a message you will see the reaction in the message, via a notification on the “bell” icon on the top of the Outlook desktop window and in other places, and importantly for this blog…
-

Seamless Office 365 Message Encryption (OME) Never Works
Microsoft 365 Purview Message Encryption, previously known as OME (Office Message Encryption) and before that Microsoft Rights Management, allows you to share protected email with anyone on any device. Users can exchange protected messages with other Microsoft 365 organizations, as well as third-parties using Outlook.com, Gmail, and other email services. The feature is part of…
-

Post Tenant To Tenant Migration Calendaring Issues
When you perform a Microsoft 365 tenant to tenant (T2T) migration and run a migration that is either staged over some time or sometime after the migration has completed you cutover the domains from the old tenant to the new tenant (that is, you were doing a rebrand and the new tenant had a new…
-

Blocking More Obvious Phish – Attachment Filtering
One relatively easy way to block some categories of phishing email is to block the attachment type that is sent with some of these messages. For example, I have had a few of these recently: Hovering over the attachment I see the filename, and it ends .shtml. This attachment is for server-side HTML (SSI includes…
-

Exchange Hybrid Wizard – New Tenants and Missing Errors
Rumoured to be fixed end of June 2023 A short blog post on this issue – you see in the Microsoft Exchange Server Hybrid Configuration Wizard logs the following error “Connecting to remote server failed with the following error message: Connecting to remote server outlook.office365.com failed with the following error message : For more information,…
-

Managing Hybrid Exchange Online Without Installing an Exchange Server
In April 2022 Microsoft finally released the ability to manage Active Directory synced attributes (Hybrid Identity) to Azure Active Directory for Exchange without a full Exchange Server installation. Instead, you install the Exchange Management Tools (EMT). You need to install Exchange Server 2019 CU12 or later to do this, and you either uninstall your existing…
-
Conditional Access in Defender for Cloud (MCAS)
I was asked this question last week at Microsoft Ignite following a talk that I did, and as it was a question it was clearly not as clear cut as maybe I thought it was. The question was, “why is Conditional Access found in Azure AD and Defender for Cloud?” (Defender for Cloud was previously…
-
Getting Teams Meetings Added to Your Events When Using Apple iOS Calendar App
A user can enable an “All Meetings Online” option in Outlook (all versions) to add a Teams meeting automatically when the meeting is created and an admin can enable this centrally for all users with the PowerShell Set-OrganizationConfig -OnlineMeetingsByDefaultEnabled $true But this does not add the meeting bridge to events created in Apple Calendar on…
-
Improving Exchange Online Email Deliverability Through Third Party Filtering Services – Trusted ARC Sealer
When you receive emails into Exchange Online and you filter the external messages before arrival with a third party filter such as Mimecast, Proofpoint or others, then you can have DMARC failures that result in messages being junked or quarantined in Exchange Online. Trusted ARC Sealer is a feature of Exchange Online to allow you…
-
Gmail showing “via” in Microsoft 365 Email Headers
I came across this issue the other day. In the headers of an email received from Microsoft 365 / Exchange Online into Gmail (and not other recipients) the message header reads “name@domain via otherdomain.onmicrosoft.com”, for example: In this case the via header for onmicrosoft.com was an old organization name and as tenant rename does not…
-
Finding Existing Plus Addresses
Exchange Online will automatically enable “Plus Addressing” for all tenants from Jan 2022. This change may cause issues if you have existing mailboxes where the SMTP address contains a + sign. That is, directors+managers@contoso.com would be considered a broken email address from Jan 2022 in Exchange Online. So you need to check you have no…
-

