Category: Azure AD
-

Testing Entra ID Claims and Single Sign-On Enterprise Apps
There is a class of Enterprise App in Entra ID (previously known as Azure Active Directory) that provides SSO (Single Sign-On) for apps outside of Microsoft 365 provided by other vendors. Some of these will be very commonly used apps and others not so. For these apps to sign you into their application with your…
-

Windows LAPS and Granting Roles to Administrative Units
This blog post discusses how to create both a custom admin role for reading the LAPS password and settings stored in Entra ID and then assigning that role so that only device administrators of an Entra ID Administrative Unit can see the local admin password for the subset of devices they are able to manage.…
-

Inviting Google (Gmail) Users To Collaborate In Your Teams Channels
This post is not about inviting Google users to your meetings, where you just send them the meeting invite and all is good. This is about adding the Gmail user as a member of a Team, so they can see the Teams channels, chat and collaborate with files and apps along with everyone else in…
-

Is That Domain In Entra ID
Occasionally it is useful to know if a domain name is registered with a tenant in Entra ID (previously known as Azure AD). There is a URL to lookup this information as to my knowledge there is not easy portal to query. The URL requires you to add an email address, though the actual user…
-

Introduction to Microsoft Graph PowerShell SDK
This short blog post is the 10 minute demo I presented at Microsoft Ignite 2023 in Seattle. It was not recorded, but this was the slide deck that went with it. Graph SDK Additional Content.pptx The full speaking text of the presentation might be added here once the jetlag goes away!
-

Bulk Token Retrieval Failed
The Windows Configuration Designer (WCD) application (installed from the Microsoft Store) allows you to bulk convert standalone Windows 10+ clients to Azure AD Joined clients, and if you have Intune auto-enroll enabled then the client will enrol with Intune as well. But there are a number of issues with this application that result in errors…
-

Entra ID and Parental Consent
For organizations that store the data of young adults and children, and in some legal regions, adults who cannot consent to their own legal affairs, you need to record the Age Group for the user, along with any Consent Provided in the case of Minors. There are three categories of Age Group in Entra ID…
-

Migrating from AADConnect Sync to Entra Connect Cloud Sync Correctly
At the time of writing this blog post, the Microsoft guide for doing an AADConnect to Entra ID Cloud Sync migration is lacking quite a lot of detail. It contains the sum of two self referencing documents, one of which is a guide to doing the migration in a lab environment and the other is…
-
Domain Tenant Move and Device Join Issues
I discovered recently an issue following a tenant to tenant Microsoft 365/Azure AD migration. The issue was that devices would not enroll with Intune in the old tenant because the settings the device was getting was mixed up between the old and new tenants. In the case I had, the new tenant was not yet…
-

Adobe Creative Cloud and Conditional Access Restrictions
In Azure Active Directory it is possible to create Conditional Access rules that restrict applications to only running on company owned or managed devices. Conditional Access approves or rejects the login based on that knowledge – so what happens if the app in question is running on a company (managed or compliant) machine, but the…
-