Outlook AutoDetect And Broken AutoDiscover
Those in the Exchange Server space for a number of years know all about AutoDiscover and the many ways it can be configured and misconfigured – if even configured at all. Often misconfiguration is to do with certificates or it is not configured at all because it involves certificates and I thought I was aware…
-
550 5.1.8 Access denied, bad outbound sender AS(42003)
“Your message couldn’t be delivered because you weren’t recognized as a valid sender. The most common reason for this is that your email address is suspected of sending spam and it’s no longer allowed to send email. Contact your email admin for assistance.” This is an error you get when your anti-spam “outbound” policy restricts…
-
[New] External Email Notification in Exchange Online
This is a new feature released in March 2021 that adds support in Outlook (Mac, OWA, Mobile) for the display of the external status of the sender – note at the time of writing it does not add this feature to Outlook for the PC. This should be used to replace the way this has…
-
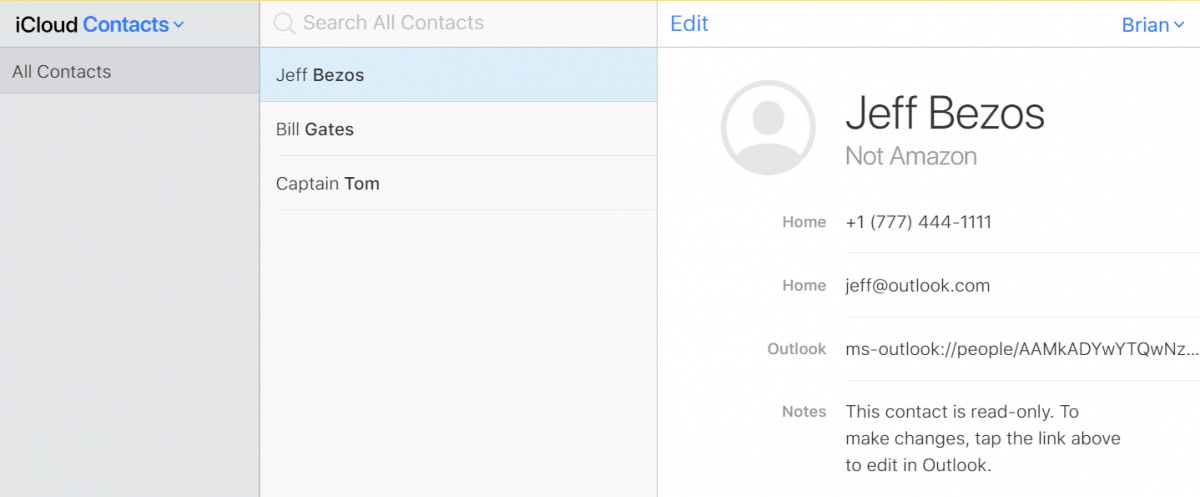
iOS and Outlook Mobile and Duplicate Contacts
Of the back of a few conversations recently on having duplicate contacts in the iOS platform because of syncing via multiple different routes or devices I decided to try to reproduce the issues and see what I could work out. I looked on my test iPhone to see if I could see any duplicates and…
-
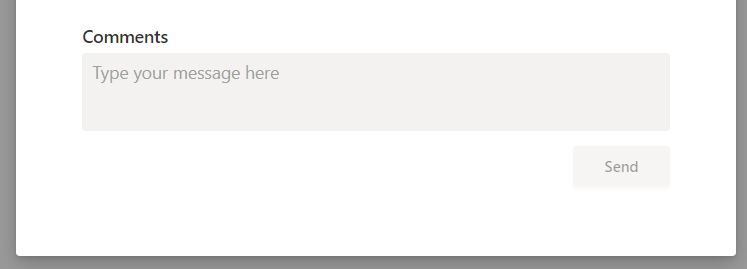
Why Do Comments In Microsoft 365 Planner Disappear?
So first you need an Exchange Online mailbox for comments to work. Comments to the tasks of Plans are stored in the Microsoft 365 Group mailbox, and you need an Exchange Online mailbox to access the M365 Group mailbox. Behind the scenes, or actually not that behind the scenes, the process for comments is as…
-
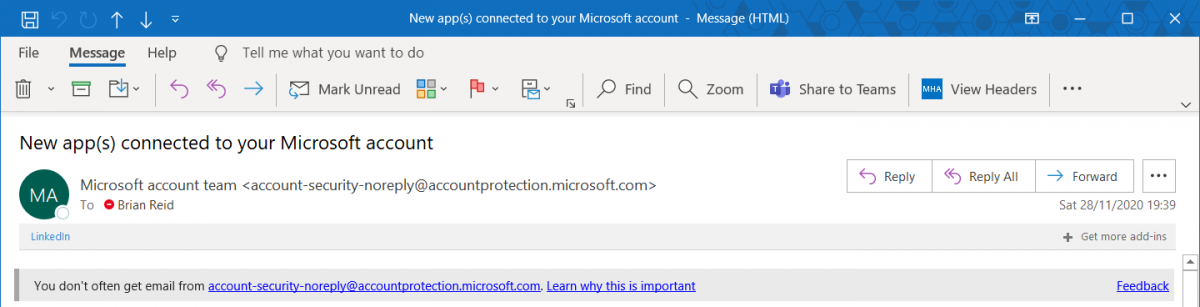
Exchange Online Warning On Receipt Of New Email Sender
Released recently to no fanfare at all, Microsoft now has a SafetyTip that appears if you receive email from a first time recipient. Most often phish emails will come from an address you have never received email from before, and sometimes this email will try to impersonate people you communicate with or are internal to…