Migrating MFA Settings To Authentication Methods
Released to Azure AD in December 2022 there is now a process for migrating from the legacy MFA methods and Self-Service Password Reset (SSPR) authentication methods to the unified Authentication Methods policies in Azure AD. This migration window is open until Jan 2024 when the legacy methods will be disabled. This change will allow you…
-
Conditional Access Authentication Strengths
Newly released to Conditional Access in Azure AD is the “Authentication Strengths” settings. These allow you to control the strength of the authentication you need to be used for that conditional access rule. Before this feature was available you had the option of allowing access with no second factor, MFA as a second factor (any…
-
Improving Security For MFA Approvals – Number Matching
Rolling out in November 2021 is a new feature – that of requiring the user to enter a number rather than just click approve on the MFA prompt. This update to Azure AD requires the use of Push Notifications and therefore requires the use of the Microsoft Authenticator app. It also requires that MFA is…
-
Adding Location To Azure AD MFA
This Azure AD feature is something that a number of other Multi-Factor Authentication providers have already implemented – that of showing the location of the user login (and the app in use) on the MFA prompt. This feature rolled out to Azure AD in mid November 2021 in preview – so use in non-production tenants…
-
MFA, Admin Roles and AADConnect Sync Failures
Come Feb 29th 2020 and Microsoft are turning off the baseline security policies. If you used these policies to do MFA for all admins (as that was an easy way to achieve this), then a replacement Conditional Access rule might cause errors with AADConnect. The reason being is that you could create a new Conditional…
-
Blocking Apps With a Low Reputation
One of the benefits of Microsoft 365 is the interaction across many products and features to create services that otherwise you might not have available to you or need to implement unrelated and unconnected additional software and maybe client agents as well. Recently announced is an interaction between Windows Defender (client AV and other security…
-
Baseline Policy Replacements: Conditional Access MFA for Administrators
From Feb 29th 2020 Microsoft will remove the “baseline policies” from Azure AD. These were very useful in the past to enable blanket settings like MFA for all admin accounts (well, selected admin roles) and to disable legacy auth for the same admin roles. With the removal of the baseline policies you need to ensure…
-
MFA and End User Impacts
This article will look at the various different MFA settings found in Azure AD (which controls MFA for Office 365 and other SaaS services) and how those decisions impact users. There is lots on the internet on enabling MFA, and lots on what that looks like for the user – but nothing I could see…
-
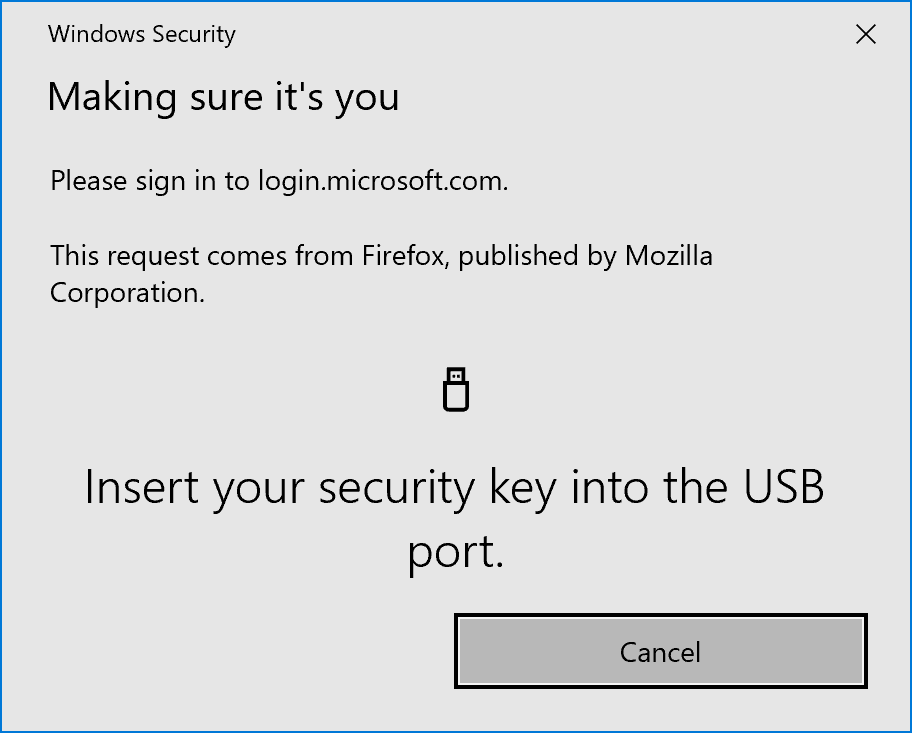
Getting Rid of Passwords in Azure AD / Office 365
This article is based on the public preview of the use of hardware tokens/Microsoft Authenticator to do sign-in without passwords released in July 2019 Using Microsoft Authenticator for Passwordless Sign-in You used to be able to do this by running the following in PowerShell for the last few years New-AzureADPolicy -Type AuthenticatorAppSignInPolicy -Definition ‘{“AuthenticatorAppSignInPolicy”:{“Enabled”:true}}’ -isOrganizationDefault…